Replying to @durumcrustulum
Beautiful photo. Mars is in conjunction tonight, hiding in there next to Venus, which is 190x brighter tonight and 1/2 a degree away. I was not able to spot Mars with the naked eye.
Tue Jul 13 07:23:07 +0000 2021
I like these tiers of trust: can delegate a task, next can handle a process, then you trust that they will follow your intent. This feels related to my 2004 blog post about Progressive Trust, but also connects new laws about delegation & authority I’m working on in Wyoming. https://twitter.com/rdonoghue/status/1414561256883769346
Wed Jul 14 03:54:02 +0000 2021
Link to my old blog post on Progressive Trust: http://www.lifewithalacrity.com/2004/08/progressive_tru.html
Wed Jul 14 03:54:03 +0000 2021
Replying to @usablelearning
Yes, Julie, your are correct, it does also seem to be related to the Proficiency Ladder that I later wrote up as a presentation at https://www.slideshare.net/ChristopherA/the-proficiency-ladder I’d be interested in your thoughts.
Wed Jul 14 05:42:35 +0000 2021
Replying to @usablelearning
I’m not teaching in academia anymore, but I’ve got a dozen interns this summer as part of a @HRF grant where we are working on projects related to digital human rights, privacy tech, etc. And of course we are talking about trust there as well.
Wed Jul 14 05:45:16 +0000 2021
🕵🏻♂️”We implement…auditable MPC construction…with 32 MPC servers, over 1 million constraints, and 8 statement size, our prover time is about 678 seconds, auditing time less than 40ms, proof size is ≈ 1.5Kb, total MPC com overhead is a constant 700Kb with five additional rounds” https://twitter.com/socrates1024/status/1414990885981466635
Thu Jul 15 03:37:46 +0000 2021
Thu Jul 15 03:38:45 +0000 2021
This is the first of a number of new UR spec improvements related to crypto-request, which allows for networked services or desktop appsto request what they need from airgapped wallets controlling seeds. https://twitter.com/BlockchainComns/status/1415599872514748417
Thu Jul 15 09:13:33 +0000 2021
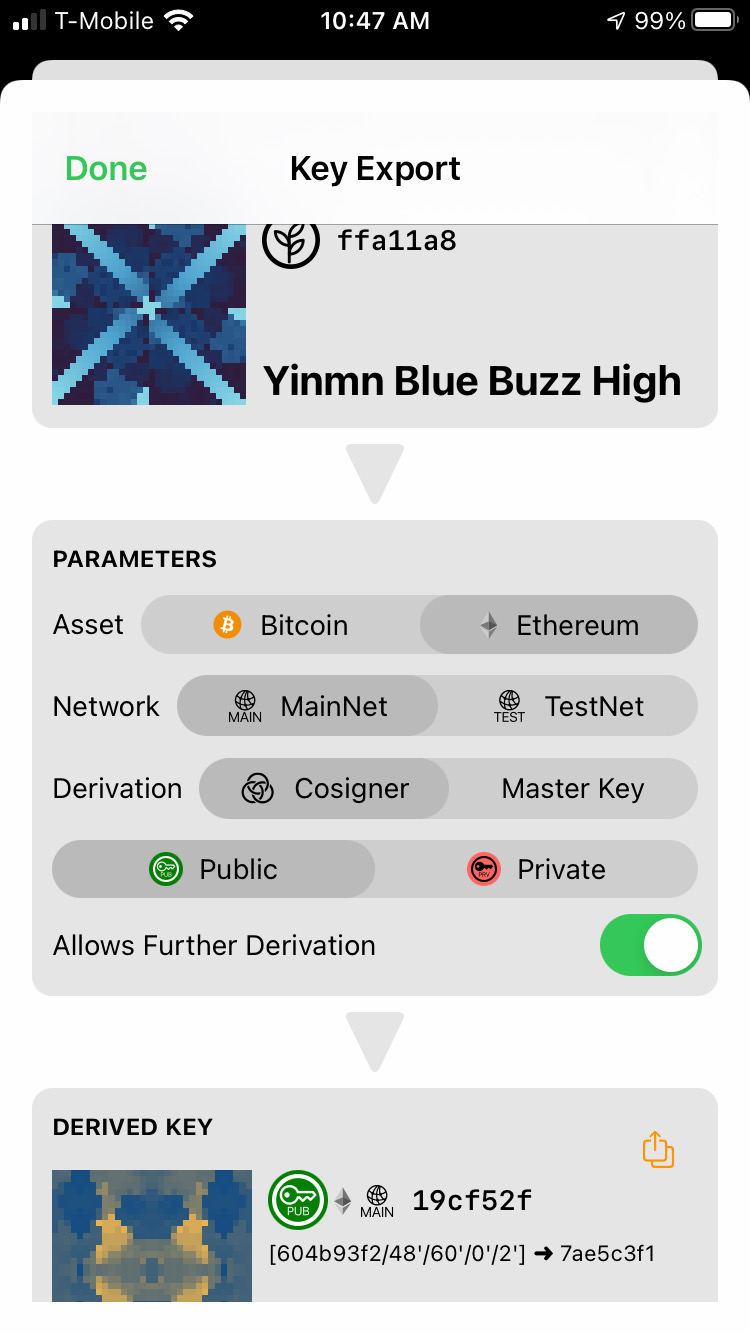
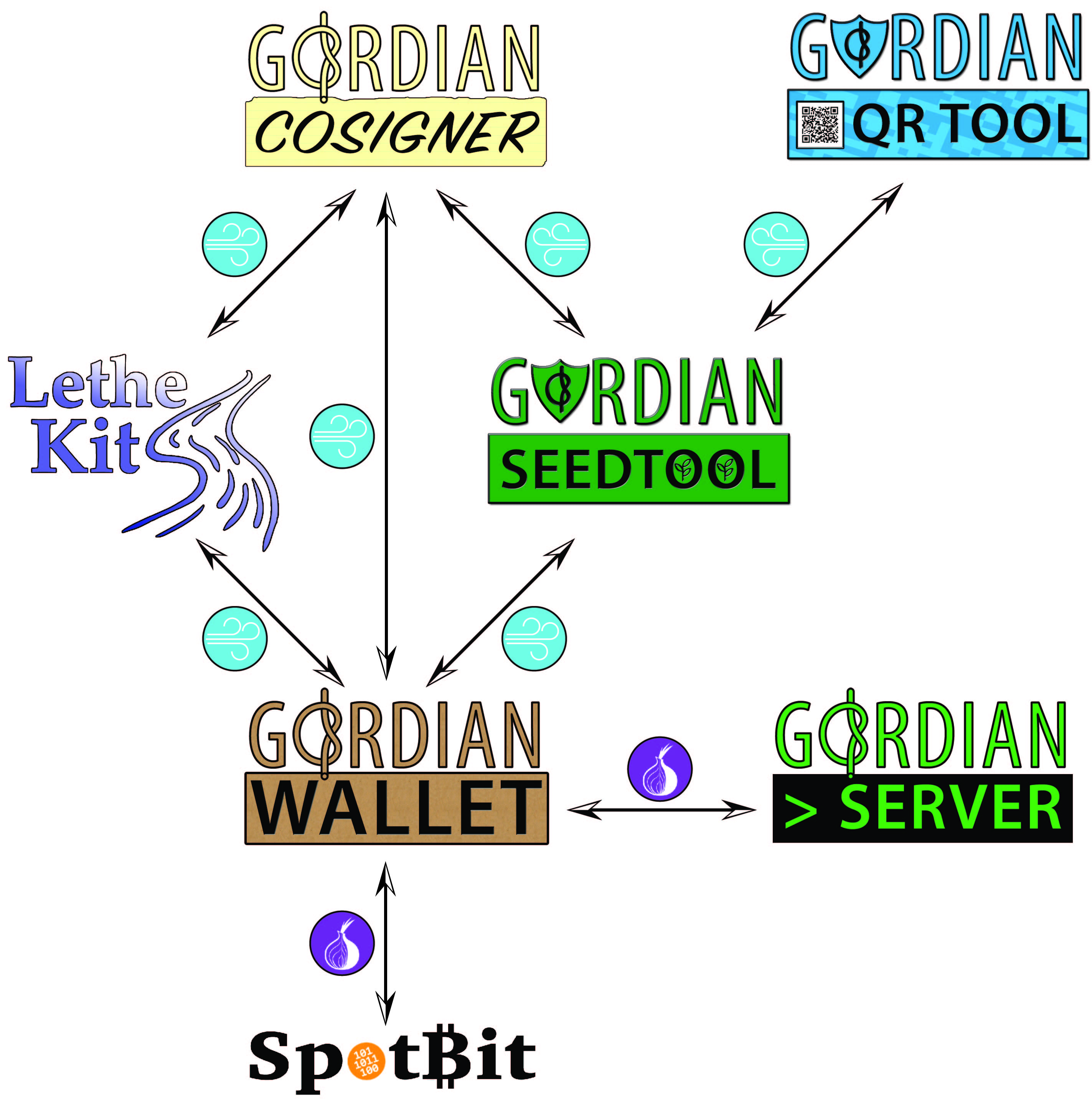
Gordian Seed Tool allows you to securely store your cryptographic seeds on your closely held mobile device, protecting them with Apple’s well-trusted encryption and your own biometrics. [2/11]
Thu Jul 15 19:57:26 +0000 2021
Blockchain Commons has recently released Gordian Seed Tool, our second reference app, available for iOS devices through the Apple App Store. [1/11] https://apps.apple.com/us/app/gordian-seed-tool/id1545088229
Thu Jul 15 19:57:26 +0000 2021
This builds on the core concept of airgaps. By separating your seeds from the network, you can depend on the physical and cryptographic security of your device, rather than using a porous, networked computer prone to network attacks. [3/11]
Thu Jul 15 19:57:27 +0000 2021
But how do you use your seeds? Seed Tool makes it easy. You can derive popular keys for Bitcoin or Ethereum, and then export those rather than your seed itself. In particular Seed Tool is useful for keys used in multisig.[4/11]
Thu Jul 15 19:57:28 +0000 2021
Seed Tool can even answer requests from other apps for specific derivations, creating a whole web of airgapped crypto-apps, all carefully partitioned and individually protected, to maximize your security. [5/11]
Thu Jul 15 19:57:29 +0000 2021
Seed Tool supplements its security with resilience. Your seeds are encrypted and backed up to iCloud, ensuring that if you lose your mobile device, you can recover your seeds — and our experience is that loss of this type is the biggest threat to your crypto holdings. [6/11]
Thu Jul 15 19:57:31 +0000 2021
Want to see more specifications and reference code and apps for creating wallet interoperability? You can support Blockchain Commons by becoming a patron! [11/11] https://github.com/sponsors/BlockchainCommons
Thu Jul 15 19:57:32 +0000 2021
Seed Tool is open source! If you are a wallet developer, join us in our Airgapped Wallet Community to talk about how to engineer the next generation of cryptocurrency wallets. [10/11] https://github.com/BlockchainCommons/Airgapped-Wallet-Community/discussions
Thu Jul 15 19:57:32 +0000 2021
Learn more about Gordian Seed Tool in our recent article on its release. [9/11] https://www.blockchaincommons.com/projects/SeedTool-Release/
Thu Jul 15 19:57:32 +0000 2021
Seed Tool was built using the Gordian Principles of independence, privacy, resilience, and openness. [8/11] https://github.com/BlockchainCommons/GordianSeedTool-iOS#gordian-principles
Thu Jul 15 19:57:32 +0000 2021
There’s a lot more to be said about Gordian Seed Tool. It can import and export using a variety of specifications, it will uniquely display your keys, and it can shard them. We invite you to take a look! [7/11] https://apps.apple.com/us/app/gordian-seed-tool/id1545088229
Thu Jul 15 19:57:32 +0000 2021
RT @Appelcline: Blockchain Commons, who I do tech writing for, just released its second reference app: Gordian Seed Tool.
The goal of thes…
Fri Jul 16 17:06:17 +0000 2021
RT @WolfMcNally: Very proud to work with @BlockchainComns in creating Gordian Seed Tool, a #SwiftUI app aimed at users of #cryptocurrencies…
Fri Jul 16 17:06:19 +0000 2021
I’m impressed by this concise summary (66 pages) of pragmatic cryptography and security. I say pragmatic because the author avoids modern (last decade) topics like quorum multisig, zk-proofs, mpc, etc. that I believe are not quite mature and have risk just because they are new. https://twitter.com/kennyog/status/1416429123031941121
Sat Jul 17 21:31:57 +0000 2021
This is an interesting new service from @rusty_twit of @Blockstream’s C-Lightning . I’ve been considering something similar from @BlockchainComns that leveraged our TorGap services, paid for with small number of satoshi using lightning, time stamped, and maybe signed. I will 🕵🏻♂️. https://twitter.com/rusty_twit/status/1416669667037368326
Sun Jul 18 20:17:59 +0000 2021
There are several uses for this type of service. In particular to my own concerns recently, unlike single signature wallets, to back up a descriptor-based wallets with sophisticated scripts such as multisig or time locks, you need also backup the descriptor or scripts.
Sun Jul 18 20:26:17 +0000 2021
My first thought was to allow the descriptor or minisig or other short metadata to be encrypted with a symmetric key derived from the master key. But which one? More recently I’ve been working on a CBOR based proposal where there are multiple ways to get that asymmetric key…
Sun Jul 18 20:29:26 +0000 2021
…through a header block we call the manifest, so that we can encrypt that symmetric key with EVERY xpub in the descriptor or minisig. Thus you can use asymmetric keys, sskr, or new approaches, all of which can reveal the symmetric key for decryption of the metadata needed.
Sun Jul 18 20:34:52 +0000 2021
We already have an experimental TorGap v3 open source repo that we offer, along with timestamping & ability for the onion address to countersign the data, so this metadata archive would be the another service on top.
Sun Jul 18 20:38:25 +0000 2021
We got stuck making some cryptographic choices, finalizing our manifest ideas for maximum future proofing, some CBOR UR perquisites, and puzzling through how to auction price this service with Lightning so anyone could offer it. @rusty_twit’s proposal is simpler, but centralized.
Sun Jul 18 20:41:25 +0000 2021
RT @ChristopherA: There are several uses for this type of service. In particular to my own concerns recently, unlike single signature walle…
Sun Jul 18 20:41:54 +0000 2021
This is our (@WolfMcNally & I) rough start on “An Envelope for Multi-Recipient Encryption of CBOR Objects” at https://hackmd.io/@Rc_qSIjeRK6KtnGbrOqz0w/Hk4uerfFd
Sun Jul 18 21:08:14 +0000 2021
A particular inspiration for a manifest of different permits was the MiniLock v2 format: https://45678.github.io/miniLock-file-format/2.html#decrypt_a_permit but we wanted to add other options than only asymmetric pub/prv keys to the mix, such as quorum of two-layer Shamir shards in SSKR, Verifiable Secret Sharing, etc.
Sun Jul 18 21:14:07 +0000 2021
Replying to @rusty_twit
what do you think of the encrypted payload be encrypted by a random symmetric key, but then encrypt that payload key from an array of keys corresponding to a specific derivativion + index for one or more of the xpubs? That is the most important difference from yours.
Mon Jul 19 00:21:01 +0000 2021
Replying to @rusty_twit
Have you seen SSKR yet? The reference implementation is in seedtool-cli & our iOS/Mac SeedTool. Our idea is that you could also encrypt the payload key using a key derived from the recovery of SSKR so you can also set that permit to allow social key recovery.
Mon Jul 19 00:26:02 +0000 2021
RT @Appelcline: Hats off to @AlexPreukschat and @drummondreed , for publishing our dreams of internet identity that is controlled by us (…
Mon Jul 19 22:47:07 +0000 2021
Note that this GPG vulnerability does not apply to Elliptic Curve keys. Time to us to revoke our older GPG keys, in particular RSA-based ones, and use more recent key generation best-practices. https://twitter.com/luca_defeo/status/1417409699884982294
Wed Jul 21 01:23:57 +0000 2021
Replying to @AlyssaHertig and @La__Cuen
We’ve started our second season of summer interns. Here is an article on last year’s program: https://www.google.com/amp/s/www.coindesk.com/blockchain-commons-interns-open-source-developers Many are not engineers, and help out with use cases, docs, etc. Others are junior or are taking on simpler code project. This year we received a grant from @HRF.
Fri Jul 23 04:58:06 +0000 2021
I am verifying my identity as christophera on @gitcoin https://gitcoin.co/christophera
Tue Jul 27 15:49:20 +0000 2021
@StupidFunWill if you have not seen this video yet, it was inspired by SimEarth. I remember with fondness our discussions about meteorites seeding continents, tricordates winning the Cambrian Explosion, or delphinoids winning the sapience race. Thank you! https://www.vice.com/en/article/xgx7nq/watch-four-billion-years-of-earths-evolution-in-four-minutes
Thu Jul 29 22:51:59 +0000 2021
Some of it was overview, such as our laying out our Gordian principles of independence, privacy, resilience, and openness and producing a new video, talking about all our technologies and specifications. [2/14] https://www.youtube.com/watch?v=RYgOFSdUqWY
Fri Jul 30 16:52:55 +0000 2021
Blockchain Commons has released its Q2 report talking about what we were doing this Spring … and there’s a lot! [1/14] https://www.blockchaincommons.com/quarterlies/Q2-2021-Report/
Fri Jul 30 16:52:55 +0000 2021
Gordian QR Tool similarly allows you to keep QR codes in a protected and backed up vault. Great for 2FA seeds, cryptocurrency seeds, Smart Health Certificates, and other QRs that need more security then your camera roll! [5/14] https://apps.apple.com/us/app/gordian-qr-tool/id1506851070
Fri Jul 30 16:52:56 +0000 2021
Gordian Seed Tool allows you protect and backup your seeds, and use them to derive keys. It also serves as a reference airgapped QR tool to demonstrate interoperability between wallets. [4/14] https://apps.apple.com/us/app/gordian-seed-tool/id1545088229
Fri Jul 30 16:52:56 +0000 2021
We’re also thrilled to have released our first two Gordian apps to the Apple App Store! [3/14]
Fri Jul 30 16:52:56 +0000 2021
Meanwhile, one of our sponsors is funding Blockchain Commons’ first formal security review, covering our SSKR libraries for sharding seeds. This is a critical step toward making them available for production blockchain releases. Thanks, @BitmarkInc! [9/14] https://bitmark.com/
Fri Jul 30 16:52:57 +0000 2021
Both Sweeptool and Mori represent a new focus on Rust programming language, which we think is also critical for the next generation of blockchain development because of its safety guarantees. [8/14]
Fri Jul 30 16:52:57 +0000 2021
Mori-cli ensures that your cryptofunds get to your heirs if you’re incapacitated or worse. (It’s part of a general investigation in Timelock solutions, as the next generation of #SmartCustody) [7/14] https://github.com/BlockchainCommons/mori-cli
Fri Jul 30 16:52:57 +0000 2021
We’re also continuing work on developer command-line tools. Sweeptool-cli helps you to search and sweep all funds out of descriptor-based wallets, in particular for multisig-based asset recovery. [6/14] https://github.com/BlockchainCommons/sweeptool-cli
Fri Jul 30 16:52:57 +0000 2021
Many thanks to our sustaining sponsors Bitmark (@BitmarkInc), Avanti Bank (@AvantiBT) Unchained Capital (@unchainedcap), and Blockchainbird (@henkvancann) and our many smaller funders for their patronage to make these projects possible. [14/14]
Fri Jul 30 16:52:58 +0000 2021
If you’re a supporter of our work, especially if you’re a company that benefits from it, please become a patron, so that we can continue to make key management and cryptocurrency safe, private, independent, and open. [13/14] https://github.com/sponsors/BlockchainCommons
Fri Jul 30 16:52:58 +0000 2021
Also take a look at our quarterly report for some details on our upcoming Q3 priorities! [12/14] https://www.blockchaincommons.com/quarterlies/Q2-2021-Report/
Fri Jul 30 16:52:58 +0000 2021
We’re particularly proud of the work we’re seeing from our new class of summer interns. They’re working on lots of projects for @HRF, including a bitcoin donation app and Tails scripts, but also more general work, such as improvements to Spotbit and deployment of Esplora. [11/14]
Fri Jul 30 16:52:58 +0000 2021
There’s been so much more, including new UR & SSKR docs, work on two translations for Learning Bitcoin from the Command Line (Spanish & Portuguese), new testimony and laws in Wyoming, fresh discussions of the BTCR DID, and the fifth anniversary of Self-Sovereign Identity! [10/14]