Passwords are very important for maintaining your online identity, because they ensure that no one else can access your accounts and do things that you wouldn’t do. As such, you should make sure that your online passwords are as strong as possible. This article will provide some general guidelines for doing so.
Multiple Passwords
Note that I said that you want to ensure your passwords, plural, are strong. That’s because you’ll want at least two. They should both be good passwords, but they should be used in different places.
Use a “non-secure” password for any non-financial websites that you sign up for, such as Facebook and Twitter. Use a different “secure” password for places where your credit card is on file or money changes hands, such as eBay, Amazon, your bank, and your stock broker. Because banks and other financial institutions are more likely to maintain good security over their transactions, reserving a password only for those sites makes it more likely that they will remain safe.
Of course, this could just be the tip of the iceberg. You might want to create a third password for shopping sites, or another one for less reliable sites that you might use. Ideally you would use a different password for every site. That would surely be the most secure, as someone breaking into one site couldn’t get into your other accounts — but clearly that is too many passwords to remember. As a compromise, I’ll talk shortly about an easy technique to both remember and vary your passwords.
Criteria for Bad Passwords
In a moment, I’m going to suggest an excellent method for creating a secure password. However, if you prefer to use your own methods, be sure to watch out for these common problems which could result weak passwords.
- Do not use obvious words. There was a time when “password” was one of the most common passwords on the internet (along with “root” and “”).
- Do not use words from the dictionary as passwords. Some of the oldest password crackers just dumped the entire dictionary at an account to see if any of them worked as passwords. This doesn’t apply just to English either. It’s easy enough for a password cracker to use any dictionary, whether it be French or Klingon.
- Do not depend on a dictionary word with simple substitutions. Though I’ll talk in a bit about the advantage of substituting letters for numbers, a dictionary word with simple substitutions will be no more secure than just a dictionary word. That’s because later password crackers would run not only the dictionary, but also a dictionary with a few substitutions, such as “0”s for “o”s and “1”s for “l”s.
- Do not depend on multiple dictionary words concatenated together. If you were concatenating three or four words, you might be OK, but password crackers were checking two word dictionary concatenations a decade ago.
- Do not use obvious names of people or places you know. Your girlfriend’s name, your street address, and your favorite pet’s name are all straight out. A password cracker may not be able to guess these (though testing against common names is another strategy used by some), but if someone who knows you can break in by hand, that’s no good either.
- Do not write down your password, and especially do not write down your password in an online or computer file. If you picked the best password in the world, it doesn’t matter if someone else can easily look at it.
- Do not keep the same password forever. It’s pain, but you really should change it every year or two, at least, just in case someone has broken into one of your accounts, and you don’t know it.
A Method for Creating a Strong Password
So you’ve learned a lot about what makes a bad password. What makes a good password? The following suggests one method that you can use to create a password that’s not easily breakable — but which is easily memorable.
- Pick a short phrase, or an obscure but memorable long word. For example “amber waves” or “perspicacious”.
- Shorten it to 7 characters, such as “ambrwvs” or “prspccus”.
- Convert a letter other then first to a number. You can use those obvious substitutions here (e.g., A=4, B=8, E=3, G=6, I=1, L=1, O=0, R=2, S=5, T=7), since they’re not your only method of security. This might produce “ambrwv5” or “pr5pccus”.
- The next part is the key trick: use a specific letter from the domain name for the last character for your password and capitalize it. For example, you might add the third o from google, producing “ambrwv5O” or “pr5pccusO” for a GMail password. This ensures that even if you use your password at multiple sites, anyone who steals the password can’t use it another website unless they know the trick. You can also use this trick with your computer’s password by choosing the third letter from the name you use for the computer, or for a password required for a software application, by using the third letter from the app’s name.
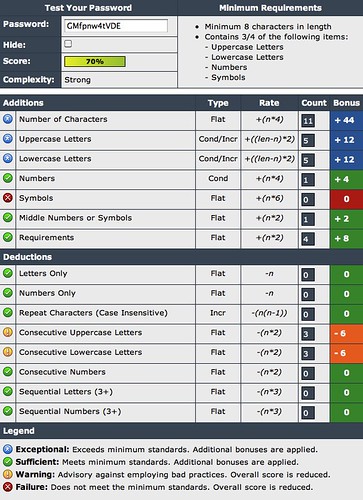
- You should check the quality of your example password at Password Meter -- “ambrwv5O” weight is 54%, which is pretty good for an 8-character password, “pr5pccusO” is 44%, which is OK, but both are significantly better because they will be different at every site.
The same technique can be used with longer words to create more secure financial passwords. These might be easier to remember if you use the first letters from a sentence or poem that you can remember to generate the initial phrase. For example, “My first pet’s name was Arthur the Valiant Dog” would generate “MfpnwAtVD”. Again, you convert one or more letters to a number (“Mfpnw4tVD”).
When you add the domain letters to your secure password, you can strengthen it again by adding multiple letters, possibly to different parts of the password. For example, add the first and last letter the domain name. Thus a Google Gmail password might add a “G” to start and an “E” to the end, producing “GMfpnw4tVDE”. This one rates 70% at Password Meter, but again is actually better because of the site variation.
Also, most financial sites will accept, and some even require, passwords to include a symbol — I don’t recommend this with your “non-secure” password as many ordinary sites do not allow symbols, but if you need one, then the following are some easy to remember substitutions: A=@, E=#, I=!, L=!, O=* S=$, or you can just put a symbol between the first domain letter and the passphrase (many sites will not allow a symbol at beginning or end). For example, password above could become “G$Mfpnw4tVDE” which raises this password’s Password Meter rating to 90%.
With these two passwords you’ll find it very easy to both remember and be secure against most password based attacks.
A High-Tech Alternative
An interesting high-security alternative that works best on webpages is to use SuperGenPass Bookmarklet — it takes the domain name plus a private master password and creates a unique high security password for each website based on a cryptographic hash of the two. It can generate any length of password and you can’t really get a password that is more secure, but there is the occasional web page that the bookmarklet doesn’t work on. Fortunately, you can save http://supergenpass.com/mobile/ as an .html file to your disk and you can open it anytime to manually create a supergenpass password for a website that you can copy and paste. I’ve even used SuperGenPass on my iPhone.
Secondary Authentication
Many sites require you to give them additional identification, such as mother’s maiden name, the name of your pet, etc. Crackers have broken into various celebrities accounts — such as Paris Hilton and Sarah Palin — by researching this information and asking for a password reset.
You can avoid this danger by treating these authentication requests like passwords. I have a standard word that I use for my mother’s maiden name, my pet, etc. They’re things that I can easily remember, but no one could figure out. Like the password technique above, I can easily add a letter from the domain. I’ve had no problem with customer service phone calls to banks; when they ask me for my mother’s maiden name I just spell it out my encode word for them.
Be Safe
None of these approaches is perfect, but they significantly raise the bar against any but the most determined cracker from breaking into one of your accounts. The domain letter technique will also make it very difficult for a cracker to break into your more important financial accounts if he gets access to your password from a poorly secured website or masquerades as a legitimate website or email by using a phishing attack.
However, don’t ever think that a good password is the be-all and end-all of security. You also have to protect it adequately, and that doesn’t just mean not writing it down, as mentioned above. You also must be alert to “social engineering”, where a cracker might call you or email you pretending to be associated with some institute where you might have an account.
Security is a constant game of oneupmanship between you and the black hats. Thus you need to ensure that you’re always alert to the current best practices for setting, resetting, and protecting all of your security information on the internet.
(Photo credit: rattodisabina/ / CC BY 2.0)
Comments
URL: I had an idea once to start a very famous community, ask for login info and use those usernames and passwords to gain on other sites, since most people use the same password for most sites. It sounds silly, but I think that’s how Twitter was hacked some time back. Moral of the story, don’t use same passwords on every site. Nice post btw Chris, I need to start creating pass myself.
Senthil 2009-09-26T15:24:58-07:00
I do know that in fact there are criminals that host “honey pot” websites with semi-legitimate content (games, files, music, porn,etc.) solely for the opportunity to collect passwords from unknowing users. So you need to be particularly careful the more fly-by-night the website is. I’ve not heard of any social media / mashup websites set up for this purpose, but I would not be surprised if there was.
ChristopherA 2009-09-26T22:34:11-07:00
Thank you Chris for the detailed article on password best practices. I like to use roboform for the purpose and of course having a sophisticated randomized combination of different passwords will greatly reduce the chances of being compromised and thats where the roboform software comes in to manage the passwords.
Jingle Vannis 2010-02-07T07:14:08-07:00
Very nice post. I especially like the unique-per-site approach. One thing you didn’t mention was OpenID, which I with gurgling joy register with whenever the opportunity arises. I wish the world used OpenID so I could just have one gigantically monstrous password to rule my world with.
Kalle Alm 2010-02-23T09:12:08-07:00
Life With Alacrity
© Christopher Allen

