RT @AnomalRoil: As presented today @defcon, we are super happy to be releasing the first practical, highly available timelock encryption sy…
Sun Oct 02 18:30:49 +0000 2022
RT @matthew_d_green: The dark side of building a massive (and poorly secured) personal data-collection infrastructure in the West: even if…
Sun Oct 02 18:40:26 +0000 2022
RT @stealthygeek: Yesterday, in broad daylight, our home was SWATTed by the @MilwaukeePolice for the 6TH TIME!
And unlike the 5th time whi…
Sun Oct 02 22:49:05 +0000 2022
👍👏 https://twitter.com/mer__edith/status/1576596971099664384
Sun Oct 02 23:09:14 +0000 2022
Replying to @trbouma
I have that set, from my dad. Still hope to read it someday.
Sun Oct 02 23:10:55 +0000 2022
RT @ssi_karim: I can’t wait to see the results of last week. Thanks to the @RWOTEvents team and everyone that participated, I had a blast!
Tue Oct 04 15:06:22 +0000 2022
RT @EssifL: Last 26-30 September eSSIF-Lab project was presented at the Rebooting Web of Trust (#RWOT11) event in The Hague (Netherlands)…
Wed Oct 05 01:28:38 +0000 2022
RT @privacylawyer: To me, privacy is all about autonomy, dignity and individual control. So a provision that would permit the privacy commi…
Wed Oct 05 02:00:55 +0000 2022
Replying to @ethotim
I’ve heard that some cryptographers have reservations about by Gennaro & Goldfeder ECDSA thresholds, such as https://info.fireblocks.com/hubfs/A_Note_on_the_Security_of_GG.pdf — what are your opinions? We’re currently investigating moving from SSS to the VSS that is also used by FROST round one.
Wed Oct 05 19:20:29 +0000 2022
Replying to @ethotim
Yes, FROST uses Feldman. However, we need one based on secp256k1, as we desire be compatible with code this PR at https://github.com/ElementsProject/secp256k1-zkp/pull/138. However, that being said, we need to do more as we’d like to use VSS independently from FROST to be a upgrade for SSS in our SSKR spec.
Thu Oct 06 18:25:04 +0000 2022
RT @ethotim: @ChristopherA Thanks for sharing this report, have to read it to get the context. In general, GG20 scheme is broadly considere…
Thu Oct 06 18:25:44 +0000 2022
Gordian Envelope is part of our Collaborative Seed Recovery (CSR) program, which will make it easy and accessible to securely store and reconstruct your cryptographic seeds, and supports all blockchains & other technologies that leverage seeds. [4/9] https://github.com/BlockchainCommons/Gordian/blob/master/Docs/CSR.md
Thu Oct 06 18:49:55 +0000 2022
And we’re now building that foundation for more than just the cryptocurrency community, as we’re doing our first work with the decentralized identity community courtesy of our sustaining sponsor @Proxy. [3/9]
Thu Oct 06 18:49:55 +0000 2022
Blockchain Commons returns to one of its fundamental goals, building a firmer foundation for digital assets and decentralized identity wallets, with a new specification: Gordian Envelope. [2/9] https://youtu.be/tQ9SPek0mnI
Thu Oct 06 18:49:55 +0000 2022
Our latest quarterly report from @BlockchainComns is out, with details on our 2nd #SiliconSalon, Gordian Envelope & Private Key Disclosure Advocacy. We work with developer communities to design, build, and maintain secure & compassionate decentralized architecture & tools:🧵[1/9] https://twitter.com/BlockchainComns/status/1578068815610408960
Thu Oct 06 18:49:55 +0000 2022
For the details on this work and even more, see the full quarterly report! [8/9] https://www.blockchaincommons.com/quarterlies/Q3-2022/
Thu Oct 06 18:49:56 +0000 2022
Finally, it was great to see #RebootingWebOfTrust @RWOTEvents back! We submitted an advance reading on the elision, redaction, and noncorrelation properties of Gordian Envelope, and was selected for a full RWOT white paper on “Selective Correlation”! [7/9] https://github.com/WebOfTrustInfo/rwot11-the-hague/blob/master/advance-readings/elision-redaction-correlation-smart-documents.md
Thu Oct 06 18:49:56 +0000 2022
Our advocacy also continues with a defense of private keys. I’ve been working with the Wyoming legisulature on this topic and also authored an article about it that was picked up by Bitcoin magazine. [6/9] https://bitcoinmagazine.com/legal/saving-bitcoin-private-keys-from-courts
Thu Oct 06 18:49:56 +0000 2022
The other big Blockchain Commons event in the last quarter was Silicon Salon 2, where we’re continuing to work with semiconductor manufacturers and wallet developers to create the next generation of crypto-silicon. [5/9] https://www.siliconsalon.info/salon2/
Thu Oct 06 18:49:56 +0000 2022
If creating stronger foundations for decentralized wallet security, interoperability, and human-rights privacy work is important to you, and if you’d like to work with us to expand it, please become a Blockchain Commons sponsor: https://github.com/sponsors/BlockchainCommons. [9/9]
Thu Oct 06 18:49:57 +0000 2022
Replying to @ethotim
BTW, details on our SSKR specs: https://github.com/blockchaincommons/crypto-commons#sskr
Thu Oct 06 19:08:46 +0000 2022
Replying to @ethotim
…and our current Q4 priority, Collaborative Seed Recovery https://twitter.com/ChristopherA/status/1578095224890396673?s=20&t=HGAqSdIApYUBQYXXfVWMGg
Thu Oct 06 19:10:16 +0000 2022
A challenge in @BlockchainComns & @RWOTEvents is that we need a grant manager to keep up with tech grant opportunities, applications, reports, etc. But we are two small to hire one full time. If you know of someone that would be interested in a day a week paid role let me know.
Thu Oct 06 19:21:24 +0000 2022
Replying to @ethotim
The underlying SSS is the same (they participated in our @RWOTEvents discussions in Barcelona & Prague). However, they don’t round-trip with BIP39, and we do so we each forked. (long story). We have our own mnemonics, bytewords, which work better with QRs https://github.com/BlockchainCommons/Research/blob/master/papers/bcr-2020-012-bytewords.md
Thu Oct 06 19:24:36 +0000 2022
Replying to @ethotim and @RWOTEvents
For more details on why we diverged SSKR from SLIP-39, see: https://github.com/BlockchainCommons/Research/blob/master/papers/bcr-2020-011-sskr.md#%EF%B8%8F-incompatible-with-slip-39
Thu Oct 06 19:26:40 +0000 2022
Replying to @ethotim and @RWOTEvents
Also relevant as we move from SSKR to also support VSS is this security review of SSKR: https://github.com/BlockchainCommons/bc-sskr/blob/master/SECURITY-REVIEW.md
Thu Oct 06 19:29:30 +0000 2022
Replying to @ethotim and @RWOTEvents
There are some choices we made in SSKR (that SLIP-39 also has) that allow for some correlation, that we also need to revisit as we move to VSS: See in our non-correlation section of our draft envelopes spec: https://github.com/BlockchainCommons/BCSwiftSecureComponents/blob/6600fecf1120cacfe0737659c0671ecfed72dbd6/Docs/07-NONCORRELATION.md#sskrshares-are-correlatable
Thu Oct 06 19:35:16 +0000 2022
Replying to @ethotim and @RWOTEvents
In SSKR “The session ID is a check on foreign shares being introduced into the recovery process, and removing the session ID would make it impossible for an SSKR decoder to reject a share interactively”. Using VSS could address this.
Thu Oct 06 19:36:43 +0000 2022
GrapheneOS is a privacy focused fork of Android. Worthy of support. https://twitter.com/GrapheneOS/status/1578073223316619271
Fri Oct 07 03:39:17 +0000 2022
Gordian Envelopes are built upon semantic triples, such as “Alice Knows Bob”. Each of these elements can itself be an envelope: it’s envelopes all the way down. [3/12] https://en.wikipedia.org/wiki/Semantic_triple
Wed Oct 12 19:07:22 +0000 2022
You can alternatively read an annotated transcript of the video, which includes all the command-line examples. [2/12] https://github.com/BlockchainCommons/envelope-cli-swift/blob/master/Transcripts/1-OVERVIEW-TRANSCRIPT.md
Wed Oct 12 19:07:22 +0000 2022
An overview of Blockchain Commons’ new envelope-cli is now available. Envelopes are a new type of “smart document” to support the storage, backup, encryption & authentication of data, with explicit support for Merkle-based selective disclosure.🧵[1/12] https://www.youtube.com/watch?v=K2gFTyjbiYk
Wed Oct 12 19:07:22 +0000 2022
If elision is not a desirable property, you can instead add salt to your envelope to change its digest and make it non-correlatable. [7/12] https://en.wikipedia.org/wiki/Salt_(cryptography)
Wed Oct 12 19:07:23 +0000 2022
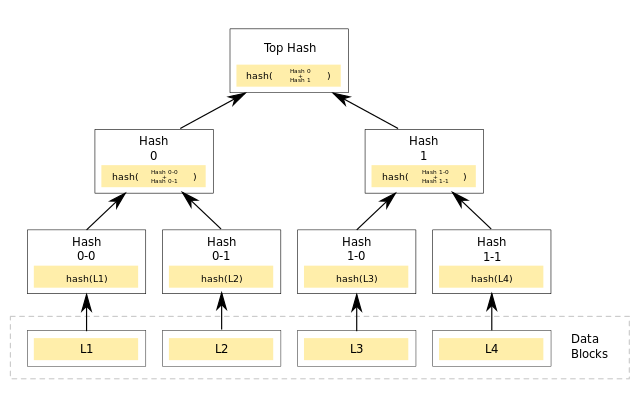
Finally, digests allow you to validate an envelope. Digests for individual elements in an Envelope’s Merkle tree remain the same, as does the overall digest, even when those elements are elided! So Envelope contains selective disclosure, including hash inclusion proofs! [6/12]
Wed Oct 12 19:07:23 +0000 2022
But there’s more! Elision allows you to redact some of the contents of an envelope, so that you only reveal what you want! [5/12] https://github.com/WebOfTrustInfo/rwot11-the-hague/blob/master/advance-readings/elision-redaction-correlation-smart-documents.md
Wed Oct 12 19:07:23 +0000 2022
Many of the core features of Envelope are demonstrated in the video. Encryption allows you to protect the contents of an envelope. Signing allows your recipients to verify it. Sharding allows you to safely back it up using Shamir’s Secret Sharing. [4/12] https://www.youtube.com/watch?v=K2gFTyjbiYk
Wed Oct 12 19:07:23 +0000 2022
For a deeper dive into Gordian Envelopes, with more examples, exploration of its features such as elision/redaction, existence proofs, and overview of use cases such as credentials & distributed identifiers, see the full playlist of videos. [10/12] https://www.youtube.com/watch?v=tQ9SPek0mnI&list=PLCkrqxOY1FbooYwJ7ZhpJ_QQk8Az1aCnG
Wed Oct 12 19:07:24 +0000 2022
Our envelope-cli app is intended as a reference for developers, and currently only works on macOS. But we plan to port to more languages & OSes. You can try it out for yourself by pulling the repo and building it with Xcode. [9/12] https://github.com/BlockchainCommons/envelope-cli-swift
Wed Oct 12 19:07:24 +0000 2022
None of this is theoretical. The
envelope-cliapp shows a fully functional example of how Gordian Envelope works! We’re also now working with partners to deploy it for use with secret protection, credential sharing, and other requirements. [8/12] https://github.com/BlockchainCommons/envelope-cli-swift
Wed Oct 12 19:07:24 +0000 2022
Support @BlockchainComns so that we can continue to develop our Gordian architectures, including Gordian Envelope. You can sponsor us by becoming a Blockchain Commons patron on GitHub. [12/12] https://github.com/sponsors/BlockchainCommons
Wed Oct 12 19:07:25 +0000 2022
Be part of the developer discussions about Gordian Envelope! Email us at team@blockchaincommons.com or join our Developer Discussions on Envelope. [11/12] https://github.com/BlockchainCommons/Gordian-Developer-Community/discussions/100
Wed Oct 12 19:07:25 +0000 2022
Replying to @AndyPerfors
Cooperative design is part of motivates the approach we take with our #RebootingWebOfTrust events. No sages on stages, less talk, more collaboration. A primer on how it works: https://github.com/WebOfTrustInfo/rwot11-the-hague/blob/master/advance-readings/rwot-primer.md
Thu Oct 13 04:01:17 +0000 2022
The ability of a holder to elide content is important because other credential systems (such as VCs) limit that capability to the issuer. That’s very restrictive if you have to go out to the issuer every time you want a version of a credential that doesn’t reveal too much! [2/10]
Fri Oct 14 15:36:03 +0000 2022
One of the most useful attributes of the Gordian Envelope is its elision capability: a holder can redact any contents of an Envelope without harming the ability to verify signatures. A new @BlockchainComns video depicts this process in detail. 🧵[1/10] https://www.youtube.com/watch?v=3G70mUYQB18
Fri Oct 14 15:36:03 +0000 2022
Elision in envelopes can not only target the release of specific information but also can allow adding a signature to the elided Envelope as a warranty, as shown in the video. Try it out yourself with envelope-cli for Mac! [6/10] https://github.com/BlockchainCommons/envelope-cli-swift
Fri Oct 14 15:36:04 +0000 2022
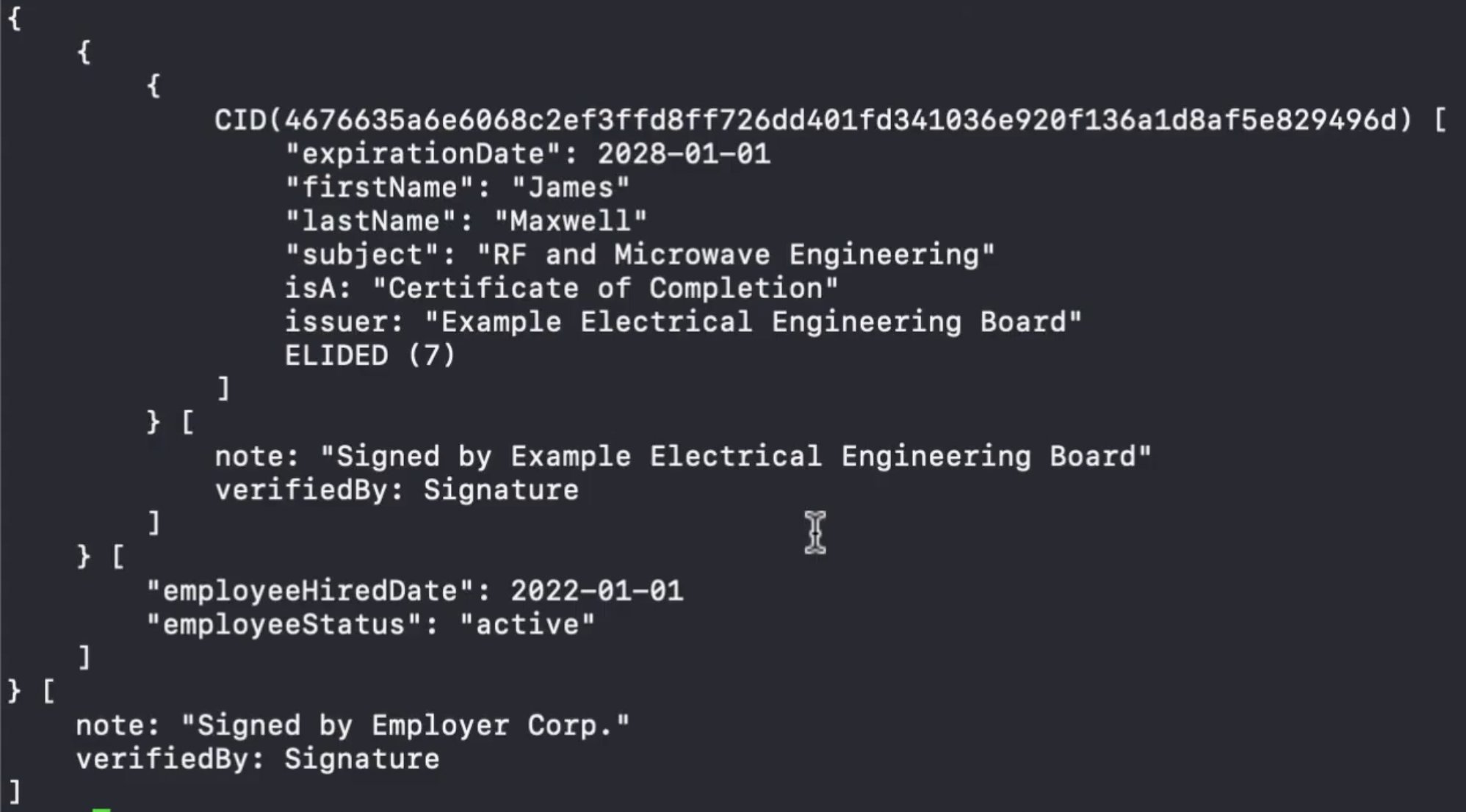
The electrician’s employer wants to warrant to a third-party that they have a credentialed electrician on staff, but it’s not appropriate for them to send all of his information, as the Envelope includes things like his photograph and ID #. That’s where elision comes in. [5/10]
Fri Oct 14 15:36:04 +0000 2022
The @BlockchainComns video offers a comprehensive example of an electrician with a skills credential signed by the local electricity board. [4/10] https://www.youtube.com/watch?v=3G70mUYQB18
Fri Oct 14 15:36:04 +0000 2022
As for elision, that’s important because you may have Envelopes that contain a wide variety of different information, such as an educational credential. You may have Envelopes where information is appropriate for one group but not another. That’s why you want to redact. [3/10]
Fri Oct 14 15:36:04 +0000 2022
Join our developer community if you are looking to offer more privacy when sharing digital data. Envelopes also offer important features for your own cryptographic data or digital identity work! [9/10] https://github.com/BlockchainCommons/Gordian-Developer-Community/discussions
Fri Oct 14 15:36:05 +0000 2022
You can also examine all of the Elision examples in our Elision Examples text file. [8/10] https://github.com/BlockchainCommons/envelope-cli-swift/blob/master/Docs/7-VC-ELISION-EXAMPLE.md
Fri Oct 14 15:36:05 +0000 2022
Using the Envelope-CLI App, you can follow along with all the examples in the video. [7/10] https://www.youtube.com/watch?v=3G70mUYQB18
Fri Oct 14 15:36:05 +0000 2022
Support @BlockchainComns by becoming a GitHub patron to ensure that this important, foundational work for digital privacy on the internet continues. [10/10] https://github.com/sponsors/BlockchainCommons
Fri Oct 14 15:36:06 +0000 2022
Existence proofs instead allow a verifier to ask for proof of a specific credential (or other data), and then to verify that proof against an elided version of an Envelope! (Salts prevent other assertions from being guessed) [4/11]
Mon Oct 17 17:00:58 +0000 2022
There is already support for elision in Gordian Envelope: the issuer or any holder can redact any element of an Envelope before providing it to a requester. [3/11] https://github.com/BlockchainCommons/BCSwiftSecureComponents/blob/master/Docs/08-ELISION-REDACTION.md
Mon Oct 17 17:00:58 +0000 2022
Gordian Envelope is a new type of “smart document” that supports the storage, backup, encryption & authentication of data. But what if you only want to prove a specific bit of data? That’s where Merkle-based selective correlation comes in. [2/11] https://www.youtube.com/watch?v=tQ9SPek0mnI
Mon Oct 17 17:00:58 +0000 2022
Existence Proofs are one of the many powerful tools available in our new Gordian Envelope architecture for cryptographic documents. Our newest video explains how this feature is supported by Gordian Envelope to enable “selective correlation”. 🧵[1/11] https://www.youtube.com/watch?v=LUQ-n9EZa0U
Mon Oct 17 17:00:58 +0000 2022
Another opportunity is for a large group of people to share a single DID, each contributing a smaller hash tree to the whole, and only offering existence proofs for their own portion. Both these techniques enable “herd privacy”. [8/11]
Mon Oct 17 17:00:59 +0000 2022
Existence proofs in Gordian Envelope allow for some very interesting new opportunities for safer credentials and DIDs. For instance, a school could offer a single large credential for a graduating class, where students prove their own details within that larger class. [7/11]
Mon Oct 17 17:00:59 +0000 2022
You can also dig into Existence Proofs by working along with the examples using the envelope-cli example directly. (This all already works!) [6/11] https://github.com/BlockchainCommons/envelope-cli-swift/blob/master/Docs/8-EXISTENCE-PROOFS.md
Mon Oct 17 17:00:59 +0000 2022
Want to verify the relation between two entities? Want to check an identifier? Want to confirm multiple facts simultaneously? The examples in our newest video show them all. [5/11] https://www.youtube.com/watch?v=tQ9SPek0mnI
Mon Oct 17 17:00:59 +0000 2022
Support this and our other digital identity & cryptocurrency wallet specs to ensure future wallet security and interoperability! Become a Blockchain Commons Patron on GitHub! [11/11] https://github.com/sponsors/BlockchainCommons
Mon Oct 17 17:01:00 +0000 2022
Developers interested in the topic should join us in our Developer Community discussions, or else mail us at team@blockchaincommons.com. [10/11] https://github.com/BlockchainCommons/Gordian-Developer-Community/discussions
Mon Oct 17 17:01:00 +0000 2022
This is just part of the power of Gordian Envelopes. These smart documents allow for the storage of secrets, the inclusion of metadata, the ability to access them with different permits, and the creation of DID docs. We’ve got examples of those too. [9/11] https://github.com/BlockchainCommons/envelope-cli-swift/tree/master/Docs
Mon Oct 17 17:01:00 +0000 2022
I’m intrigued by the design space offered by verifiable time-lock encryption. These leverage trusted randomness oracles that operate as MPC federations (to prevent single points of failure or collusion) such #LeagueOfEntropy. This 🧵shows some of the performance tradeoffs. https://twitter.com/timoethey/status/1582013471935254528
Mon Oct 17 17:28:38 +0000 2022
RT @gimly_io: This is why @casparroelofs joined @kudrixD, @tlodderstedt, @mirkomollik, Maaike van Leuken & Paul Bastiana during the last #R…
Sat Oct 22 23:55:28 +0000 2022
RT @gimly_io: To learn more about this effort and to start contributing, have a look at the credential profiles comparison matrix and read…
Sat Oct 22 23:55:39 +0000 2022
RT @gimly_io: Self-sovereign identity experts, techies, implementors, designers and regulators - we need to improve our collective understa…
Sat Oct 22 23:56:04 +0000 2022
RT @GalaxyKate: declaring a new term:
A Bach Faucet is a situation where a generative system makes an endless supply of some content at or…
Sun Oct 23 17:20:50 +0000 2022
Replying to @darrello, @OR13b and @TheKaryl
I think our @BlockchainComns dev community will be offering a DID, but use minimal disclosure existence proofs & progressive trust mechanisms instead of VCs. See “Gordian Envelope CLI - 5 - Existence Proofs”
https://youtu.be/LUQ-n9EZa0U
Tue Oct 25 23:58:23 +0000 2022
Replying to @darrello, @OR13b, @TheKaryl and @BlockchainComns
For a easier overview see the first two videos in this playlist https://youtube.com/playlist?list=PLCkrqxOY1FbooYwJ7ZhpJ_QQk8Az1aCnG
Wed Oct 26 00:01:24 +0000 2022
Replying to @darrello, @OR13b, @TheKaryl and @BlockchainComns
Or if you don’t like videos: https://github.com/BlockchainCommons/envelope-cli-swift/blob/master/Transcripts/1-OVERVIEW-TRANSCRIPT.md
Wed Oct 26 00:03:03 +0000 2022
Replying to @doerkadrian
Wyoming SF0039: “xviii) “Personal digital identity” means the intangible digital representation of, by and for a natural person, over which he has principal authority and through which he intentionally communicates or acts.”
Wed Oct 26 00:17:35 +0000 2022
Replying to @doerkadrian
https://www.blockchaincommons.com/articles/Principal-Authority/
Wed Oct 26 00:18:04 +0000 2022
Replying to @doerkadrian
The law does not say “exclusive control”. If something has been stolen from you, it is still yours. If your authority has been violated, it is still yours. You can seek redress for both. As far as shadow profile the “of” part of the law covers that. Law isn’t perfect but better.
Wed Oct 26 14:49:28 +0000 2022
This came up again today as a zk-proof technique for #LocationPrivacy that works with the well-studied & deployed integer bulletproofs. https://twitter.com/ChristopherA/status/1243413128378892293
Wed Oct 26 21:05:41 +0000 2022
Replying to @TelegramSam
I’d be interested in your thoughts on where elision & proofs of inclusion fall into your list: https://youtube.com/playlist?list=PLCkrqxOY1FbooYwJ7ZhpJ_QQk8Az1aCnG
Thu Oct 27 05:38:12 +0000 2022
Replying to @TelegramSam
Or see transcripts https://github.com/BlockchainCommons/envelope-cli-swift/blob/master/Transcripts/1-OVERVIEW-TRANSCRIPT.md & https://github.com/BlockchainCommons/envelope-cli-swift/blob/master/Transcripts/5-EXISTENCE-PROOFS-TRANSCRIPT.md
Thu Oct 27 05:40:07 +0000 2022
Replying to @TruvityHQ
I’m the author of the foundational paper & the 10 SSI principles. However, I don’t solely tweet about #SSI.
Thu Oct 27 16:40:35 +0000 2022
Replying to @TelegramSam
We are working on a high-level overview document now. Early draft at https://hackmd.io/CcsiXod9RLSQ8VsLYeu9Ig?view — when finished next week we’ll move to github.
Thu Oct 27 17:56:22 +0000 2022
RT @ViktorDefi: Just found another great resource.
👉 Learning Bitcoin from the Command Line:
A complete course for learning Bitcoin prog…