RT @kimdhamilton: Vahttps://www.lifewithalacrity.com/assets/images/media/cation reading list (completed): The Haunting of Hill House, The Martian, Wide Sargasso Sea, and NIST Draft “Taxonomic…
Thu Aug 01 17:51:12 +0000 2019
RT @kimdhamilton: I highly recommend all, but only the NIST paper is still accepting public comments (until Aug 9). So I recommend reading…
Thu Aug 01 17:51:13 +0000 2019
Replying to @kallewoof and @GoldenChaosGod
In addition to the #RWOT9 F2F in Prague Sept. 3-6, there is also the BTCR virtual hackathon starting this Monday that uses a Bitcoin transaction as the Decentralized Identifier (DID). https://weboftrustinfo.github.io/btcr-hackathon-2019/
Fri Aug 02 02:09:12 +0000 2019
Replying to @GoldenChaosGod and @kallewoof
The Decentralized IDentifier (DID) spec, originally incubated at #RebootingWebOfTrust has been nurtured for the last few years in the W3C Credentials CG, and is now on way to be run as by an official W3C Working Group to become an international standard: https://w3c-ccg.github.io/did-spec/
Fri Aug 02 02:26:24 +0000 2019
Replying to @CleanApp
I define commons as “any regenerative, self-organizing complex system that can be drawn upon for deep wealth.” These include regenerative systems such as communities, markets, intellectual property, etc. http://www.lifewithalacrity.com/2015/11/a-revised-ostroms-design-principles-for-collective-governance-of-the-commons-.html
Fri Aug 02 15:35:48 +0000 2019
Replying to @CleanApp
The key is keeping the regeneration of wealth going, with includes not withdrawing capital (physical, social, or enclosures of intellectual) which requires some bounds on the authority on those benefiting from that regenerative wealth.
Fri Aug 02 15:40:39 +0000 2019
Replying to @cycryptr and @kimdhamilton
More generically a Lightning service that pins an IPFS object to ensure its availability would be great!
Sat Aug 03 03:14:02 +0000 2019
Replying to @CleanApp
I’m not quite that “resource pools that underpin social processes” is phrased quite right. Social processes can support resource pools, but resource pools do not inherently have social processes.
Sat Aug 03 03:19:46 +0000 2019
Replying to @CleanApp
Still feels backwards. “resource pools need effective social processes to survive extraction of wealth”. That some social processes are also commons is not the key point.
Sat Aug 03 08:13:58 +0000 2019
RT @CleanApp: What is the law of “commons” — ?
https://medium.com/cryptolawreview/law-of-blockchain-commons-29ce6c0720a5
Sat Aug 03 16:18:45 +0000 2019
This group thinking along similar lines as I have been the last few years: “How do we ensure we make the right decisions as a collective? How do we allocate funds fairly? How do we avoid plutocracy in these new economic systems?” @jeffemmett https://medium.com/giveth/introducing-the-commons-stack-scalable-infrastructure-for-community-collaboration-6886eb97413e
Sat Aug 03 16:26:29 +0000 2019
“attacker would need to continually expend funds to bend the system towards their desired outcomes, rather than purchasing the votes once to obtain their desired outcomes indefinitely…raises the costs of influencing the system over long periods of time” https://medium.com/giveth/conviction-voting-a-novel-continuous-decision-making-alternative-to-governance-aa746cfb9475
Sat Aug 03 16:38:51 +0000 2019
I appreciate the community exploring the design space they call “token design” in the Ethereum community (bonding curves, curation markets, continuous voting, etc) but my architectures for these only use a single token, bitcoin, using L2 (payment channels like LN & sidechains).
Sat Aug 03 16:44:58 +0000 2019
Replying to @JTremback
Why? Two reasons: I’m not confident that many having different tokens does not add huge issues of value signaling & exchange risk. A sidechain can be designed on collapse to immediately pay all participants. 2nd, lack confidence in EVM—might as well trust a sidechain federation.
Sat Aug 03 16:53:25 +0000 2019
Replying to @JTremback
I will say that my ideas of sidechains & other L2 are somewhat heretical to many of peers. For instance, I could see a corporation being a sidechain: you purchase rights by locking bitcoin, you exercise those rights, and exit by getting more or less bitcoin than you started.
Sat Aug 03 16:57:08 +0000 2019
Replying to @jeffemmett and @commonsstack
I hoping to be able to devote some resources in the future to demonstrate how to use these emerging incentive/mechanism design principles using different architectures than Ethereum tokens. Diversity in the solution space is needed until proof emerges. https://twitter.com/christophera/status/1157693854063009794?s=21
Sat Aug 03 17:02:27 +0000 2019
Replying to @JTremback
No forking. All the coins are still bitcoin, locked on the L1 chain with simple scripts. The sidechain is a distributed (not decentralized) L2 app & as a whole system has to be built to be trusted in its context to do its job, but recourse back to L1 is easier like in Lightning.
Sat Aug 03 17:38:58 +0000 2019
Replying to @JTremback
The L2 DAO app as a whole is not limited to script. @Blockstream’s Liquid K2 sidechain demonstrates that, with many additional scripting features not found in bitcoin, many of which should NOT be in bitcoin and are safer in a L2 app.
Sat Aug 03 17:42:32 +0000 2019
Replying to @ferranrego and @JTremback
I have mixed feelings. I like that they are experimenting with sidechains, merge mining & alternative L2 smart contracts. However, I’m fairly sure I’d make different design choices in all of those areas. Do have to give them credit they have shipped and I have not :-)
Sat Aug 03 17:46:22 +0000 2019
RT @ChristopherA: @JTremback No forking. All the coins are still bitcoin, locked on the L1 chain with simple scripts. The sidechain is a di…
Sat Aug 03 17:46:54 +0000 2019
RT @ChristopherA: @JTremback The L2 DAO app as a whole is not limited to script. @Blockstream’s Liquid K2 sidechain demonstrates that, with…
Sat Aug 03 17:46:56 +0000 2019
RT @kimdhamilton: @ChrisLundkvist @2357_is_prime @csuwildcat @ChristopherA @danpape @jonnycrunch I agree – solid work. I wish I had time t…
Sun Aug 04 02:38:02 +0000 2019
Amused to find that Bitcoin Coffee https://www.bitcoincoffee.cz/ is a block away from the venue for our next #RebootingWebOfTrust in Prague next month. Hopefully a good omen for getting a more functional BTCR DID method & wallet working during the event!
Mon Aug 05 06:24:08 +0000 2019
Our virtual hackathon to continue development of decentralized identifiers on bitcoin (aka the BTCR DID Method) runs Monday through Friday this week starting tomorrow at 10am PT. Join @kimdhamilton and I to help this open source DID project to catch up! https://weboftrustinfo.github.io/btcr-hackathon-2019/
Mon Aug 05 06:31:19 +0000 2019
RT @AlterUK21: Do you want to be able to “pull the plug” on your online life? You need to think about your “self-sovereign identity” https…
Tue Aug 06 15:44:03 +0000 2019
RT @kimdhamilton: If you are experiencing #btcr #did hackathon FOMO, follow along with our progress via our daily digests at https://t.co/8…
Wed Aug 07 03:40:41 +0000 2019
RT @kimdhamilton: @ChristopherA @danpape @JoeAndrieu @cycryptr @yancyribbens @hawkmauk @peacekeeper Our up-to-date list of BTCR references/…
Wed Aug 07 03:40:58 +0000 2019
RT @kanzure: Announcing my new bitcoin vault proposal (does not require any forks): https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2019-August/017229.html expanding on @ittayeyal/@el33t…
Wed Aug 07 16:09:18 +0000 2019
RT @SovrinID: Who else is heading to Rebooting the Web of Trust? See you there! https://twitter.com/ChristopherA/status/1153376693907644416
Thu Aug 08 16:56:45 +0000 2019
RT @kimdhamilton: Lots of progress and momentum from our #BTCR #DID Hackathon. If you’d like to contribute, join us at RWOT9 https://t.co/v…
Sat Aug 10 06:18:58 +0000 2019
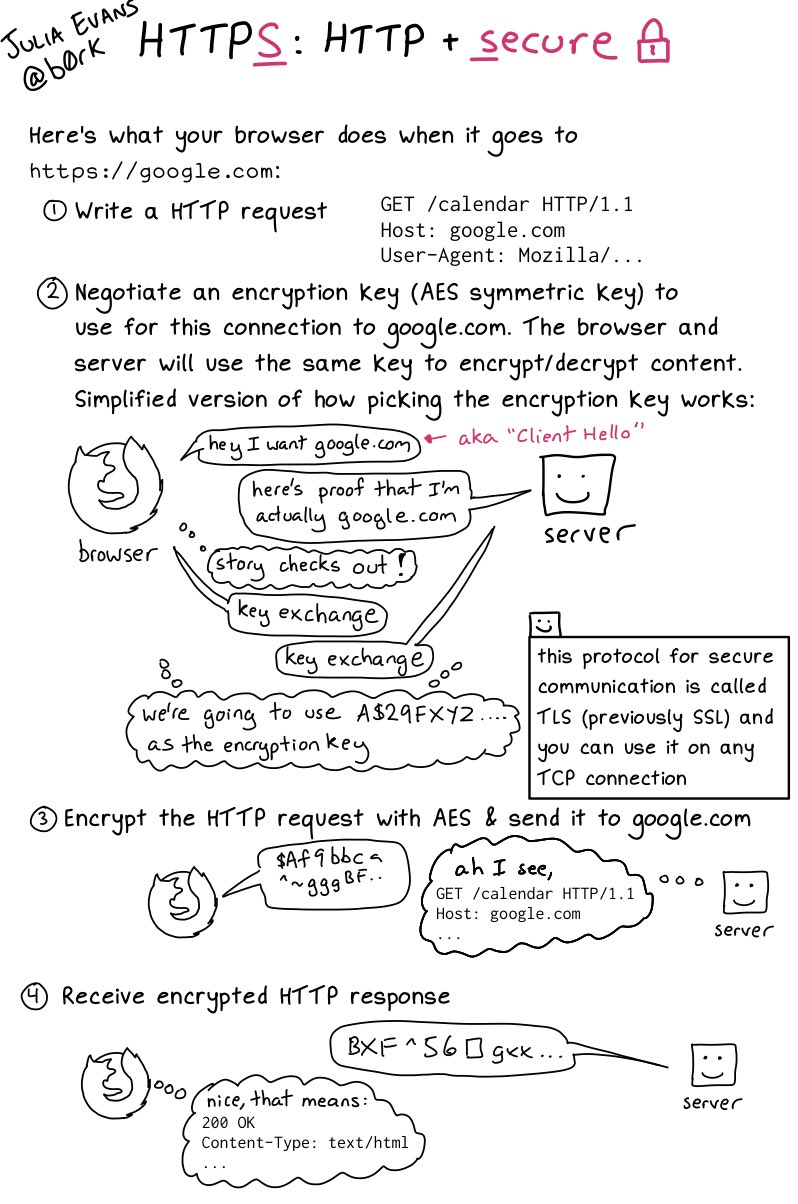
RT @b0rk: HTTPS: HTTP + security
Sun Aug 11 23:26:09 +0000 2019
Replying to @b0rk
I (a co-author of TLS 1.0) always describe it as integrity check first, then a key exchange (which includes authentication of none (rarely) of one (usually) or both parties(rarely)) then the asymmetric encryption.
Sun Aug 11 23:32:04 +0000 2019
RT @ChristopherA: I’m also interested in contracting a US or Canada-based bookkeeper that knows or is willing to learn basic command line a…
Mon Aug 12 19:58:32 +0000 2019
RT @Appelcline: I’ve been happily doing tech writing for @BitmarkInc for over a year now. Recently, I’ve supported them in their work on ta…
Mon Aug 12 20:58:12 +0000 2019
RT @feross: We need more experimentation to figure out how to get open source maintainers paid. The
thanksexperiment was very educationa…
Mon Aug 12 20:59:13 +0000 2019
RT @BlockchainComns: Blockchain Commons was founded to support blockchain infrastructure, security & privacy. One project we are supporting…
Tue Aug 13 16:18:56 +0000 2019
Companies! Support our efforts to create a DID (Decentralized IDentifier) standard! The W3C is requesting public comments on our proposal to form an official Working Group to be authorized to continue efforts to make it an international standard: https://lists.w3.org/Archives/Public/public-new-work/2019Aug/0000.html
Tue Aug 13 16:30:58 +0000 2019
(https://twitter.com/ChristopherA/status/1161314210736775168)
For W3C purposes, the bigger the organization the better, though all organizations are welcome to endorse this proposal. Please mention why you are interested in this making the DID specification nascent standard, from desirability of patent & IP protection or just needing it!
Tue Aug 13 16:38:11 +0000 2019
(https://twitter.com/ChristopherA/status/1161316026971090944)
The W3C-CCG’s (Credentials Community Group) last task before turning the DID (Decentralized Identifier) spec over to a WG is to publish a Final Report. We are in a 7 day period for community members to assert any substantial objections to publishing this: https://w3c-ccg.github.io/did-spec/CGFR/2019-08-10/
Tue Aug 13 18:23:43 +0000 2019
Replying to @Ferdinando1970, @kimdhamilton, @opentimestamps and @danpape
In the BTCR architecture we are planning Lightning Network-style P2P updates that only have to be transactioned to Bitcoin on revocation & disputes. Thus BTCR-based decentralized identifiers will scale as well as LN. Microsoft has their own Bitcoin-based L2 that can scale more.
Tue Aug 13 18:31:40 +0000 2019
RT @Ferdinando1970: BTCR DID Method Updates by @kimdhamilton
Fascinating stuff, if only it didn’t imply one tx per DID creation/update…
N…
Tue Aug 13 18:31:46 +0000 2019
RT @ChristopherA: @Ferdinando1970 @kimdhamilton @opentimestamps @danpape In the BTCR architecture we are planning Lightning Network-style P…
Tue Aug 13 18:31:51 +0000 2019
RT @fuxjaeger: “Without a shared language there will be no clarity on mutual goals”
as mentioned by @ChristopherA in a recent discussion w…
Fri Aug 16 16:05:35 +0000 2019
RT @DigitalscotNews: Building an SSI Ecosystem : Self-Sovereign Identity , featuring presentations from @mike_brown_yyc, @ChristopherA and…
Mon Aug 19 14:42:38 +0000 2019
One of the inspirations for my card-based GMless storygame “Gate Watch” was a desire to change the experience of the Fiasco RPG to allow more broader, more episodic stories. Now @bullypulpit_hq is offering a @Kickstarter for a their own card-based storygame based on Fiasco. 👏👍 https://twitter.com/bullypulpit_hq/status/1157306929770848256
Mon Aug 19 22:34:25 +0000 2019
I’ve been puzzling about this topic (L2 pay for storage) for a while, but more napkin scratching than actual code. Increasingly the decentralized apps I am architecting need to be able to pay for reliable storage (mostly IPFS pinning) and I want Lightning Network not FileCoin. https://twitter.com/dr_orlovsky/status/1162417145361383424
Mon Aug 19 23:29:19 +0000 2019
I’m seeking a standard’s based compact binary representations of date and/or time that isn’t as precise (for instance the GMT day is ok for dates) but isn’t broken in 2038 like linux time is & is good for the long term. Any recommendations from masters of esoteric time formats?
Mon Aug 19 23:37:07 +0000 2019
Replying to @iang_fc
I am storing this as part of a cryptographic secret and it need needs to be small as possible. But ideally relatively standard so code does not have to go through too many gyrations to compare to clock time. And doesn’t linux time still have the 2038 bug?
Tue Aug 20 00:25:27 +0000 2019
Replying to @boscolochris
FileCoin is not deployed & proven yet, much less that it can support Satoshi level micro-transactions. Also, my projects are already bitcoin-centric & I worry about currency exchange issues & censorship resistance; thus prefer to keep projects like BTCR DIDs using one coin.
Tue Aug 20 00:31:22 +0000 2019
Replying to @dr_orlovsky, @giacomozucco and @MarkFriedenbach
The topic of storage in the Decentralized Identifier architecture has come up with 3+ different proposals from multiple vendors. Maybe you should come to #RWOT9 in Prague Sept 3rd-6th to storm about Storm? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/README.md
Tue Aug 20 03:07:34 +0000 2019
(https://twitter.com/ChristopherA/status/1163648743868006400)
Let me know if you are interested in getting together there, and who else should be there, and I can arrange it.
Tue Aug 20 03:08:44 +0000 2019
RT @ChristopherA: @dr_orlovsky @giacomozucco @MarkFriedenbach The topic of storage in the Decentralized Identifier architecture has come up…
Tue Aug 20 03:08:53 +0000 2019
RT @hackylawyER: Monetize your data folks: Citing fundamental rights in property to justify selling/monetizing personal data.
Me: The fund…
Tue Aug 20 06:35:05 +0000 2019
Replying to @aris_ada and @adamshostack
I’m don’t need that level of precision of time, I need at best day. I’d prefer 32 bits or smaller.
Tue Aug 20 06:38:03 +0000 2019
Over 50 current #decentralized #identity topic papers submitted for #RWOT9 in Prague 9/3-6th, on subjects ranging from #DIDs #VerifiableCredentials #Authentication #Trust #IdentityPub #Mastadon #Agents, #SecureStorage, #KeyManagement #Wallets #iOT & more!
https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/README.md
Tue Aug 20 17:38:24 +0000 2019
(https://twitter.com/ChristopherA/status/1163867896474324992)
Interested in attending this multi-community design workshop on decentralized identity #RWOT9 in Prague on September 3rd-6th? https://rwot9.eventbrite.com. If you would like to demonstrate for support this event & get your logo on all final white papers: sponsorships@weboftrust.info
Tue Aug 20 17:44:52 +0000 2019
RT @ChristopherA: Interested in attending this multi-community design workshop on decentralized identity #RWOT9 in Prague on September 3rd-…
Tue Aug 20 17:44:58 +0000 2019
RT @discipl_org: We’re proud to participate this #RWOT9 event in Prague and contribute with a X.509 DID method proposal https://t.co/Rpjawu…
Tue Aug 20 17:45:08 +0000 2019
Replying to @iang_fc
Right now I’m considering for storage rounding down the 64-bit Linux time by the seconds in a day to get a smaller int (maybe vint). Then when you do reverse you add half a day to unambiguously set day correct to avoid leap seconds maybe making it 11:59:59 the day before.
Tue Aug 20 18:11:43 +0000 2019
RT @ChristopherA: @iang_fc Right now I’m considering for storage rounding down the 64-bit Linux time by the seconds in a day to get a small…
Tue Aug 20 18:11:51 +0000 2019
My congratulations to @TheBlueMatt & appreciation for @sqcrypto supporting those that make this technical & financial revolution possible. To keep the momentum going not only must we find ways to support the intellectual commons ourselves, but also demand the same of our peers. https://twitter.com/TheBlueMatt/status/1163852530142654464
Wed Aug 21 00:42:15 +0000 2019
I’m seeking a part-time Linux system adin that has a strong knowledge of privacy technologies, tor, standing up web services, hardening servers, etc. Will be working with bitcoin tech but does not need to be a core developer. Preferably not based in a Five Eyes country. DM me.
Wed Aug 21 00:55:37 +0000 2019
Replying to @o0ragman0o
Preferably ;-)
Wed Aug 21 00:58:53 +0000 2019
So I had a couple of discussion this week with DNS experts about use of recursive DNS to correlate users with traffic. Google’s 8.8.88 & Cloudflare’s 1.1.1.1 are claimed to be bad actors, with quad9’s 9.9.9.9 & maybe Cisco claimed to be good actors. How can we verify this?
Wed Aug 21 01:06:40 +0000 2019
I’m quite pleased that in this week’s Wyoming Blockchain Task Force that they are discussing a legal issue that I have been personally advocating about, which is that keys should not be considered digital assets, as keys are not designed to be transferred https://www.wyoleg.gov/InterimCommittee/2019/S3-2019081920LSO-0163v0.3.pdf
Wed Aug 21 06:12:22 +0000 2019
(https://twitter.com/ChristopherA/status/1164057639233323008)
My key point is that attempting to demand keys has larger risks to both personal privacy and in multisig scenarios even the rights of others. Unlike keys, digital assets are designed to be transferred. You can see context for my advocacy in this thread https://twitter.com/ChristopherA/status/1121883628701544449
Wed Aug 21 06:16:52 +0000 2019
(https://twitter.com/ChristopherA/status/1164058767895326720)
It is also quite pleasing that the Wyoming legislative Blockchain Task Force is truly listening, not only to me but also to other blockchain experts and the broader community.
Wed Aug 21 06:21:44 +0000 2019
(https://twitter.com/ChristopherA/status/1164059996142751744)
If you’d like to catch the discussion on this topic by the task force at this week’s public meeting, it starts at the 3:24:36 mark. Some nuanced discussion, and the co-chairs @Rothfuss & @Tyler_Lindholm get the essence! Final language to still be drafted. https://youtu.be/4ga8ouSfcXU?t=12046
Wed Aug 21 06:40:11 +0000 2019
RT @ChristopherA: It is also quite pleasing that the Wyoming legislative Blockchain Task Force is truly listening, not only to me but also…
Wed Aug 21 06:54:23 +0000 2019
RT @ChristopherA: If you’d like to catch the discussion on this topic by the task force at this week’s public meeting, it starts at the 3:2…
Wed Aug 21 06:54:25 +0000 2019
Replying to @amigus
Thanks for your commentary. I didn’t mean to name and shame, just very confused on how to verify what is really happening and how to verify the claims of these DNS offerings. It feels like DNS used for correlation makes a lot of other privacy tech less useful.
Wed Aug 21 17:21:27 +0000 2019
(https://twitter.com/ChristopherA/status/1164064636632616965)
I’ve been trying to come up with an analogy for why you should treat keys extremely carefully and focus instead on the requirements to require use of them for transfer of assets but not the keys themselves. The best I have so far follows in next tweet…
Wed Aug 21 17:31:41 +0000 2019
(https://twitter.com/ChristopherA/status/1164228592244424704)
Keys are like a safe-deposit box that opens to the secret words “Open Sesame”. Anyone overhearing can make use those words to open the box, but also may compromise other assets belonging not only the key holder, but also joint property of their wife, their biz partner & more!
Wed Aug 21 17:31:57 +0000 2019
RT @amigus: @ChristopherA That’s definitely true but the discussion of solutions need not devolve into determining how to choose a provider…
Wed Aug 21 18:07:04 +0000 2019
RT @hackylawyER: “We now face the challenge of abolishing digital servitude – where people are mined for their data, and served back inform…
Wed Aug 21 18:11:56 +0000 2019
(https://twitter.com/ChristopherA/status/1164228661572034560)
A good question about the current legal text in the Wyoming bill proposal from @jasoncoombsceo “(if) a private key is not an asset separate from the digital asset that it controls? Then stealing your key isn’t a theft, right” https://twitter.com/jasoncoombsceo/status/1163968752616013824?s=21
Wed Aug 21 20:01:16 +0000 2019
RT @ChristopherA: A good question about the current legal text in the Wyoming bill proposal from @jasoncoombsceo “(if) a private key is not…
Wed Aug 21 20:01:24 +0000 2019
(https://twitter.com/ChristopherA/status/1164266236114419713)
Also “(can a custodian)…steal a client’s private keys…travel to a foreign jurisdiction and transfer the digital assets controlled by those keys, leaving no crime to prosecute in Wyoming?” https://twitter.com/jasoncoombsceo/status/1163969765141909506?s=21
Wed Aug 21 20:03:57 +0000 2019
RT @ChristopherA: Also “(can a custodian)…steal a client’s private keys…travel to a foreign jurisdiction and transfer the digital assets co…
Wed Aug 21 20:07:54 +0000 2019
RT @TheBlueMatt: Gotta incorporate this into Bitcoin Core at some point. Indeed, also want to use it in my DNS seed scanner :) https://t.co…
Wed Aug 21 21:08:02 +0000 2019
Replying to @wiz
Blockchain Commons is thinking about hosting a few swamp-C’s as full BPG ASNs in some key remote peering hosting facilities to serve various blockchain infrastructure services. For instance, we help sponsor this with @TheBlueMatt: https://twitter.com/BlockchainComns/status/1161310976030867456?s=20 — open to best ideas.
Wed Aug 21 21:14:58 +0000 2019
What is current thinking on open source contributor agreements? CLAs vs. CAAs vs DCO? A DCO (developer certificate of origin) is simple and makes sense for volunteer work, but a CLA or CAA (contributor assignment agreement) feels required for paid open source work. @kemitchell ?
Wed Aug 21 21:20:52 +0000 2019
Replying to @hiharveen
We should think of secret keys as an essential root for identity in the virtual world, thus why they must be treated differently legally. To deprive someone of rights or identity in the physical world requires more due process than that needed for civil property disputes.
Wed Aug 21 21:30:25 +0000 2019
RT @ChristopherA: @hiharveen We should think of secret keys as an essential root for identity in the virtual world, thus why they must be t…
Wed Aug 21 21:30:31 +0000 2019
RT @MeeplesTogether: Can a co-op be too difficult to be fun? That was the consensus when we played The Captain is Dead: Lockdown. https://…
Thu Aug 22 00:57:26 +0000 2019
Last call! We need more companies that are not currently members of the W3C to send email offering why they desire to support the effort to make the Decentralized Identifier (DID) spec an international standard. https://twitter.com/ChristopherA/status/1161314210736775168
Fri Aug 23 15:56:30 +0000 2019
If your organization is a W3C member, please have your AC vote YES on the Decentralized Identifier Working Group (DIDWG) Charter at: https://www.w3.org/2002/09/wbs/33280/did-wg-2019/ Don’t presume your organization’s representative has voted, many focus on other WGs and may not be aware of your interest!
Fri Aug 23 16:01:36 +0000 2019
Only ten days before #RWOT9 in Prague http://rwot9.eventbrite.com! Over 50 pre-reading topic papers on decentralized identity. That means I need to read 5 a day. This thread is for my notes on the advance topics in https://github.com/WebOfTrustInfo/rwot9-prague/tree/master/topics-and-advance-readings …
Fri Aug 23 22:26:18 +0000 2019
(https://twitter.com/ChristopherA/status/1165027510100221952)
“A DID based solution for verifiable data streaming & processing in cyber-physical systems” KEY CONCEPT: DIDs for verifiable data chains to drive event processing in mobile app & server architectures, to increase safety through data provenance. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/A_DID_based_solution_for_data_processing.md
Fri Aug 23 22:33:07 +0000 2019
(https://twitter.com/ChristopherA/status/1165029227155968002)
…use cases include “real-time vehicle value, dangerous driving, road and obstacle mapping, usage-based insurance (UBI), reliable feedback loops into driver assistance system (DAS) and autonomous driving infrastructures, V2V/V2I interactions and cooperative mobility systems.”
Fri Aug 23 22:34:24 +0000 2019
(https://twitter.com/ChristopherA/status/1165029551170129920)
…”Digital twins can represent objects and entities as varied as IoT sensors, ECUs, spare parts, vehicles, traffic lights, access gates, human users, or a city…or represent intangible entities like services, code, data, processes and knowledge.”
Fri Aug 23 22:36:05 +0000 2019
RT @ChristopherA: “A DID based solution for verifiable data streaming & processing in cyber-physical systems” KEY CONCEPT: DIDs for verifia…
Fri Aug 23 22:37:49 +0000 2019
(https://twitter.com/ChristopherA/status/1165029974060851200)
TOPIC Bare minimum agent for identity KEY CONCEPT How do we allow those with only access to cheap “dumb” phones say in Africa) to “take back control of their digital selves”? What is the “minimum specifications that an identity app needs to provide value”? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Bare-minimum-agent.md
Fri Aug 23 22:43:03 +0000 2019
RT @ChristopherA: TOPIC Bare minimum agent for identity KEY CONCEPT How do we allow those with only access to cheap “dumb” phones say in Af…
Fri Aug 23 22:43:08 +0000 2019
(https://twitter.com/ChristopherA/status/1165031725732257793)
There is a mention of an “ID Pass” system for refugee camps that was “cool”. There wasn’t a link in the paper but maybe he is referring to one of the projects in “GSMA Refugees & Identity” https://www.gsma.com/mobilefordevelopment/wp-content/uploads/2017/06/Refugees-and-Identity.pdf
Fri Aug 23 22:48:53 +0000 2019
(https://twitter.com/ChristopherA/status/1165033192618770432)
Topic of decentralized identity for the refugee use case has long been of interest at #RWOT going back to the 1st #ID2020 at the UN. I know HTC will be at #RWOT9 & have announced a cheaper self-sovereign cell phone, but we have a way to go. Glad to see this topic re-emerging.
Fri Aug 23 22:53:33 +0000 2019
(https://twitter.com/ChristopherA/status/1165034368387055616)
TOPIC Using DID for use of Rotating Savings and Credit in Developing/ Emerging Economies KEY CONCEPT: ROSCA is a kind of micro-finance in emerging economies, but scaling them up risks fraud. Using DIDs w/ anonymity could help reduce these problems. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/DID_for_ROSCAS.md
Fri Aug 23 22:59:02 +0000 2019
RT @ChristopherA: There is a mention of an “ID Pass” system for refugee camps that was “cool”. There wasn’t a link in the paper but maybe h…
Fri Aug 23 22:59:07 +0000 2019
(https://twitter.com/ChristopherA/status/1165035748799549440)
…a ”common attack is if the person having secured the pot doesn’t turn up next time. This is typically mitigated by having due diligence and KYC for every participant…(but) defaulter has to be sent a mail and then taken to court and legal proceedings take their own sweet time.”
Fri Aug 23 23:01:35 +0000 2019
(https://twitter.com/ChristopherA/status/1165036389664088065)
…”attack could be from the organizer where the auctions…rigged by discounting too much by using proxies or agents…(such) that the participant who is actually needy and deserves money is not able to get the required amount which leads to more discount in subsequent turns.”
Fri Aug 23 23:03:14 +0000 2019
(https://twitter.com/ChristopherA/status/1165036805449641984)
…“most rampant type of scam is similar to multi level marketing, having a hierarchy of agents to pool in people. In many cases, chit fund is simply a name to attract people which in reality is a ponzi scheme.”
Fri Aug 23 23:04:04 +0000 2019
(https://twitter.com/ChristopherA/status/1165037015391358976)
…Requirements for a digital ROSCAS: “Anonymity: Not being able to know who the person is makes it highly unlikely that the auction or any process can be rigged through collusion.”…
Fri Aug 23 23:06:03 +0000 2019
(https://twitter.com/ChristopherA/status/1165037514643533824)
…Requirement: ”One to One relationship: Being able to prove that a person owns the DID by giving a certificate of binding with some biometric (owned on the device by individual) without revealing the biometric.”…
Fri Aug 23 23:07:12 +0000 2019
(https://twitter.com/ChristopherA/status/1165037803996008448)
…Requirement: ”Self Sovereign: the identifier should be owned by individuals and can’t be created by any other entity.”…
Fri Aug 23 23:08:17 +0000 2019
(https://twitter.com/ChristopherA/status/1165038078299275264)
…DIDs ”provide all the requirement to be an effective identity layer for successfully running the ROSCAS digitally…The best of the scenario could be if a farmer from India is able to participate in a ROSCAS run in West Africa, thereby helping borrowers and in turn…earning.”
Fri Aug 23 23:09:31 +0000 2019
(https://twitter.com/ChristopherA/status/1165038389030092800)
TOPIC Decentralising OpenCerts KEY CONCEPT. Paper begins with review of Singapore govtech issuance OpenCert verifiable credentials issued by white listed institutions without use of DIDs, and issues thereof like centralization, weak identity & privacy. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Decentralising%20OpenCerts%20v2.md
Fri Aug 23 23:16:12 +0000 2019
RT @ChristopherA: TOPIC Decentralising OpenCerts KEY CONCEPT. Paper begins with review of Singapore govtech issuance OpenCert verifiable cr…
Fri Aug 23 23:16:23 +0000 2019
(https://twitter.com/ChristopherA/status/1165040070518198272)
…The paper then goes into a number of potential solutions for those problems. “adding an acceptance step in the issuance process, the recipient has the choice to opt-in to storage of their certificate. They could request corrections or simply opt-out”
Fri Aug 23 23:18:03 +0000 2019
(https://twitter.com/ChristopherA/status/1165040533363802112)
…”There is a debate over whether certificates should identify recipients using national identity, public key or some other variation of Decentralised Identity (DID). Our view is that national identity and DID will coexist but…”
Fri Aug 23 23:19:03 +0000 2019
(https://twitter.com/ChristopherA/status/1165040786733326336)
…“…until the usability of wallet software improves and wallet use becomes mainstream, we have to make do with personal names as the recipient identifier for OpenCerts. The strength of the credential can be bolstered with additional attributes like national ID and birthdate.”
Fri Aug 23 23:49:17 +0000 2019
(https://twitter.com/ChristopherA/status/1165048393107787777)
TOPIC Decentralized Identifiers to Enable Trusted Machine Economy KEY CONCEPT Use DIDs their underlying DHTs to secure IoT devices ranging from buildings to smart cars, in particular securing the large amount of data they produce. Marketplaces will emerge. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Decentralized%20Identifiers%20to%20Enable%20Trusted%20Machine%20Economy.md
Sat Aug 24 00:01:10 +0000 2019
RT @ChristopherA: TOPIC Decentralized Identifiers to Enable Trusted Machine Economy KEY CONCEPT Use DIDs their underlying DHTs to secure Io…
Sat Aug 24 00:01:19 +0000 2019
(https://twitter.com/ChristopherA/status/1165051383831134208)
…”users tranport the encrypted data to smart contracts for storage via MAM channel, and simultaneously make a verifiable Auth-compliant request to the platform in claim of “being tradable.” Later, the verified data will enter data marketplace to be traded.”
Sat Aug 24 00:01:56 +0000 2019
(https://twitter.com/ChristopherA/status/1165051577742196736)
…”a car equipped with LIDAR…a gyroscope & an accelerometer can accurately detect bumps and potholes on the road. Those data sets could be extremely useful for municipal governments as well as companies in fields such as car insurance, navigation applications & road maintenance”
Sat Aug 24 00:03:54 +0000 2019
(https://twitter.com/ChristopherA/status/1165052074947575808)
TOPIC Decentralized Identity as a Meta-platform: How Cooperation Beats Aggregation KEY CONCEPTS “A meta-platform is a platform that enables and fosters participant controlled value transfer across and among other platforms.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Decentralized-Identity-Meta-platform.md
Sat Aug 24 00:06:11 +0000 2019
(https://twitter.com/ChristopherA/status/1165052646144663552)
…”Participant control means that participants may form customized or bespoke virtual platforms of their own choosing…Participant control better balances the interests of participants & platform operators.”
Sat Aug 24 00:08:28 +0000 2019
(https://twitter.com/ChristopherA/status/1165053223121481730)
…”An early paper outlined the potential for identity to be a meta-system. The difference is that a meta-platform enables value transfer between platforms whereas a meta-system enables interoperability between systems.”
Sat Aug 24 00:10:18 +0000 2019
(https://twitter.com/ChristopherA/status/1165053684604006401)
The paper also links to a Medium article by this topics author that I’ve added to my reading list: https://medium.com/selfrule/meta-platforms-and-cooperative-network-of-networks-effects-6e61eb15c586
Sat Aug 24 00:11:26 +0000 2019
(https://twitter.com/ChristopherA/status/1165053967555936256)
That’s my summary for today for the first 5 of 50 advance readings for #RWOT9. The point sharing these advance reading is to help the community understand emerging thoughts and trends of other participants, as well as help build a shared language before the event for everyone.
Sat Aug 24 00:15:43 +0000 2019
RT @ChristopherA: TOPIC Decentralized Identity as a Meta-platform: How Cooperation Beats Aggregation KEY CONCEPTS “A meta-platform is a pla…
Sat Aug 24 00:15:53 +0000 2019
I’m impressed by this list and summary of behavior change strategies. Understanding the basis for persuasion and behavior change often sounds too “soft” for many techies, but I feel having some understanding of them can have big impact on success of tech. https://digitalwellbeing.org/bcttv1_pdf_version/
Sat Aug 24 01:08:54 +0000 2019
Replying to @bsuichies and @trbouma
We have had some papers on the topic of anti-sybil “Proof of Unique Personhood” papers at previous #RWOTs, and there is a new one suggested at #RWOT9. Right now I like @brynosaurus of @EPFL’s approach which he presented at the W3C-CCG https://w3c-ccg.github.io/meetings/2018-08-07/
Sat Aug 24 01:29:10 +0000 2019
9 days until #RWOT9 in Prague, and 5 more topic papers to read & summarize. Remember that an advance reading is not for it to be judged like a peer-reviewed paper. The goal instead is to communicate current interests and inspire, as the best may be ripe for a collaborative paper.
Sat Aug 24 10:50:13 +0000 2019
(https://twitter.com/ChristopherA/status/1165214722553085952)
All 50+ topic papers and advance readings are at https://github.com/WebOfTrustInfo/rwot9-prague/tree/master/topics-and-advance-readings and from these will emerge a dozen or so groups to build & collaborate on together during the design workshop.
Sat Aug 24 10:53:31 +0000 2019
(https://twitter.com/ChristopherA/status/1165215556187803648)
TOPIC Decentralizing Reputation with DID, KEY CONCEPT There continues a strong thread through a number of years of #RWOT to enable peer-to-peer reputation. Peer transactions like dating & physician referral are one of many valuable use cases https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Decentralizing-Reputation-with-DID.md
Sat Aug 24 11:00:10 +0000 2019
RT @ChristopherA: TOPIC Decentralizing Reputation with DID, KEY CONCEPT There continues a strong thread through a number of years of #RWOT…
Sat Aug 24 11:00:20 +0000 2019
(https://twitter.com/ChristopherA/status/1165217227991207936)
…”The transaction cost has traditionally been reduced by introducing a centralized intermediary as technology operator. This avoids lagging open standards and reduces the cost for the peers to operate self-sovereign technology to execute the transaction.…”
Sat Aug 24 11:03:11 +0000 2019
(https://twitter.com/ChristopherA/status/1165217986480730114)
…”…However, as technology cost drops with Moore’s law and standards evolve, the transaction case for centralization becomes moot, leaving search and risk as practical barriers to decentralization.”
Sat Aug 24 11:03:49 +0000 2019
(https://twitter.com/ChristopherA/status/1165218147512639489)
…”Search for a suitable peer and risk of transacting with that peer are related since a good search experience would consider risk as a major influence in the rankings.”
Sat Aug 24 11:05:27 +0000 2019
(https://twitter.com/ChristopherA/status/1165218558852231169)
…”Reputation is highly contextual. My reputation as an Airbnb host has little to do with my reputation as a physician or my FICO score. To scale… commerce based on self-sovereign identity & DIDs we will need to provide a practical alternative to centralized reputation managers”
Sat Aug 24 11:07:00 +0000 2019
(https://twitter.com/ChristopherA/status/1165218946183614466)
…paper suggest some clues on how to implement decentralized reputation can come from experience of Colony’s https://colony.io/whitepaper.pdf “reputation miners”, zkp for privacy, costs must be low compared to value of consumer, and cheating needs to be avoide, maybe by audits. …
Sat Aug 24 11:13:03 +0000 2019
(https://twitter.com/ChristopherA/status/1165220470406316032)
“A medical referral could be worth $thousands & hours of research on the part of the patient. But the decision to allow that same medical record to be used for cancer research might be worth almost nothing ideally would not require a minute’s thought by a patient”
Sat Aug 24 11:14:22 +0000 2019
(https://twitter.com/ChristopherA/status/1165220800997146629)
TOPIC Exploring InterPersonal Data KEY CONCEPT Peoples identities are intertwined, with recursive loops of people and contexts. Ideas from Meg Wheatly’s book Leadership and the New Sciences (1995) is worth revisiting
https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Exploring%20InterPersonal%20Data.md
Sat Aug 24 11:19:13 +0000 2019
(https://twitter.com/ChristopherA/status/1165222020998561792)
…“Identity is defined by Meg as the sense-making capacity of the organization. This understands itself and is relative to other things…Meg also talks about identity as being about boundaries and identity happens when there are distinctions between inside and outside.”
Sat Aug 24 11:20:09 +0000 2019
(https://twitter.com/ChristopherA/status/1165222257997692929)
…”Information is the medium of organization—which is about how entities within share to make sense of themselves. Within organic organisms this happens with chemical signaling. Within human & organizational system this is done with language & other signaling mechanisms.”
Sat Aug 24 11:23:43 +0000 2019
(https://twitter.com/ChristopherA/status/1165223156635684865)
…”Relationships are the pathways of the organization. That is information flows via relationships.”
Sat Aug 24 11:25:10 +0000 2019
(https://twitter.com/ChristopherA/status/1165223517979201536)
…Philip Sheldrake “articulated the difference between “Personal data” and “Interpersonal data”. The former being largely between individuals and institutions and the latter between individuals and each other or more informal clusters or groups of people.”
Sat Aug 24 11:26:22 +0000 2019
(https://twitter.com/ChristopherA/status/1165223821252558848)
…”It is not clear to me how the difference between personal data and interpersonal data is bridged and how we build sufficient institutional confidence in the latter but we believe it is worth exploration.”
Sat Aug 24 11:26:56 +0000 2019
(https://twitter.com/ChristopherA/status/1165223966111232001)
TOPIC KERI for a Universal DKMI, KEY CONCEPT “Key Event Receipt Infrastructure (KERI) provides a minimally sufficient means for managing signing authority and tracking events for a crypto-graphic key-pair based decentralized identifier such as a W3C DID” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/KERI-Universal-DKMI.md
Sat Aug 24 11:29:06 +0000 2019
RT @ChristopherA: TOPIC KERI for a Universal DKMI, KEY CONCEPT “Key Event Receipt Infrastructure (KERI) provides a minimally sufficient mea…
Sat Aug 24 11:29:21 +0000 2019
(https://twitter.com/ChristopherA/status/1165224507981721600)
…“KERI does not require a distributed consensus ledger but may be augmented with such a ledger. As a result KERI is a candidate component of a universal decentralized key management infrastructure (DKMI).”
Sat Aug 24 11:30:34 +0000 2019
(https://twitter.com/ChristopherA/status/1165224879513206786)
…”For decentralized identity systems based on self-certifying identifiers, management of the associated private keys is essential. Because the controlling entity holds their own private key(s) the primary burden of management falls on that entity or its assigns…”
Sat Aug 24 11:33:15 +0000 2019
(https://twitter.com/ChristopherA/status/1165225553068089344)
…”…a decentralized identity system may have a multitude of controlling entities each controlling one or more identifiers. Some of these entities may not have the resources or the expertise to design, build, and maintain secure key management infrastructure…”
Sat Aug 24 11:34:06 +0000 2019
(https://twitter.com/ChristopherA/status/1165225768118472705)
…“…Consequently there is a need for open interoperable decentralized key management infrastructure (DKMI).” “One design approach to composing scalable and performant infrastructure is to find minimally sufficient means for each of the key management tasks.”
Sat Aug 24 11:35:27 +0000 2019
(https://twitter.com/ChristopherA/status/1165226108091957248)
…”This work describes a protocol that provides secure verifiable rotation that solves the problem of successful exploit of a given private key due to exposure when that exploit happens sometime after creation and use of the key.”
Sat Aug 24 11:36:24 +0000 2019
(https://twitter.com/ChristopherA/status/1165226345246281728)
…This paper in some ways goes back to the roots of the first #RWOT over 4 years where many of the requirements of DPKI were defined, but takes one step further to start defining the requirements for self-sovereign key management to support DPKI.
Sat Aug 24 11:43:04 +0000 2019
(https://twitter.com/ChristopherA/status/1165228022527455233)
TOPIC Supreme Court for decent and interop KEY CONCEPT “Flashy, jokey title for a boring, ugly, uncomfortable topic– community service and adjudication. Who watchers the watchers?” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Supreme%20Court%20for%20decent%20and%20interop.md
Sat Aug 24 11:46:42 +0000 2019
(https://twitter.com/ChristopherA/status/1165228936994803712)
…”The conversation around decentralization that took place since #RWOT8 has been a fruitful, which makes abundantly clear an uncomfortable truth– “decentralization” is an almost impossible term to standardize across all its domains”
Sat Aug 24 11:48:02 +0000 2019
(https://twitter.com/ChristopherA/status/1165229273017225217)
“Perhaps it would be easier to start with a slightly more verifiable, objective claim– interoperability. It also feels to me, given the stakes for fundraising and government buy-in, to be a lot more urgent than decentralization ratings for the development of the SSI ecosystem…”
Sat Aug 24 11:49:19 +0000 2019
(https://twitter.com/ChristopherA/status/1165229597555752965)
…”…Maybe we should start there, and set up structures of neutrality (and funding!) to certify and rate interoperability, before expanding the scope of that agency or adhoc whatever-it-is to weigh in on the Great Decentralization Debates of 2019?”
Sat Aug 24 11:50:31 +0000 2019
(https://twitter.com/ChristopherA/status/1165229900325736449)
…This topic paper is exemplary of a powerful type of advance reading, the short opinion piece. It suggests that we should maybe forget the debate of rubric for decentralization but instead define rubric for interoperability, neutrality and industry fairness.
Sat Aug 24 11:53:52 +0000 2019
(https://twitter.com/ChristopherA/status/1165230744035180545)
TOPIC Terminology KEY CONCEPT As new groups join our community, how do we create a common vocabulary “that is actually useful, i.e. that within a given context, people demonstrably have the same understanding of (a coherent set of) term(s)” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/terminology.md
Sat Aug 24 12:00:19 +0000 2019
(https://twitter.com/ChristopherA/status/1165232364223488001)
…The topic paper goes on to suggest that during #RWOT9 we form a group that creates “a (generic) terminology process (at the same time developing the terminology for that process), selects one or two topics and use them to create a (first/draft) terminology for that topic”
Sat Aug 24 12:04:44 +0000 2019
(https://twitter.com/ChristopherA/status/1165233475185561600)
…As an example, the author also submitted an interesting terminology document with only the definitions, no terms. This invites other communities in our ecosystem to offer up what they terminology they use for the same concepts. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Terminology%20for%20Agent_Hub-Related%20Identity%20Concepts.pdf
Sat Aug 24 12:09:52 +0000 2019
(https://twitter.com/ChristopherA/status/1165234767198965761)
TOPIC Using Verifiable Claims as a Proof of Ownership for Blockcerts KEY CONCEPTS Blockcerts predate the DID/VC specs, so transitionally how can they use a Verifiable Credential from a recipient to prove ownership of a Blockcert needing verification? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Using%20Verifiable%20Claims%20as%20a%20Proof%20of%20Ownership%20for%20Blockcerts.md
Sat Aug 24 12:14:57 +0000 2019
(https://twitter.com/ChristopherA/status/1165236049003438080)
…the remainder of the paper specifies how this link between Blockcerts & DID/VCs can be accomplished, using a BTCR DID and some examples from our last BTCR hackathon as examples.
Sat Aug 24 12:17:51 +0000 2019
(https://twitter.com/ChristopherA/status/1165236779714150400)
This paper is not only a good example of something that could inform future specs, it is a prime candidate for coding a Proof of Concept during #RWOT9 — not all collaborative teams have to do a white paper, instead code is an equally good artifact of our work together.
Sat Aug 24 12:20:33 +0000 2019
RT @ChristopherA: TOPIC Using Verifiable Claims as a Proof of Ownership for Blockcerts KEY CONCEPTS Blockcerts predate the DID/VC specs, so…
Sat Aug 24 12:22:35 +0000 2019
RT @ChristopherA: TOPIC Terminology KEY CONCEPT As new groups join our community, how do we create a common vocabulary “that is actually us…
Sat Aug 24 12:22:40 +0000 2019
RT @ChristopherA: TOPIC Supreme Court for decent and interop KEY CONCEPT “Flashy, jokey title for a boring, ugly, uncomfortable topic– com…
Sat Aug 24 12:22:46 +0000 2019
(https://twitter.com/ChristopherA/status/1165237458553827328)
So this wraps another 6 topics reviewed for #RWOT9, another 39 to go. In the 11 so far you can see a good requisite variety of people that we have in the #RWOT community. Not only identity technologists & developers, but doctors, financial inclusion advocates, educators & more.
Sat Aug 24 12:47:08 +0000 2019
For over 10 years when I described how the Certificate Authority system I helped establish with SSL/TLS went wrong, I’d point to the Kazakhstan CA in every browser and ask “Why?” If you manually deleted it, it would come back. https://www.internetsociety.org/news/statements/2019/internet-society-concerns-kazakhstan-encryption
Sat Aug 24 14:01:12 +0000 2019
Replying to @caruanab
That is the hope and plan of the #RebootingWebOfTrust community.
Sat Aug 24 14:28:32 +0000 2019
8 days until #RWOT9 in Prague. Here are my notes on the next set of 5 topic & advance reading papers https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/
Sun Aug 25 20:20:06 +0000 2019
(https://twitter.com/ChristopherA/status/1165720529585811457)
TOPIC Addressing DID Connection Man in the Middle Attacks KEY CONCEPT In decentralized architectures trust is not binary true/false. Thus avoiding MitM attacks as you bootstrap into a web of trust is critical. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/addressing-MITM-attacks.md
Sun Aug 25 20:25:57 +0000 2019
(https://twitter.com/ChristopherA/status/1165722001937485825)
…The paper briefly discusses establishing TOFU (trust on first use) for a new DID by one of two methods, an out-of-band communication confirmation such as a hash, or a verifiable credential from someone you already trust.
Sun Aug 25 20:30:24 +0000 2019
(https://twitter.com/ChristopherA/status/1165723118020759557)
…”For example, a randomart image could be embedded into a QR code and then the randomart image could be displayed on the users device as well. The user would then be required to verify the image displayed on the user’s device is the same as the one embedded in the QR code.”
Sun Aug 25 20:31:45 +0000 2019
(https://twitter.com/ChristopherA/status/1165723459755880455)
…This paper doesn’t dive deeply into the problem space here and I might have some quibbles with some specifics, but the point of this kind of paper is an expression of interest that this topic should be dived into more deeply at #RWOT9.
Sun Aug 25 20:34:20 +0000 2019
(https://twitter.com/ChristopherA/status/1165724110430842880)
TOPIC Analysis of Verifiable Credential Protocols for Issuer Interactions KEY CONCEPT To get a VC, you have to request one from an issuer. Two different proposals are covered in this paper, one a more static manifest, the other a more dynamic marketplace. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/vc_protocols_issuer.md
Sun Aug 25 20:40:41 +0000 2019
(https://twitter.com/ChristopherA/status/1165725707886088193)
…This paper is just a beginning, more of a skeleton to be filled out if this topic is selected for more iteration at #RWOT9. I appreciate that they start with an analysis of 2 different approaches. This area is an important next step now that VCs are becoming a formal standard.
Sun Aug 25 20:46:18 +0000 2019
(https://twitter.com/ChristopherA/status/1165727123081965568)
…”the process of presenting…is often not initialized by the Holder of the Credential, but rather requested by the verifier to fulfill a specific need. Therefore, the process is often triggered by a Verifier requesting a specific Credential.”
Sun Aug 25 20:50:13 +0000 2019
(https://twitter.com/ChristopherA/status/1165728105207668741)
TOPIC Building Blocks for Sovereign P2P Identity KEY CONCEPT Many other DID architectures offer “multi-authoritative rather than a single authority” decentralization, but Holochain’s approach to identity is more Peer-to-Peer in design. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/building-blocks-sovereign-p2p-identity.md
Sun Aug 25 20:56:50 +0000 2019
(https://twitter.com/ChristopherA/status/1165729770673512449)
…“scalable by eliminating the high overhead involved with maintaining global consensus & constructing absolute time sequencing. Real-world identity works fine without requiring either of those constraints, digital identity should also be able to be constructed without them.”
Sun Aug 25 20:58:09 +0000 2019
(https://twitter.com/ChristopherA/status/1165730103604723712)
…”Holochain operates less like a global state blockchain, and more like git plus BitTorrent. Each node…signs any actions it originates to a local hashchain (providing an immutable sequence of local state changes) then publishes entries from their chain to a shared ledger space”
Sun Aug 25 21:00:19 +0000 2019
(https://twitter.com/ChristopherA/status/1165730650357256192)
…”Every application…functions as its own P2P encrypted network. The network ID is the SHA-256 hash of the application code as compiled to WASM (also called the DNA of the app). And the address space of network nodes and data, is the SHA-256 hash of the data…”
Sun Aug 25 21:02:24 +0000 2019
(https://twitter.com/ChristopherA/status/1165731172829319170)
…”…This makes for an extremely large address space (about 1.34e+154) with no top level namespace to create artificial scarcity or encourage name squatting. This should be plenty of elbow room for identity applications and other dApps.”
Sun Aug 25 21:03:04 +0000 2019
(https://twitter.com/ChristopherA/status/1165731340668592128)
…Paper continues with details on Holochain’s runtime called Conductor, and its key management architectures, how it handles multiple personas and profiles per person.
Sun Aug 25 21:06:47 +0000 2019
(https://twitter.com/ChristopherA/status/1165732277340528641)
…IMHO the best thing about Holochain is that they committed to implementing this architecture very differently than those based on the now more traditional permissionless or permissioned blockchains. IMHO we need this “new blood” to challenge some of our assumptions.
Sun Aug 25 21:10:43 +0000 2019
(https://twitter.com/ChristopherA/status/1165733266399399936)
TOPIC Combining Verifiable Credentials and Zero Knowledge Proof Systems KEY CONCEPT This paper is about beginning implementation of a library to support zkp anonymous Verifiable Credentials. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/verifiable-credentials-and-zero-knowledge-proof-systems.md
Sun Aug 25 21:15:43 +0000 2019
(https://twitter.com/ChristopherA/status/1165734524564791297)
…This advance reading is another example of a topic paper to express interest and support for a joining with others to collaborate at #RWOT9, and in this case not to do a paper but code. There is a zkp library in the Sovrin ecosystem but it is important we have another.
Sun Aug 25 21:19:09 +0000 2019
(https://twitter.com/ChristopherA/status/1165735386640977929)
TOPIC Concerns for minorities in a Web of Trust KEY CONCEPT We continue to need more input in our designs of decentralized architectures to address the needs of marginalized groups. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/concerns-for-minorities.md
Sun Aug 25 21:24:47 +0000 2019
(https://twitter.com/ChristopherA/status/1165736806442242049)
…”while Joram and Amira are both very tech-spec focused papers, I do believe that there’s space here for a less technical approach in order for us to help grasp what aspects and angles may still be missing from our current conversation.”
Sun Aug 25 21:26:11 +0000 2019
(https://twitter.com/ChristopherA/status/1165737156532473856)
…”Different minority groups have different needs, and they can’t all be addressed with one simple solution. What we need to do is find a way to address those needs, in their own time and space.”
Sun Aug 25 21:27:05 +0000 2019
(https://twitter.com/ChristopherA/status/1165737382986993664)
…”this paper wants to begin by mapping out some of those issues, so we have base to stand on and continue working from.”
Sun Aug 25 21:27:58 +0000 2019
(https://twitter.com/ChristopherA/status/1165737606581293057)
…This paper asks an important question — “Is a Web of Trust reliable for marginalized groups? Or does it require you to be part of a majority group in order for it to work properly?”
Sun Aug 25 21:29:00 +0000 2019
(https://twitter.com/ChristopherA/status/1165737866271571968)
I appreciate that this kind of topic continues to be presented before all the #RWOT community, going back to the refugee use case from our first design workshop. How does our community address the needs of all, not just of those in power or those with easier access to power!
Sun Aug 25 21:36:00 +0000 2019
(https://twitter.com/ChristopherA/status/1165739630312009728)
That wraps up my read-thru of another 5 #RWOT9 advance topic papers. A few last minute ones have been added, but I still plan to finish and highlight all of them in the coming week. We will use them in Prague as input for our collaborative choices of what to focus on F2F.
Sun Aug 25 21:43:20 +0000 2019
RT @ChristopherA: TOPIC Addressing DID Connection Man in the Middle Attacks KEY CONCEPT In decentralized architectures trust is not binary…
Sun Aug 25 21:44:00 +0000 2019
RT @ChristopherA: TOPIC Analysis of Verifiable Credential Protocols for Issuer Interactions KEY CONCEPT To get a VC, you have to request on…
Sun Aug 25 21:44:04 +0000 2019
RT @ChristopherA: TOPIC Building Blocks for Sovereign P2P Identity KEY CONCEPT Many other DID architectures offer “multi-authoritative rath…
Sun Aug 25 21:44:09 +0000 2019
RT @ChristopherA: TOPIC Combining Verifiable Credentials and Zero Knowledge Proof Systems KEY CONCEPT This paper is about beginning impleme…
Sun Aug 25 21:44:18 +0000 2019
RT @ChristopherA: TOPIC Concerns for minorities in a Web of Trust KEY CONCEPT We continue to need more input in our designs of decentralize…
Sun Aug 25 21:44:22 +0000 2019
Replying to @caruanab
I think it is possible to begin, especially if you are tech savvy. Own your own domain and host as many of your own services as you can. Imperfect, but perfection is the enemy of the good. Move away from powerful players like Google. Start using Tor. Support $ all these efforts.
Sun Aug 25 21:49:08 +0000 2019
A week before #RWOT9 in Prague, 35 more advance reading & topic papers to review. Another 5 today. This is a great way too get a feel for the current edges of decentralized identity technologies and trends. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/
Mon Aug 26 12:28:47 +0000 2019
(https://twitter.com/ChristopherA/status/1165964304782434304)
TOPIC X.509 DID method—Decentralising PKI starting with a X.509 DID method, KEY CONCEPT Traditional and federated PKI use X.509 certificates. Can we ease transition from this older architecture by creating a new DID Method? Are there other advantages? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/X.509-DID-Method.md
Mon Aug 26 12:35:22 +0000 2019
(https://twitter.com/ChristopherA/status/1165965961285066754)
…”We propose using an X.509 DID method or X.509 DID submethod in which the DID itself contains the fingerprint of the X.509 certificate used for signing the issued verifiable credential data.”
Mon Aug 26 12:37:46 +0000 2019
(https://twitter.com/ChristopherA/status/1165966563700355073)
…”This could be a new DID method, or it could be a submethod with which existing methods could optionally provide a way to use existing X.509 certificates to sign credentials.”
Mon Aug 26 12:38:20 +0000 2019
(https://twitter.com/ChristopherA/status/1165966709829832705)
…”Note that a VC can easily be transformed into an ETSI TS 103 171 3 compliant document so for instance a XaDES document by adding the X.509 public keys from the one that is used for signing to the PKI root certificate.…”
Mon Aug 26 12:39:46 +0000 2019
(https://twitter.com/ChristopherA/status/1165967067301994496)
…”…This enables people within the EU to use a verifiable credential issued with this method to proof facts about themselves across borders within the EU and which all countries are bound to accept due to eIDAS regulation.”
Mon Aug 26 12:40:31 +0000 2019
(https://twitter.com/ChristopherA/status/1165967067301994496)
…”X.509 DID’s are a good way for entities that do not represent natural persons, so-called legal persons to refer to themselves in a verifiable manner using existing systems in place. These DID’s themselves are not considered personal data in relation to the GDPR”
Mon Aug 26 12:42:18 +0000 2019
(https://twitter.com/ChristopherA/status/1165967704483934208)
…”Waardepapieren project in the Netherlands is aiming to use X.509 DID’s to have municipalities issue all kinds of valid proofs, not to be used for identification of a holder, in a digital way instead of issuing in print on specific watermarked paper as is done until now.”
Mon Aug 26 12:43:47 +0000 2019
(https://twitter.com/ChristopherA/status/1165968080746557442)
TOPIC Keeping Unwanted Messages off the Fediverse KEY CONCEPT This paper proposes a number of techniques to leverage DID & Verifiable Credentials architectures to discourage spam in ActivityPub systems such as Mastadon. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/ap-unwanted-messages.md
Mon Aug 26 12:49:10 +0000 2019
(https://twitter.com/ChristopherA/status/1165969433178902528)
…Though not technically part of the ActivityPub standard, one of the more powerful tools to avoid for this is authentication using HTTP Signatures, which is being upgraded to leverage DIDs (a different paper).
Mon Aug 26 12:53:45 +0000 2019
(https://twitter.com/ChristopherA/status/1165970587325534209)
…”Due to these and other concerns over sensitive information leaking to third parties, we suggest that Followers and Following collections not generally be made public.”
Mon Aug 26 12:54:41 +0000 2019
(https://twitter.com/ChristopherA/status/1165970823418658817)
…”In most ActivityPub implementations, an Actor’s inbox is simply a URL endpoint specific to the actor, e.g. https://example.com/bob/inbox. While convenient, we propose that servers should be using Object Capabilities model by which Inboxes are a capability handed out by a server.”
Mon Aug 26 12:55:49 +0000 2019
(https://twitter.com/ChristopherA/status/1165971108786561024)
…”We propose to extend this validation with a second layer of identity validation through the use of Pet Names. The Pet Names proposal presented in Rebooting Web of Trust 201817 has a secondary property of being able to be used as simplified trust mechanism.”
Mon Aug 26 12:57:29 +0000 2019
(https://twitter.com/ChristopherA/status/1165971526858018816)
…”we are concerned that the transitive properties of block lists may have unintended consequences or be used as a vector for attack or denial of service. If services adopt each other’s blocklists without review, they may miss out on messages that they might wish to recieve.”
Mon Aug 26 12:58:36 +0000 2019
(https://twitter.com/ChristopherA/status/1165971809541529601)
…There are a number of other suggestions for ActivityPub in this paper and “the suggestions made in this proposal are meant to be used in conjunction with one another for maximum efficacy.“
Mon Aug 26 13:01:15 +0000 2019
(https://twitter.com/ChristopherA/status/1165972473772478465)
TOPIC Why we must ask the Why of Identity KEY CONCEPT In the tradition of previous #RWOT white papers, this paper dives into the challenge of why identity as a term in our ecosystem is so hard to define. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/ask-why.md
Mon Aug 26 13:06:42 +0000 2019
(https://twitter.com/ChristopherA/status/1165973846354210822)
…”Identity continues to be bedevilled by conflicting language and definitions of what should be simple and understandable terms. An understandable reaction to this is to define or catalogue the various terms, in the hope that confusion disappears and consensus emerges…”
Mon Aug 26 13:07:36 +0000 2019
(https://twitter.com/ChristopherA/status/1165974074641850368)
…”…Yet even this has not seemingly aided the sector. Why is this? One possible cause is a focus on WHAT and HOW rather than WHY…Without a focus on WHY, we techies are left interpreting it from our own biases.”
Mon Aug 26 13:08:52 +0000 2019
(https://twitter.com/ChristopherA/status/1165974390758158336)
…”Such a consensual approach should be obviously good, but I have a nagging doubt. When I formulated the 4 schools or types of identity (state, self, corporate, community), I was not thinking of inclusion, I was expressly intending to exclude”
Mon Aug 26 13:09:52 +0000 2019
(https://twitter.com/ChristopherA/status/1165974645859856386)
…”without a strong narrative as to WHY, we are ungrounded. It doesn’t help to know HOW to build it if our foundations are sand. The castle of Identity, to be of any use whatsoever, must be founded on the strongest rock of understanding, of WHY”
Mon Aug 26 13:10:58 +0000 2019
RT @ChristopherA: TOPIC X.509 DID method—Decentralising PKI starting with a X.509 DID method, KEY CONCEPT Traditional and federated PKI use…
Mon Aug 26 13:11:37 +0000 2019
RT @ChristopherA: TOPIC Keeping Unwanted Messages off the Fediverse KEY CONCEPT This paper proposes a number of techniques to leverage DID…
Mon Aug 26 13:11:42 +0000 2019
RT @ChristopherA: TOPIC Why we must ask the Why of Identity KEY CONCEPT In the tradition of previous #RWOT white papers, this paper dives i…
Mon Aug 26 13:11:48 +0000 2019
(https://twitter.com/ChristopherA/status/1165974918720315398)
TOPIC Datashards: secure storage primitives for the web KEY CONCEPT Now that we have DIDs & DID documents, this topic paper proposes URIs to represent private, encrypted storage that can live in a variety of locations. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/datashards-rationale.md
Mon Aug 26 13:16:16 +0000 2019
(https://twitter.com/ChristopherA/status/1165976253796626432)
…Privacy problem in content addressable systems: “Any data store can inspect & observe all contents, so privacy does not exist on this layer. This is even worse in a peer to peer system, because then the network cannot help spread content without being able to see all content.”
Mon Aug 26 13:19:18 +0000 2019
(https://twitter.com/ChristopherA/status/1165977018535690240)
…”This ability to see the content you are helping to distribute is also a liability; a node wishing to be a good citizen and helping distribute content along the network may find that it is storing undesirable material in the clear. Sometimes it is best to know less.”
Mon Aug 26 13:19:45 +0000 2019
(https://twitter.com/ChristopherA/status/1165977129831600129)
… Datashards ”come from chopping up & symmetrically encrypting content into uniform-sized chunks/shards are content-addressed “shard URNs”. The shards may be distributed amongst storage & distribution providers without knowledge by those parties as to what the contents contain.”
Mon Aug 26 13:21:18 +0000 2019
(https://twitter.com/ChristopherA/status/1165977520447119361)
…”Datashard capabilities come in two flavors (and two new URI schemes): idsc: (Immutable DataShard Capability) for fixed/immutable content. Builds on shard URNs. mdsc: (Mutable DataShard Capability) for mutable/updateable content. Builds on Immutable Datashard Capabilities.”
Mon Aug 26 13:22:12 +0000 2019
(https://twitter.com/ChristopherA/status/1165977748604633088)
There is a lot more depth in this proposal, and I particularly like the use of ocaps for access control. This paper is one of about 9 different papers submitted about encrypted storage approaches, clearly the hot topic for this #RWOT9 design workshop.
Mon Aug 26 13:56:47 +0000 2019
RT @ChristopherA: TOPIC Datashards: secure storage primitives for the web KEY CONCEPT Now that we have DIDs & DID documents, this topic pap…
Mon Aug 26 13:57:30 +0000 2019
(https://twitter.com/ChristopherA/status/1165986450514407430)
TOPIC Decentralized unique anonymous identity KEY CONCEPT This paper proposes using “proof of the humanness and uniqueness by running a collective simultaneous online AI-hard Turing test”. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/decentralized-unique-anonymous-identity.md
Mon Aug 26 14:08:03 +0000 2019
(https://twitter.com/ChristopherA/status/1165989286363058176)
…”a language-neutral AI-hard test that conveys narrative rather than semantic meaning. A flip, “Filter for Live Intelligent People,” utilizes four images. To solve a flip, the participant chooses between two sequences of these images, only one of which makes narrative sense.“
Mon Aug 26 14:11:48 +0000 2019
(https://twitter.com/ChristopherA/status/1165990231180365830)
…”The uniqueness of participants is proven by the fact that they must solve flips synchronously. Flips are decrypted at the same time world wide. A single person is not able to validate herself multiple times because of the limited timeframe for the submission of answers.”
Mon Aug 26 14:12:36 +0000 2019
(https://twitter.com/ChristopherA/status/1165990429529010176)
…Use cases for attestations of human uniqueness include fair voting, free speech, serverless messaging, permissioned marketing, air drops, and UNI (universal basic income).
Mon Aug 26 14:17:01 +0000 2019
(https://twitter.com/ChristopherA/status/1165990231180365830)
…Different approaches to sybil-proofing pseudoanonymous identies, what I call “Proof of Unique Personhood” has been a regular proposed topic at #RWOT, but never has risen to be a collaborative white paper. Hopefully there is sufficient critical mass to scope one at #RWOT9.
Mon Aug 26 14:21:51 +0000 2019
(https://twitter.com/ChristopherA/status/1165992756918939654)
That’s all of my advance readings for today. 30+ to go for #RWOT9, but I’m on track to complete before we begin our design workshop next Tuesday in Prague.
Mon Aug 26 14:25:57 +0000 2019
RT @ChristopherA: TOPIC Decentralized unique anonymous identity KEY CONCEPT This paper proposes using “proof of the humanness and uniquenes…
Mon Aug 26 14:26:08 +0000 2019
RT @socrates1024: Illinois is literally overflowing with blockchain-relevant courses, inc:
- Consensus protocols https://sites.google.com/view/cs598lr/home…
Tue Aug 27 19:06:32 +0000 2019
6 days until the #RWOT9 design workshop in Prague. Of 50+ advance reading and topic papers https://github.com/WebOfTrustInfo/rwot9-prague/tree/master/topics-and-advance-readings I’ve read almost half, and expect to be half-way done today. Here are my summaries of the next 5.
Tue Aug 27 19:06:34 +0000 2019
(https://twitter.com/ChristopherA/status/1166426796587454464)
TOPIC DID Resolution collected diagrams KEY CONCEPT The DID Resolver task force has been puzzling through how to handle different DID methods at the same time, as well as address how to implement some of the capabilities possible with DID dereferencing. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/did-resolution-collected-diagrams.md
Tue Aug 27 19:12:32 +0000 2019
(https://twitter.com/ChristopherA/status/1166428299863740417)
…As someone who often presents about the DID architecture, this collection of explanatory images is quite useful. In particular, the subtleties of DID matrix parameters, dereferencing vs. resolving, etc. has been always been difficult. This paper offers the best explanation yet
Tue Aug 27 19:17:10 +0000 2019
(https://twitter.com/ChristopherA/status/1166429464710041605)
TOPIC did🐌 A DID Method for the Real World KEY CONCEPT “This DID Method specification started out as satire, but it occurred to us that exercises in mapping DID related concepts to offline or non-technical scenarios might actually be a useful educational tool.”
Tue Aug 27 19:19:24 +0000 2019
RT @ChristopherA: TOPIC DID Resolution collected diagrams KEY CONCEPT The DID Resolver task force has been puzzling through how to handle d…
Tue Aug 27 19:19:31 +0000 2019
(https://twitter.com/ChristopherA/status/1166430025782059016)
…”Prerequisites: This DID method assumes you already have a place to live. If you don’t, please consult wikipedia or legal counsel regarding your local regulations about purchasing, renting or squatting land and buildings and get somewhere to live before proceeding.”
Tue Aug 27 19:20:30 +0000 2019
(https://twitter.com/ChristopherA/status/1166430305974149121)
…”Generating the identifier: The snail identifier portion is generated from your IRL address. To generate, perform the following steps: Write down the details of where you live, starting from the most general to the most specific…”
Tue Aug 27 19:21:52 +0000 2019
(https://twitter.com/ChristopherA/status/1166430648418148354)
…”…You SHOULD also include any country- or region-specific codes, such as postal or zip codes. The last line SHOULD be your name. 2. Replace spaces with the + character. 3. Replace line breaks with a _ character. 3. Append this string to did
”
Tue Aug 27 19:22:57 +0000 2019
(https://twitter.com/ChristopherA/status/1166430921844822016)
…”Deactivate: You may wish to deactive your DID if you abandon society to live in the woods, are the victim of structural inequality which renders you homeless, or shuffle off this mortal coil…Take your paper DID Document in two hands. …Tear the DID Document into tiny pieces”
Tue Aug 27 19:24:47 +0000 2019
(https://twitter.com/ChristopherA/status/1166431383134359552)
…When I first read this it made me laugh, but though it is silly and has some insider jokes, it has some real value in its metaphors and analogies that are helpful people outside the identity space understand DIDs and related technologies.
Tue Aug 27 19:26:31 +0000 2019
RT @ChristopherA: TOPIC did🐌 A DID Method for the Real World KEY CONCEPT “This DID Method specification started out as satire, but it occur…
Tue Aug 27 19:26:39 +0000 2019
(https://twitter.com/ChristopherA/status/1166431819706896385)
TOPIC KEY Ecosystem Bootstrapping Via Notary VCs CONCEPT This paper observes that in current existing document collection and notarization processes there may be some value that DID/VCs can offer the notaries. This might ease bootstrapping into full DIDs. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/ecosystem-bootstrapping-via-notary-vcs.md
Tue Aug 27 19:31:52 +0000 2019
RT @ChristopherA: TOPIC KEY Ecosystem Bootstrapping Via Notary VCs CONCEPT This paper observes that in current existing document collection…
Tue Aug 27 19:32:02 +0000 2019
(https://twitter.com/ChristopherA/status/1166433166543990784)
…”The goal is to improve the footprint of…SSI technologies through verifiable credentials issued without the expectation that the subject maintains a wallet, controls a DID, or manages private-keys, and where the issuer of the credential is not the originator of the data.”
Tue Aug 27 19:33:26 +0000 2019
(https://twitter.com/ChristopherA/status/1166433557310521344)
…”The danger of not paying attention…is that the first-order trust in legislative compliance tools will go first to another style of technology, such as state-sanctioned credentials issued and managed fully by our glorious leaders and our benevolent corporate overlords.”
Tue Aug 27 19:34:53 +0000 2019
(https://twitter.com/ChristopherA/status/1166433923485851648)
…”Can we use SSI-like technology to get to a half-way point that begins to integrate WoT processes and existing document-vetting without requiring that a mature ecosystem emerge fully formed before it is first useful? I believe the answer is yes.”
Tue Aug 27 19:35:40 +0000 2019
(https://twitter.com/ChristopherA/status/1166434121700302848)
…”save a PDF of the receipt with a QR code that points to some digitally signed asset or credential with the option of downloading the digital asset. Cost remains…(low). Most importantly there is no lifelong commitment to guarding private keys, and no training required.”
Tue Aug 27 19:37:41 +0000 2019
(https://twitter.com/ChristopherA/status/1166434628875575297)
…”The key to this is the “discretion of the officer” and providing SSI and WoT technologies that enable such officials to arrive at the same decisions they would make today, but to arrive at them faster and with more safety and strong defensive auditability than before.”
Tue Aug 27 19:38:25 +0000 2019
(https://twitter.com/ChristopherA/status/1166434812317618176)
…”Focus on the notary changes the nature of the credential which is issued. The credential is no longer a direct, first-class claim by an issuer about a subject - it is a claim of observation, by a registered professional, of a document issued to a subject.”
Tue Aug 27 19:39:35 +0000 2019
(https://twitter.com/ChristopherA/status/1166434812317618176)
…I’m excited about looking at SSI through the needs of notaries, and seeing what may be possible with these ideas. I believe that Verifiable Credentials also underutilized the power of digital time stamps proofs, which could be quite useful in the hands of a notary.”
Tue Aug 27 19:41:47 +0000 2019
(https://twitter.com/ChristopherA/status/1166435106644512769)
It was just pointed out to me that I didn’t give the URL for the DID:Snail method satire that I described. It is at https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/didm-snail.md
Tue Aug 27 19:43:05 +0000 2019
(https://twitter.com/ChristopherA/status/1166435987171553280)
TOPIC Formal protocol verification for SSI KEY CONCEPT The process of proving code and protocols has been emerging out from academia into the real world. This paper proposes we should do begin this formal verification process for DIDs and SSI designs. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/formal_verification_for_ssi.md
Tue Aug 27 19:46:57 +0000 2019
(https://twitter.com/ChristopherA/status/1166436959239192576)
…”Even when best practices are followed during design and specification of such systems, security problems can still occur through unforeseen interactions. Simple protocols have been believed secure for a long time and found insecure only after tool-assisted formal analysis.”
Tue Aug 27 19:48:00 +0000 2019
(https://twitter.com/ChristopherA/status/1166437224277262341)
…”formal analysis has often been applied to already established standards and protocols; it has only recently been incorporated more into design processes, e.g., for TLS 1.3. Similarly, there is a great opportunity to incorporate formal verification into the SSI design process.”
Tue Aug 27 19:50:20 +0000 2019
(https://twitter.com/ChristopherA/status/1166437812771655681)
…”As a first step, we provide models of increasing complexity for DIDComm, agent-to-agent communication using peer DIDs” The topic paper then points to a longer formal proof at https://github.com/SvenHammann90/SSI/blob/master/RWOT_9/Topic_Paper_RWOT.md
Tue Aug 27 19:51:50 +0000 2019
(https://twitter.com/ChristopherA/status/1166437812771655681)
…This in an important area for our community. As a co-author of the TLS 1.0standard, I watched with interest TLS 1.3 get some significant value from bringing formal verification processes. I’m pleased that we are getting some of that expertise coming to #RWOT9, but we need more!
Tue Aug 27 19:54:03 +0000 2019
(https://twitter.com/ChristopherA/status/1166438189508300801)
TOPIC Islands, Tigers, and Bears, Oh My! KEY CONCEPT “Is there a risk of the VC ecosystem devolving into islands of incompatible VCs? In short, the answer is yes.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/islands.md
Tue Aug 27 19:58:42 +0000 2019
(https://twitter.com/ChristopherA/status/1166439919155318784)
…”Many of the properties in VCs are optional, and of the ones that are mandatory there is often flexibility in how they can be used…In short, the syntax is generic enough to support all these options, but it is NOT the case that every VC in existence will be verifiable”
Tue Aug 27 19:59:46 +0000 2019
(https://twitter.com/ChristopherA/status/1166440187322359808)
“The question for this paper, and for RWOT, is what, if anything, can or should be done about it? Stopping it is difficult, so one possibility is to consider ways to enable easy conversion from one format to another, or to enable low-cost converters.”
Tue Aug 27 20:00:41 +0000 2019
(https://twitter.com/ChristopherA/status/1166440417862266880)
…This is a short advance reading, but a very important topic, and potentially an existential one. I know that in my own work on implementing the DID BTCR method that it is easy to make VCs that work with our method, but as soon as we try to make them work elsewhere, it is hard.
Tue Aug 27 20:02:45 +0000 2019
RT @ChristopherA: TOPIC Islands, Tigers, and Bears, Oh My! KEY CONCEPT “Is there a risk of the VC ecosystem devolving into islands of incom…
Tue Aug 27 20:03:01 +0000 2019
(https://twitter.com/ChristopherA/status/1166440935787360257)
I’m done with another 5, for a total of 26 completed, leaving about half of the 50+ remaining to cover the rest of the week. 5 more tomorrow!
Tue Aug 27 20:04:15 +0000 2019
For everyone who is joining us in Prague for #RWOT9 (our ninth Rebooting the Web of Trust design workshop) I encourage you to read through this new primer. Even if you’ve been to one before, there are some slight changes (now 4 days but more breaks & “in the margins” activities). https://twitter.com/Appelcline/status/1166418148523794433
Wed Aug 28 06:19:14 +0000 2019
RT @webfoundation: “For digital ID to be meaningful for human development, it must — from the word go — be developed as a means of better f…
Wed Aug 28 06:34:01 +0000 2019
Replying to @JoukoSalonen and @Appelcline
No, that is exactly the type of thing we do. Have you read https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/rwot-primer.md yet?
Wed Aug 28 12:23:51 +0000 2019
Replying to @JoukoSalonen and @Appelcline
The exact choice of what papers/specs/code are decided collaboratively at the first day of the event based on who shows up. We’ve had interest in your topic in the past, but insufficient people from government to feel that we could have done it previously, but hopefully soon!
Wed Aug 28 13:05:59 +0000 2019
Replying to @JoukoSalonen and @Appelcline
Have you seen this advance reading topic paper submitted for #RWOT9? https://twitter.com/christophera/status/1165031725732257793?s=21
Wed Aug 28 13:08:48 +0000 2019
😡👎 Besides the basic privacy violation here, using the social network activity of friends to make quasi-judicial decisions about someone seems quite inappropriate and likely unscientific. As he was already filtered by Harvard as a promising student, he seemed a good prospect. https://twitter.com/SanaSaeed/status/1166326940292268033
Wed Aug 28 13:16:17 +0000 2019
The countdown to #RWOT9 in Prague continues, and my review of some more of our advance reading and topic papers that were submitted to help inform the community about our mutual interests and the “weak signals” of the edges of decentralized identity tech to collaborate on…
Wed Aug 28 16:54:40 +0000 2019
(https://twitter.com/ChristopherA/status/1166755990752178178)
TITLE Gently introducing DIDs to the Mastodon/ActivityPub Fediverse KEY CONCEPT Many in this community are joining us at #RWOT9 & this paper discusses how to transition their existing DNS-based actorIDs to use DIDs to allow portability between servers https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/fediverse-did-integration.md
Wed Aug 28 17:02:08 +0000 2019
(https://twitter.com/ChristopherA/status/1166757871104774145)
…”long term stability of a federated service crucially depends on persistent trust relations across all participants (developers, admins, users) that are not distorted by the implicit hierarchical structure of a centralized reference system, such as DNS.”
Wed Aug 28 17:03:02 +0000 2019
(https://twitter.com/ChristopherA/status/1166758097697816576)
…The original proposal for how the Fediverse might use DIDs was proposed back at #RWOT5 https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/activitypub-decentralized-distributed.md
Wed Aug 28 17:04:10 +0000 2019
(https://twitter.com/ChristopherA/status/1166758381048258560)
…”it left us wondering how to turn this into reality - how to change the base reference system of a large federated network, e.g. within the current mastodon fediverse?”
Wed Aug 28 17:05:41 +0000 2019
(https://twitter.com/ChristopherA/status/1166758766072729601)
…The Mastodon/ActivityPub/Fediverse community existed before #RWOT, but has aligned interests in decentralization. They are piggybacking their own event after #RWOT9 to collaborate and engage with us. I’m glad they will joining us to learn about DIDs & for us to learn from them.
Wed Aug 28 17:09:26 +0000 2019
(https://twitter.com/ChristopherA/status/1166759709677969418)
TOPIC The Current Status of the DID Specification KEY CONCEPT “a summary of the current state of work on the specification. It includes a rough categorization…with the goal of identifying actions which can be taken quickly” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/did-spec-current-status.md
Wed Aug 28 17:11:46 +0000 2019
(https://twitter.com/ChristopherA/status/1166760295144075265)
…”Major areas of ongoing discussion & work…1) Cleaning up introduction(s), overview, and similar…2) Matrix parameters - which should be included in the DID URI and which belong elsewhere 3) ‘clarify’…relationship with key management operations, definition of “proof purpose”…
Wed Aug 28 17:15:12 +0000 2019
(https://twitter.com/ChristopherA/status/1166761160269606914)
…”…representing services, making sure normative statements are testable 4) ‘discuss’ definition of DID controller, id for service and publicKey, What do/can/should DIDs identify?, Method-specific DID params, Empty method-specific-id, Key revocation: #96”
Wed Aug 28 17:17:56 +0000 2019
(https://twitter.com/ChristopherA/status/1166761160269606914)
…The DID specification was incubated at #RWOT, but is now moving along the W3C track toward international standard. I’m pleased that #RWOT can serve as a F2F coordination point for further discussions/clarifications.
Wed Aug 28 17:38:03 +0000 2019
(https://twitter.com/ChristopherA/status/1166761845602078720)
TOPIC Rubrics for Decentralization of DID Methods Creative Brief KEY CONCEPT This paper is a “creative brief” for how we might create a rubric for evaluating and comparing the decentralization qualities of real or potential DID Methods. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/rubrics.md
Wed Aug 28 17:42:53 +0000 2019
(https://twitter.com/ChristopherA/status/1166768127897669632)
…”Objectives: Present a set of rubrics for evaluating the decentralized character of any given DID Method. Explain how these rubrics help evaluate DID methods. Be concise and accessible.”
Wed Aug 28 17:43:46 +0000 2019
(https://twitter.com/ChristopherA/status/1166768347679207424)
…”Goals: Help standards collaborators make better decisions about what DIDs should enable and how they might do so. Help DID Method creators evaluate the trade offs in decentralizing their DID method. Help DID Method users to evaluate potential DID Methods”
Wed Aug 28 17:45:15 +0000 2019
(https://twitter.com/ChristopherA/status/1166768722956181505)
…Non-goals: This rubrics document explicitly is NOT about defining “a top-level metric for evaluating DID methods. No single metric can encapsulate all engineering trade offs. We reject singular metrics as oversimplified.”
Wed Aug 28 17:48:35 +0000 2019
(https://twitter.com/ChristopherA/status/1166769561355608064)
…NOT “a framework for certification, self- or otherwise. The intent is to enable a subjective, qualitative evaluation, not a rigorous, hard standard with specific measurable characteristics. Document readers will interpret the rubrics against their specific use cases.”
Wed Aug 28 17:49:07 +0000 2019
(https://twitter.com/ChristopherA/status/1166769694612840448)
…”It will not be exhaustive.…It will not directly provide guidance on DIDs or decentralization.…It will not provide direct guidance on what DID Methods should or should not be published in any particular registry.”
Wed Aug 28 17:50:19 +0000 2019
(https://twitter.com/ChristopherA/status/1166769997332516864)
…Call to action: we want people to “collaborate and communicate better about how DIDs and DID methods support decentralization.” “Avoid rabbit holes of decentralization in collaborative conversations. Instead, focus on the rubrics that most affect your desired outcomes.”
Wed Aug 28 17:53:02 +0000 2019
(https://twitter.com/ChristopherA/status/1166770681784274944)
…The topic of “what is decentralized” or “decentralized enough” has become a divisive topic in our community, especially as (IMHO) there can be no perfect decentralization (some forms of decentralization break others). I look forward to seeing the final rubric document evolve.
Wed Aug 28 17:55:12 +0000 2019
RT @ChristopherA: TITLE Gently introducing DIDs to the Mastodon/ActivityPub Fediverse KEY CONCEPT Many in this community are joining us at…
Wed Aug 28 17:55:37 +0000 2019
RT @ChristopherA: TOPIC The Current Status of the DID Specification KEY CONCEPT “a summary of the current state of work on the specificatio…
Wed Aug 28 17:55:42 +0000 2019
RT @ChristopherA: TOPIC Rubrics for Decentralization of DID Methods Creative Brief KEY CONCEPT This paper is a “creative brief” for how we…
Wed Aug 28 17:55:46 +0000 2019
(https://twitter.com/ChristopherA/status/1166771225231790080)
TOPIC Zion Key Management APIs and Social Key Recovery
KEY CONCEPT The new Exodus cell phone from HTC offers an SDK/API for developers to leverage its TrustZone secure hardware for key management. This paper gives an overview of that architecture. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/zion-sdks-skr.md
Wed Aug 28 18:20:37 +0000 2019
(https://twitter.com/ChristopherA/status/1166777622396833793)
…”The goal of HTC Exodus is to let you keep data—and blockchain currencies—private and secure on the device rather than in the cloud. And to maximize the capability of that, we believe open to the community is important. Therefore, we create the SDK sets for Zion Key Management”
Wed Aug 28 18:21:46 +0000 2019
(https://twitter.com/ChristopherA/status/1166777912403681281)
…”ZKMA…is a service which provides a way for developers to manage seed security built into HTC Exodus devices, which integrates Zion protection. All secure operations (input pin, display seed, sign transaction…) will be performed by the trusted OS and no secure data exposed”
Wed Aug 28 18:22:50 +0000 2019
(https://twitter.com/ChristopherA/status/1166778179312345089)
…”ZionVaultSDK…provides two major functions: Get crypto currency account address from Zion Vault. Request Zion Vault to sign a transaction…two approaches…Web base integration…Application base integration”
Wed Aug 28 18:24:40 +0000 2019
(https://twitter.com/ChristopherA/status/1166778642967539719)
…”Zion Social Key Recovery SDK…is an Android library that provides Java APIs for developers to integrate HTC Zion Vault’s Social Key Recovery (SKR) feature into their apps. 3rd party apps integrating Zion-SKR-SDK will be able to use SKR to backup or restore their…(HD Keys)”
Wed Aug 28 18:25:48 +0000 2019
(https://twitter.com/ChristopherA/status/1166778925072244736)
…Almost all of the current POCs and pilots for DIDs implement key management in the user space of their device, rather than the best practice of using hardware. I’m pleased to see some discussion about good APIs for communicating with secure cell phone hardware.
Wed Aug 28 18:28:12 +0000 2019
(https://twitter.com/ChristopherA/status/1166779530037616642)
TOPIC Mandates and Delegation KEY CONCEPT The Dutch government has a defined a concept of “mandate” and “delegation” that is potentially relevant to DIDs and Verifiable Credentials. This paper proposes the creation of specifications for mandates.
https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/mandates-and-delegation.md
Wed Aug 28 18:33:26 +0000 2019
(https://twitter.com/ChristopherA/status/1166780845711155202)
…Under Dutch law a “mandate means: the authority to take decisions in the name of an administrative body”, and “A decision taken by the mandatee within the limits of his authority counts as a decision of the mandator”
Wed Aug 28 18:36:32 +0000 2019
(https://twitter.com/ChristopherA/status/1166781629429424128)
…”Delegation is understood to mean: the transfer by a governmental body of its power to take decisions to another person who exercises this responsibility under his own responsibility”
Wed Aug 28 18:37:21 +0000 2019
(https://twitter.com/ChristopherA/status/1166781832131690497)
…”There are very many different ways in which mandates can be created, used, updated, disputed end deleted/revoked.” …
Wed Aug 28 18:39:24 +0000 2019
(https://twitter.com/ChristopherA/status/1166782347531956231)
…”Guardianship is in order when someone is incapable of taking sufficient care for him/herself. Examples include small children, and people with certain mental and/or physical disabilities.…”
Wed Aug 28 18:39:55 +0000 2019
(https://twitter.com/ChristopherA/status/1166782478444576768)
…”…Under such conditions, a judge may be asked to install guardianship, which, if awarded, results in a set of obligations and the appointment of a natural person or a legal person (called the ‘guardian’) that will be held accountable for their realization.”
Wed Aug 28 18:40:16 +0000 2019
(https://twitter.com/ChristopherA/status/1166782568928292865)
…There is a lot of subtlety in these distinctions around guardianship, stewardship, delegation & mandates that I don’t quite understand. It is clear that as a community if we want to support this in a self-sovereign architecture that we need further dialogue—this is a beginning.
Wed Aug 28 18:42:31 +0000 2019
(https://twitter.com/ChristopherA/status/1166783133632684035)
Another 5 advance reading topic papers reviews completed, about ~25 remaining to cover in the next 5 days. I hope that these summaries are useful to you, even if you are not coming to #RWOT9 in Prague next week.
Wed Aug 28 18:44:41 +0000 2019
RT @ChristopherA: TOPIC Zion Key Management APIs and Social Key Recovery
KEY CONCEPT The new Exodus cell phone from HTC offers an SDK/API f…
Wed Aug 28 18:45:52 +0000 2019
RT @ChristopherA: TOPIC Mandates and Delegation KEY CONCEPT The Dutch government has a defined a concept of “mandate” and “delegation” that…
Wed Aug 28 18:45:58 +0000 2019
Replying to @JoukoSalonen and @Appelcline
Also this one: https://twitter.com/ChristopherA/status/1166780845711155202?s=20
Wed Aug 28 18:46:59 +0000 2019
@brynosaurus There are now two topic papers submitted on topic of anti-Sybil proofs-of-personhood for #RWOT9 in Prague next week. Any chance you can come last minute? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/decentralized-unique-anonymous-identity.md https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/Decentralized-unique-identity-via-graph-based-Sybil-detection-on-a-peer-to-peer-credit-network.md
Wed Aug 28 19:58:45 +0000 2019
I personally believe this type of sharing should be banned until there are firm standard for “Quis custodiet ipsos custodes?” or “Who watches the watchers”.
I’m a big fan of my local police force, but I’ve also lived places where that was not true. https://www.washingtonpost.com/technology/2019/08/28/doorbell-camera-firm-ring-has-partnered-with-police-forces-extending-surveillance-reach/
Thu Aug 29 05:40:19 +0000 2019
Once again, the topic of blockchain voting is in the news. The best quote (and article) on this topic is “To sum it up, using Blockchain for voting solves a small part of the problem with an unnecessarily big hammer.” by @benadida. The rest is hard https://benlog.com/2017/12/28/blockchain-and-voting/
Thu Aug 29 05:50:38 +0000 2019
#RWOT9 begins in Prague on Tuesday, giving me 5 more days to share the rest of these quick summaries and my thoughts on the 50+ topics that have been shared as advance readings for our design workshop. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/README.md
Thu Aug 29 18:56:16 +0000 2019
(https://twitter.com/ChristopherA/status/1167148980289060864)
TOPIC Establishing level of assurance with verifiable credentials and the need for a human centered design exploration KEY CONCEPT Previous generations of digital identity systems relied on trusting a single issuer. What if we rely instead on many issuers? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/level-of-assurance-crendtials.md
Thu Aug 29 18:56:52 +0000 2019
(https://twitter.com/ChristopherA/status/1167149131338588161)
…”we would like to explore the idea of establish levels of assurance, which will no longer be tied to single issuance processes, but also to a multi-source verification processes.”
Thu Aug 29 18:57:16 +0000 2019
(https://twitter.com/ChristopherA/status/1167149233968951297)
…”As verifiers are almost always also issuers, there is a common interest in keeping costs of such systems down, driving the development of open standards to cater to interoperability rather than differentiating on individual levels of assurance”
Thu Aug 29 18:57:24 +0000 2019
(https://twitter.com/ChristopherA/status/1167149267108208640)
…”start the conversation around how could a distributed reputation system of issuers might prove as useful as their counterparts for centralized systems (ebay, amazon, etc.) and whether and how they can best be used when establishing levels of assurances”
Thu Aug 29 18:58:07 +0000 2019
(https://twitter.com/ChristopherA/status/1167149449392476160)
…”to establishing a high level of assurance of verifiable credentials, the reputational distributed system needs to be reliable & robust against liar issuers but as well incorporate in the protocol the capability to ask for extra credentials if…(assurance level not) reached.”
Thu Aug 29 19:00:09 +0000 2019
(https://twitter.com/ChristopherA/status/1167149959726206976)
…”This network effect fundamentally shifts the power balance from centralized issuers, or federated identity managers, towards individual ID holders. The trade-off here is 1) the ease of compliance and 2) automation of services across contexts in an ever expanding ecosystem.”
Thu Aug 29 19:00:28 +0000 2019
(https://twitter.com/ChristopherA/status/1167150040122568708)
…”Putting the ID holder at the center of an identity system comes with great opportunity, but also introduces new risks and barriers to adoption. Many of these are non-technical and such, should be explored in multi-disciplanary way.”
Thu Aug 29 19:00:52 +0000 2019
(https://twitter.com/ChristopherA/status/1167150139842187264)
…”How to prevent the unwanted sharing of credentials in a case where there is a power difference between a service provider and a citizen that would like to have access to a service? Is there such a thing as freely given, informed consent?”
Thu Aug 29 19:01:07 +0000 2019
(https://twitter.com/ChristopherA/status/1167150203100684288)
TOPIC Decision Making with Verifiable Credentials KEY CONCEPT “How to use trusted sources of data to learn about the ‘other’ side, or counterparty, and how to justifiably decide whether or not to engage…with the said counterparty.”
https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/decision-making-with-verifiable-credentials.md
Thu Aug 29 19:57:24 +0000 2019
(https://twitter.com/ChristopherA/status/1167164364807450626)
…”Customer assessment forms a large component of the mortgage application process…The phases of information gathering and decision making are best not viewed as separate but as feeding one another in a cycle, until a final decision can be made with enough confidence”
Thu Aug 29 19:57:55 +0000 2019
(https://twitter.com/ChristopherA/status/1167164496227590146)
…”Our motivation is the desire to improve current mortgage decisioning and ultimately the whole property transaction process resulting in property purchase/sale.”
Thu Aug 29 19:58:13 +0000 2019
(https://twitter.com/ChristopherA/status/1167164572995858432)
…”Areas we would like to see improvements in mortgage decisioning are as follows: speed & ease of use…transparency…minimal intermediaries…accuracy…collaboration”
Thu Aug 29 19:59:00 +0000 2019
(https://twitter.com/ChristopherA/status/1167164769532555264)
…”“From a decision requirement we can derive a decision strategy that describes how we can reach a decision outcome that satisfies the requirement. A decision strategy consists of information requirements and decision logic.”
Thu Aug 29 19:59:39 +0000 2019
(https://twitter.com/ChristopherA/status/1167164934079287297)
…”Multiple decision strategies can exist for the same decision requirement where some will be better than others in different circumstances.”
Thu Aug 29 19:59:57 +0000 2019
(https://twitter.com/ChristopherA/status/1167165008939311105)
…This paper goes on to detail decision making using Verifiable Credentials as well as support decision transparency. This use case is well thought out and I look forward to seeing how it evolves.
Thu Aug 29 20:01:26 +0000 2019
(https://twitter.com/ChristopherA/status/1167165379623493632)
TOPIC Preventing Transferability with ZKP-based Credentials KEY CONCEPT Some claim ZKPs are unsafe because they can be transfered by also sharing the link secret.This paper presents how to safeguard ZKP credentials to prevent abuse. https://github.com/weboftrustinfo/rwot9-prague/blob/master/topics-and-advance-readings/zkp-safety.md
Thu Aug 29 20:08:00 +0000 2019
(https://twitter.com/ChristopherA/status/1167167034838401026)
…The paper begins with a brief overview of what a ZKP-based credential is, then shares several different techniques to allow for adjustment of anonymity, vulnerability, and transferability.
Thu Aug 29 20:08:14 +0000 2019
(https://twitter.com/ChristopherA/status/1167167092753391617)
…Techniques are “Richly contextualized presentation requests…Prevent Link Secret Reuse…Require Link Secret Continuity…Commit a DID to a Link Secret…Biometrics(strong disclosure, weak disclosure, permuted disclosure)…Provisional Anonymity…LinkSecret Bond…Financial Escrow”
Thu Aug 29 20:08:33 +0000 2019
(https://twitter.com/ChristopherA/status/1167167170696097793)
…”ZKP-based approaches to credentials are undoubtedly imperfect, because they are young. However, there is no evidence, either anecdotal or rigorous, to suppose that ZKPs are inherently, uniquely vulnerable to trust problems. (there is a) long & rich history of clever solutions.
Thu Aug 29 20:09:52 +0000 2019
(https://twitter.com/ChristopherA/status/1167167503660965888)
…”The best way to serve community interests with respect to ZKPs and credentials is not to fear them. It’s to embrace them, and get on with the business of making them better and using them well.”
Thu Aug 29 20:10:09 +0000 2019
(https://twitter.com/ChristopherA/status/1167167573126995968)
TOPIC Secure Data Hubs KEY CONCEPT “We store a significant amount of sensitive data online such as personally identifying information…The data that we store should be encrypted in transit and at rest but is often not protected in an appropriate manner.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/secure-data-hubs.md
Thu Aug 29 20:11:46 +0000 2019
(https://twitter.com/ChristopherA/status/1167167980393906177)
…There are other projects that are working on various approaches for encrypting data at rest “It is one of the goals of the Secure Data Hubs specification to find commonalities between these projects (and others) and attempt to standardize them.”
Thu Aug 29 20:11:59 +0000 2019
(https://twitter.com/ChristopherA/status/1167168035377094657)
…”The simplest and most straightforward (and correct) solution is to decouple the application from storage…One could argue that Operating Systems vendors were the first to get this right in the 1970s, 1980s, and 1990s. File systems of that era separated the storage between…”
Thu Aug 29 20:12:23 +0000 2019
(https://twitter.com/ChristopherA/status/1167168137328021504)
…”… the application and the file system, enabling interoperability at a data file layer…only when global networked computing expanded that…shifted to siloed data away from the customer’s reach, largely due to the business models that drove the expansion of the Internet”
Thu Aug 29 20:13:17 +0000 2019
(https://twitter.com/ChristopherA/status/1167168365745594371)
TOPIC SolidVC: A Decentralized Verifiable Credentials Management System KEY CONCEPT “enables the unilateral issuance and presentation of credentials by anyone running the software locally, as well as verification of these credentials” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/solid-vc.md
Thu Aug 29 20:13:43 +0000 2019
(https://twitter.com/ChristopherA/status/1167168470691319809)
…”SolidVC (is a) a decentralized implementation of the Verifiable Credentials specification that leverages various ontologies, protocols, and specifications of the Web to deliver a robust and extensible credentialing system.”
Thu Aug 29 20:13:55 +0000 2019
(https://twitter.com/ChristopherA/status/1167168523229179904)
…”SolidVC consists of a number of well-defined protocols for handling credentials. In this section, I will outline these protocols in detail. Setup…Request…Issuance…Sharing…Verification…Revocation…”
Thu Aug 29 20:14:11 +0000 2019
(https://twitter.com/ChristopherA/status/1167168590879088640)
…”There are a number of improvements that I envision for SolidVC…One-to-many SolidVC-Solid account mapping, Extended RDF, serialization support, Issuer Discovery, Credential persistence, Credential expiry support, Command line interface, Overall extensibility”
Thu Aug 29 20:14:31 +0000 2019
(https://twitter.com/ChristopherA/status/1167168673443921920)
…I’m glad that the W3C Solid community has representation at #RWOT9. It has the backing Berners-Lee, the creator of the WWW, and some really good web-based foundations that the more blockchain-oriented approaches lack.
Thu Aug 29 20:17:09 +0000 2019
(https://twitter.com/ChristopherA/status/1167169337695854595)
That’s all for today. Another 20 or so advance readings remain to summarize before #RWOT9 begins in Prague on Tuesday.
Thu Aug 29 20:18:01 +0000 2019
Replying to @torproject
I, through @BlockchainComns, am supporting a Tor exit node. I’d be interested in knowing where topologically there might be a greater need for another exit node.
Fri Aug 30 17:42:10 +0000 2019
RT @EFF: Partnerships between Amazon’s Ring and police expand government surveillance, degrade public trust, breed paranoia, and deny citiz…
Fri Aug 30 17:44:11 +0000 2019
The weekend before #RWOT9 in Prague, another 5 advance reading topic papers on decentralized identity to review.
Fri Aug 30 20:29:07 +0000 2019
(https://twitter.com/ChristopherA/status/1167534737830948865)
TOPIC A Web of Credit Framework KEY CONCEPT Trust is contextual—it isn’t reliable across different domains. This paper examines a fairly well-known context, that of creditworthyness, from a web-of-trust perspective, to see what we can learn from it. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/web-of-credit.md
Fri Aug 30 20:34:54 +0000 2019
(https://twitter.com/ChristopherA/status/1167536190708420610)
…”“trust” encompasses a range of contexts. Trusting that a key belongs to an entity, evaluating an identity, is different from trusting that entity to sign others’ keys accurately, which is different from trusting it to share objective news online or to babysit your kids.”
Fri Aug 30 20:36:13 +0000 2019
(https://twitter.com/ChristopherA/status/1167536521240621057)
…”The traditional credit market is limited by the cost of capital and the cost of underwriting…To reduce the cost of underwriting, we envision a WoT that represents credit relationships and functions as a decentralized underwriting platform, operating on top of a blockchain”
Fri Aug 30 20:37:22 +0000 2019
(https://twitter.com/ChristopherA/status/1167536812308537345)
…”A WoC (Web-of-Credit) is represented as a typical WoT, a weighted directed graph (V, E, w), where V and E represent the set of nodes and the set of edges, respectively, and w is a weight function on edges…”
Fri Aug 30 20:39:18 +0000 2019
(https://twitter.com/ChristopherA/status/1167537297438494720)
…”…An edge e=(u,v) ∈ E and its weight w(e) represent the amount of credit u extends to v, and are considered valid only if they are signed by u’s public key.”
Fri Aug 30 20:40:05 +0000 2019
(https://twitter.com/ChristopherA/status/1167537494063230977)
…”Deciding on how to calculate credit between indirectly connected nodes in a web of credit is crucial in leveraging the graph’s connectivity to defend against Sybil nodes. There is a large literature on crawling social graphs for peer-to-peer Sybil defense”
Fri Aug 30 20:40:16 +0000 2019
(https://twitter.com/ChristopherA/status/1167537540708151296)
…”WoCs can organically affect and be affected by smart contracts’ logic, yielding “rich” WoCs…a smart contract’s behavior can be conditioned on given users’ contexts; e.g., Alice lets a smart contract govern her lendable funds according to her local view of the WoC.”
Fri Aug 30 20:41:04 +0000 2019
(https://twitter.com/ChristopherA/status/1167537743385284608)
…”we can easily imagine how credit can flow from a Korean businesswoman to a young student who has joined an Income Share program to cover his studies; or from a Russian financier to a Filipino worker who needs a stream of …loans to bridge the gap between his daily expenses”
Fri Aug 30 20:42:33 +0000 2019
(https://twitter.com/ChristopherA/status/1167538116195966981)
…The paper continues with some questions and tradeoffs: passivity vs privacy, inter-hub loans, and more. When I read the end of this paper I think of the Lightning Network but as credit combined with reputation. I look forward to see how this topic advances.
Fri Aug 30 20:46:25 +0000 2019
(https://twitter.com/ChristopherA/status/1167539089555562497)
TOPIC Nodemail KEY CONCEPT This is a proposal for a email-like Self-Sovereign Identity protocol, using DIDs, HD Keys (like BIP32) & distributed content-addressable storage (like IPFS or dat://). https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/nodemail.md
Fri Aug 30 20:49:44 +0000 2019
(https://twitter.com/ChristopherA/status/1167539924796620801)
…”Nodemail, then, is a system which seeks to create a robust and secure framework that relesases us from our dependence on ossified addresses, and enables us to conceive of communication from the standpoint of networks built on fresh, unique, consensual connections.”
Fri Aug 30 20:50:39 +0000 2019
(https://twitter.com/ChristopherA/status/1167540155537907714)
…”each participant generates a unique hierarchical node for each connection…through which they make ongoing structures of communication, shifting the locus from static, publicly available identities/addresses to unique addresses/identities born through connection with others.”
Fri Aug 30 20:52:10 +0000 2019
(https://twitter.com/ChristopherA/status/1167540536774991874)
…”users…grant & revoke the access others have to communication with them through management of the address which corresponds with each connection…individuals are granted greater control over the correlations others may make about their social networks.”
Fri Aug 30 20:53:25 +0000 2019
(https://twitter.com/ChristopherA/status/1167540852425658373)
…the author would “like to develop a working prototype that provides much of this functionality and am seeking to define the MVP that leverages an existing open source…which would enable individuals to build their own nodemail servers”
Fri Aug 30 20:54:59 +0000 2019
(https://twitter.com/ChristopherA/status/1167541247382315011)
…I’d be intrigued if this can be integrated into some of the DID BTCR method work happing at #RWOT9, with the additional benefit that financial bonds can be set at risk in cases of spamming.
Fri Aug 30 20:56:15 +0000 2019
(https://twitter.com/ChristopherA/status/1167541564421365761)
TOPIC VCs in Incentivized Competency Assessment KEY CONCEPT “we propose another possible use case of Verifiable Credentials in education space — competency-based assessment that does not rely on a centralized party.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/vc-in-incentivized-competency-assessment.md
Fri Aug 30 20:57:55 +0000 2019
(https://twitter.com/ChristopherA/status/1167541984392822785)
…”We leverage WoT concept…to create a network of competencies where Experts…act as verifiers to assess user’s competency on a given subject. We propose using decentralized staking & slashing mechanism…in order to create financial incentives for users to minimize fraud”
Fri Aug 30 21:00:07 +0000 2019
(https://twitter.com/ChristopherA/status/1167542536526880769)
…”With…open platforms…billions of people are getting access to free or almost free educational content. As this trend continues, more and more people around the world will be able to acquire same level of education as students from top universities.”
Fri Aug 30 21:01:19 +0000 2019
(https://twitter.com/ChristopherA/status/1167542840672604160)
…”Current model of educational credentials issuing is not ideal due to the fact that it only captures the fact of completion of some formal educational program…On the other hand, employers are more interested in applied skills rather than abstract learning”
Fri Aug 30 21:02:14 +0000 2019
(https://twitter.com/ChristopherA/status/1167543071682306053)
…”In order to preserve properties of decentralization and self-sovereign identity all data in anonymized and public:
Anonymity property ensures no user identifying information can be leaked without explicit permission for user. “
Fri Aug 30 21:03:53 +0000 2019
(https://twitter.com/ChristopherA/status/1167543487207751688)
…”Publicity property ensures track record of any interaction between Student and Expert on the platform, thus gives a proof of competency verification process.”
Fri Aug 30 21:04:07 +0000 2019
(https://twitter.com/ChristopherA/status/1167543544220966918)
…”several possible attacks…Verifiers are not diligent enough in their work…Collusion between Verifier and Student…Watchers not being active in the network. In order to mitigate these threats we propose creating an incentive-based mechanism”
Fri Aug 30 21:05:02 +0000 2019
(https://twitter.com/ChristopherA/status/1167543774475673601)
…”Model…still relies on centralized model of competencies & rubrics. Ideal network should also feature some sort of DAO-based instruments for community to come up with relevant and up-to-date map of skills and rubrics describing grading criteria &…levels for each competency.”
Fri Aug 30 21:05:52 +0000 2019
(https://twitter.com/ChristopherA/status/1167543982924206081)
…This is another topic that I’d like to see the BTCR team begin to tackle. Pseudo-anonymous competency is a key requirement in the Amira User Story that is a key guide for the BTCR roadmap.
Fri Aug 30 21:08:27 +0000 2019
(https://twitter.com/ChristopherA/status/1167544633867624448)
TOPIC Using verifiable credentials for German government grants KEY CONCEPT “This paper aims to provide an overview how verified credentials could be implemented to facilitate the application process for German government grants for students.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/vcs-for-german-grants.md
Fri Aug 30 21:09:28 +0000 2019
(https://twitter.com/ChristopherA/status/1167544890915459072)
…”In order to obtain the government grant, every student is required to prove the following:…(non-exhaustive list)…and send them (digitally or analogue) to a local administration. This is not only cumbersome, but also leaves room for errors and fraud.”
Fri Aug 30 21:10:41 +0000 2019
(https://twitter.com/ChristopherA/status/1167545194755088385)
…”As noted in the blockchain position paper from June 2019 Germany aims to build an alternative to the existing identity options based on a government-owned blockchain infrastructure.”
Fri Aug 30 21:11:21 +0000 2019
(https://twitter.com/ChristopherA/status/1167545365119328257)
…Using Verifiable Credentials for educational claims is one easiest use cases for governments to begin to test the self-sovereign identity architecture. I’m glad to see more work advancing in this area.
Fri Aug 30 21:13:23 +0000 2019
(https://twitter.com/ChristopherA/status/1167545875956215810)
TOPIC What’s in Your Wallet? KEY CONCEPT “This paper frames an initial set of terminology based on current practice & emerging standards. We consider the existing state of the art…evaluating commonalities, differences & gaps in the marketplace.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/whats-wallet.md
Fri Aug 30 21:15:29 +0000 2019
(https://twitter.com/ChristopherA/status/1167546403868028933)
…”decentralized software tends to suffer from limited capability as vendors ship…(MVPs) in the battle to establish a defendable role for themselves in the ecosystem. To date no credential wallet offers a seamless, interoperable experience across all digital asset classes.”
Fri Aug 30 21:17:40 +0000 2019
(https://twitter.com/ChristopherA/status/1167546954399793152)
…”Eventually, digital wallets will settle into a handful of common approaches. As the industry matures, patterns of capability and architecture will emerge, solving real problems in understandable ways.”
Fri Aug 30 21:18:18 +0000 2019
(https://twitter.com/ChristopherA/status/1167547115620511744)
…”Darrell O’Donnell…defines wallets as “where we put stuff”…After that colloquial definition, he clarifies that what he means by digital wallet is not “digital wallet storage”. We agree. It’s not where you store stuff, it’s where you control it.”
Fri Aug 30 21:19:35 +0000 2019
(https://twitter.com/ChristopherA/status/1167547437403312129)
…”wallets for credentials have historically managed keys…to meet the requirements of issuers and relying parties…subject typically is uninvolved with key management. In contrast, decentralized approaches take a lesson from cryptocurrencies, using keys created…by the end user”
Fri Aug 30 21:21:32 +0000 2019
(https://twitter.com/ChristopherA/status/1167547927721598976)
…”This innovation, and the emerging standards based on it, democratized credential management, allowing anyone to verifiably say anything about anyone else without censure or permission. Unfortunately, it also created two new problems.”
Fri Aug 30 21:22:12 +0000 2019
(https://twitter.com/ChristopherA/status/1167548093027540993)
…”The first is that individuals lack the sophisticated IT departments needed to build, operate, and maintain robust key management systems and processes…The second is that the issuers themselves are no longer vetted by a hierarchy of trusted authorities.”
Fri Aug 30 21:22:46 +0000 2019
(https://twitter.com/ChristopherA/status/1167548239337463808)
…”From this initial analysis, we can already identify components that are vital, but are not yet accurately depicted. For example, in the identity component diagram above, we have “Agents” floating untethered.”
Fri Aug 30 21:24:49 +0000 2019
(https://twitter.com/ChristopherA/status/1167548754314059777)
…”It is worth noting that because wallets are control mechanisms, it matters just as much how individuals control the functionality as how the wallets implement those controls. “
Fri Aug 30 21:25:28 +0000 2019
(https://twitter.com/ChristopherA/status/1167548916851720192)
…”Many approaches today focus on either key technical features…or on particular components perceived as the “missing link”…What few have done is to illustrate in clear and unambiguous terms exactly how the proposed system will be used by individuals across their lifecycle”
Fri Aug 30 21:26:05 +0000 2019
(https://twitter.com/ChristopherA/status/1167549072791785472)
…”We believe that only by deeply understanding the human requirements-—independent of the technology choices necessary to operationalize it—can we have some sense of a complete and universal solution.”
Fri Aug 30 21:26:33 +0000 2019
(https://twitter.com/ChristopherA/status/1167549189758300165)
…”One next step in the realization of a truly universal digital wallet is establishing a shared language among those developers, regulators, decision-makers, and end-users co-inventing the emergent decentralized identity layer for digital society.”
Fri Aug 30 21:27:03 +0000 2019
(https://twitter.com/ChristopherA/status/1167549314991894530)
…”The terms we’ve introduced above—even just with minimalistic boxes and arrows—provide a…framework for distilling a common vocabulary for how different approaches from different schools of thought, which in turn should help us define a common architecture for digital wallets”
Fri Aug 30 21:27:39 +0000 2019
(https://twitter.com/ChristopherA/status/1167549467832332288)
That’s my 5 for today (though I cheated a little, the last paper was co-authored by myself). About 15 remain to share before #RWOT9 begins on Tuesday in Prague.
Fri Aug 30 21:28:48 +0000 2019
Replying to @stepx10lancast1
I suggest contacting the authors of that paper — there are links to them at top.
Fri Aug 30 21:40:26 +0000 2019
RT @ChristopherA: TOPIC A Web of Credit Framework KEY CONCEPT Trust is contextual—it isn’t reliable across different domains. This paper ex…
Fri Aug 30 21:41:13 +0000 2019
RT @ChristopherA: TOPIC Nodemail KEY CONCEPT This is a proposal for a email-like Self-Sovereign Identity protocol, using DIDs, HD Keys (lik…
Fri Aug 30 21:41:21 +0000 2019
RT @ChristopherA: TOPIC VCs in Incentivized Competency Assessment KEY CONCEPT “we propose another possible use case of Verifiable Credentia…
Fri Aug 30 21:41:27 +0000 2019
RT @ChristopherA: TOPIC Using verifiable credentials for German government grants KEY CONCEPT “This paper aims to provide an overview how v…
Fri Aug 30 21:41:36 +0000 2019
RT @ChristopherA: TOPIC What’s in Your Wallet? KEY CONCEPT “This paper frames an initial set of terminology based on current practice & eme…
Fri Aug 30 21:41:41 +0000 2019
👍“We should have examples embodying most or all known timing leak sources, including (non-exhaustively): Spectre (all variants), Meltdown, Speculative Store Bypass, L1 Terminal Fault (L1TF), and Microarchitectural Data Sampling (MDS).” https://twitter.com/chandlerc1024/status/1167565135616991232
Sat Aug 31 09:33:58 +0000 2019
Maybe we’ll finally get some action from Twitter for real 2FA (or even better MFA) rather than SMS-based 2FA, now that @jack has had his phone’s SIM ported and his Twitter account abused. https://twitter.com/RMac18/status/1167591371101728768
Sat Aug 31 09:40:12 +0000 2019
RT @jonathanstray: If you’ve studied utilitarian ethics, you know that you can’t get the utility of an entire society just by adding up the…
Sat Aug 31 11:49:48 +0000 2019
Ergodicity “brings a new perspective to our understanding of cooperation and competition, and the conditions under which beneficial cooperative activity is possible…Standard thinking in economics finds limited scope for cooperation, as individual people or businesses seeking…”
Sat Aug 31 11:59:28 +0000 2019
(https://twitter.com/ChristopherA/status/1167768865201430528)
”…their own self-interest should cooperate only if, by working together, they can do better than by working alone…Things change dramatically, however, if one considers how parties do when facing uncertainty and repeatedly undertaking risky activities through time…”
Sat Aug 31 12:00:32 +0000 2019
(https://twitter.com/ChristopherA/status/1167769135486590979)
“…Mathematically, it turns out that such pooling increases the grow rate of resources or wealth for all parties.” This is why standards, open source and other commons work. https://aeon.co/ideas/how-ergodicity-reimagines-economics-for-the-benefit-of-us-all
Sat Aug 31 12:02:01 +0000 2019
RT @ChristopherA: ”…their own self-interest should cooperate only if, by working together, they can do better than by working alone…Things…
Sat Aug 31 12:02:13 +0000 2019
RT @ChristopherA: “…Mathematically, it turns out that such pooling increases the grow rate of resources or wealth for all parties.” This is…
Sat Aug 31 12:02:18 +0000 2019
Middle of the weekend, and people are starting to arrive in Prague for #RWOT9. Here are 5 more summaries of advance reading topics to help us prepare for our collaborations next week.
Sat Aug 31 20:47:29 +0000 2019
(https://twitter.com/ChristopherA/status/1167901745910927360)
TOPIC Infrastructure for Persistently Live DIDs KEY CONCEPT Infrastructure for most DID methods is bifurated, with DIDs rooted in blockchain proofs, but the DID documents are in a separate layer. Can we consolidate both functions? https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/infrastructure-for-persistently-live-dids.md
Sat Aug 31 20:47:43 +0000 2019
(https://twitter.com/ChristopherA/status/1167901803347759104)
…”limiting factors…On the lesser end, there is the minutia of knitting both layers together. More standards, more software, more maintenance, and possibly more legal situations are required to knit both layers together. “
Sat Aug 31 20:47:58 +0000 2019
(https://twitter.com/ChristopherA/status/1167901866249740290)
…”On the greater end, it limits the types of applications that may be run on such an infrastructure, since any application/feat of coordination requiring significant liveness will not be able to run.”
Sat Aug 31 20:48:08 +0000 2019
(https://twitter.com/ChristopherA/status/1167901910826766336)
…”serious liabilities—that of credential revocation. If an identity provider makes a mistake, or receives new information and must adjust the status of a particular claim, if they have already signed and circulated a claim, how are they to revoke it?”
Sat Aug 31 20:48:20 +0000 2019
(https://twitter.com/ChristopherA/status/1167901959765950469)
…”for every scenario mentioned, this would entail another round trip to the issuer to check if they indeed were authorized, which would defeat the entire point of the signing process. It seems that liveness is a desirable property when considering mutating permission systems.”
Sat Aug 31 20:48:30 +0000 2019
(https://twitter.com/ChristopherA/status/1167902003269259266)
…”A solution to those complexities would be to have an inherently networked computational fabric that would consolidate both functions required for self sovereign identity to work”
Sat Aug 31 20:48:43 +0000 2019
(https://twitter.com/ChristopherA/status/1167902058260754433)
…”The Gravity protocol is a language based on lambda calculus, prototypes, object capabilities and message passing to create distributed applications. Gravity nodes are isolated runtime processes connected through cryptographic capabilities.”
Sat Aug 31 20:48:53 +0000 2019
(https://twitter.com/ChristopherA/status/1167902099843104769)
“Gravity applications are: Persistent…Private…Transactional…Distribute…Secure…Safe…Redundant…Portable…Reflective…Gravity enables the creation of a new generation of distributed and resilient applications that are inherently networked.”
Sat Aug 31 20:49:15 +0000 2019
(https://twitter.com/ChristopherA/status/1167902191643811840)
…This paper implies that there are aren’t any fit-for-purpose blockchains, whereas both Sovrin & http://Veres.One are exactly that. However, he is correct that none that I know of do as broad range of cryptographic functions at layer one as he proposes.
Sat Aug 31 20:49:52 +0000 2019
(https://twitter.com/ChristopherA/status/1167902346451357702)
TOPIC Verifiable Credential Authentication via OpenID Connect (vc-authn-oidc) KEY CONCEPT This document describe in some detail (though still incomplete) how we can leverage VCs the legacy OpenID Connect for authentication https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/vc-authn-oidc.md
Sat Aug 31 20:50:05 +0000 2019
(https://twitter.com/ChristopherA/status/1167902398838276096)
…”DID Communication (DIDComm) is used as the messaging protocol between the OP and IW. DIDComm, is an emerging messaging protocol…This messaging protocol is used as the medium for the OP to communicate with the IW.”
Sat Aug 31 20:50:22 +0000 2019
(https://twitter.com/ChristopherA/status/1167902473480048651)
…”There are two main ways the interactions between the actors of VC-AuthN will be used. The UserAgent and IdentityWallet are co-located on the same device…The UserAgent and IdentityWallet are not co-located”
Sat Aug 31 20:50:39 +0000 2019
(https://twitter.com/ChristopherA/status/1167902541750751232)
…”Because this specification defines extending a valid OP to include VC-AuthN support, integration with many existing IAM solutions can be added without any major additional work…an IAM system simply assumes the role of a RP to the VC-AuthN compatible OP.”
Sat Aug 31 20:50:51 +0000 2019
(https://twitter.com/ChristopherA/status/1167902594200530947)
…”Un-Answered questions: SIOP instead of DIDComm for the requests…Should the verifiable credential presentation…be a valid JSON-LD object…Should the pres_req_conf_id instead be a URN so the OP does not necessarily have to host the additional configuration API?…”
Sat Aug 31 20:51:02 +0000 2019
(https://twitter.com/ChristopherA/status/1167902640266629122)
…”…Perhaps seperate things out so we have two specs, one for the RP <–> OP integration the other for AD <–> OP”
Sat Aug 31 20:51:12 +0000 2019
(https://twitter.com/ChristopherA/status/1167902682843009026)
…I’m pleased to see these efforts to leverage existing legacy identity protocols for use with DIDs and Verifiable Credentials. This one is looking well thought out.
Sat Aug 31 20:51:25 +0000 2019
(https://twitter.com/ChristopherA/status/1167902737482182656)
TOPIC Addition of Proof Request/Response to a formal Verifiable Credentials specification KEY CONCEPT “This document outlines the approach taken at Workday and proposes it as an addition or companion to the VC spec.”
https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/verifiable-credentials-proof-request.md
Sat Aug 31 20:51:37 +0000 2019
(https://twitter.com/ChristopherA/status/1167902786693943298)
…”It is the opinion of the authors that in order to have an interoperable VC flow the question of how to request Credential data must be addressed. We believe that leaving the solution out of the standards will result in competing formats which will reduce interoperability.”
Sat Aug 31 20:51:50 +0000 2019
(https://twitter.com/ChristopherA/status/1167902841018519554)
…”A Proof Request is here defined as a document produced by a Verifier which lists the data criteria for a verification event.”
Sat Aug 31 20:52:05 +0000 2019
(https://twitter.com/ChristopherA/status/1167902905019428873)
…”Similarly, Proof Response is the proposed format with which to respond to a Proof Request. By having Proof Request as part of the VC specification, software agents can have a common understanding of the data being requested.”
Sat Aug 31 20:52:18 +0000 2019
(https://twitter.com/ChristopherA/status/1167902957964156930)
…”Since enterprise use cases are less concerned with Zero Knowledge Proofs, we feel that individually signing attributes on a VC is sufficient for selective disclosure. This has the advantage of simpler crypto which anyone can reason about.”
Sat Aug 31 20:52:29 +0000 2019
(https://twitter.com/ChristopherA/status/1167903003241697281)
…”This document does not currently address Zero Knowledge Proofs. A later version of this document will describe how a Verifier requests a predicate proof.”
Sat Aug 31 20:52:44 +0000 2019
(https://twitter.com/ChristopherA/status/1167903068895072263)
…”Drawbacks/Limitations: Verbose
Issuers is a limited subset of DIDs. We should also allow for a Proof from all members of Issuer trusted by X.”
Sat Aug 31 20:52:58 +0000 2019
(https://twitter.com/ChristopherA/status/1167903126210281474)
…”Unresolved Questions: We are aware of the projects mentioned in above in Prior Art. Of these, we know that Sovrin is using Proof Requests in live systems. We do not know of other formats currently being used by live or nearly live implementations of VC.”
Sat Aug 31 20:53:09 +0000 2019
(https://twitter.com/ChristopherA/status/1167903172318265344)
…This is the third proposal I’ve seen for requesting VCs — it looks like it is time for these teams to sit down and see if they can puzzle through and make a protocol that will work for all of them.
Sat Aug 31 20:53:20 +0000 2019
(https://twitter.com/ChristopherA/status/1167903219609006080)
TOPIC Utilizing zero-knowledge proofs and verifiable credentials to provide privacy-friendly income tests for social housing KEY CONCEPT Robobank has been experimenting with SSI for a while, and this paper details a pilot with the Dutch government. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/zero-knowledge-proofs-and-vc-in-social-housing.md
Sat Aug 31 20:53:34 +0000 2019
(https://twitter.com/ChristopherA/status/1167903278400622594)
…”A challenge often faced here was that partners were interested in different technologies. That is why we designed the universal ledger agent…We have a plugin for an ERC-780 contract on Ethereum, W3C verifiable credentials on Ethereum and a Sovrin plugin.”
Sat Aug 31 20:54:01 +0000 2019
(https://twitter.com/ChristopherA/status/1167903388920512512)
…”In the Netherlands, an income test is required in order to apply for social housing…we focused on a solution using self-sovereign identity, blockchain and zero knowledge proofs. Our main focus points were a customer centric approach and data minimalization.”
Sat Aug 31 20:54:22 +0000 2019
(https://twitter.com/ChristopherA/status/1167903477499981825)
…”The proof of concept covers the following process… Social housing corporation sends the income test to the identity wallet. User authenticates at government using DigID, an authentication method for Dutch residents for governmental websites…”
Sat Aug 31 20:54:49 +0000 2019
(https://twitter.com/ChristopherA/status/1167903592168054785)
…”…The government offers an income statement to the identity wallet in the form of a W3C verifiable credential. A decentralized identifier (DID) is published to the blockchain
An answer to the income test is generated in the identity wallet using a zero-knowledge proof…”
Sat Aug 31 20:55:13 +0000 2019
(https://twitter.com/ChristopherA/status/1167903690780364801)
…”…A cryptographically signed yes or no is shared with the housing corporation. The social housing corporation verifies proof and correctness in the blockchain”
Sat Aug 31 20:55:28 +0000 2019
(https://twitter.com/ChristopherA/status/1167903755192291329)
…Last spring’s Robobank demo at #RWOT8 in Barcelona got a lot of applause for its real world practice combined with real SSI architecture. A highlight in this paper was discussion of use of multiple DID methods, a critical challenge that few of us have made sufficient priority.
Sat Aug 31 20:57:44 +0000 2019
(https://twitter.com/ChristopherA/status/1167904323549851655)
TOPIC Heresay: A Fuzzy Prediction Market for Distributed Reputation KEY CONCEPT “We propose a pattern for distributed, emergent reputation rendered via a fuzzy prediction market.” https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/heresay.md
Sat Aug 31 20:58:06 +0000 2019
(https://twitter.com/ChristopherA/status/1167904419540688898)
…”In order to promote scale with resilience, legibility with ephemerality, and transitivity with context, we begin by investigating how identity, trust, and reputation function at intimate scale and under organic constraints.”
Sat Aug 31 20:58:17 +0000 2019
(https://twitter.com/ChristopherA/status/1167904465644441601)
…”Identity is a function. An identity signifies, among other things, a specific behavioral function. Given these inputs, what are the outputs? When this happens, how will this individual react?”
Sat Aug 31 20:58:29 +0000 2019
(https://twitter.com/ChristopherA/status/1167904514814275589)
…”Trust is a degree of certainty. Trust is the subjective certainty that an entity will behave predictably in response to specific circumstance…This certainty is cultivated through repeated interactions”
Sat Aug 31 20:59:02 +0000 2019
(https://twitter.com/ChristopherA/status/1167904653662507015)
…”Reputation is a prediction. Reputation is a prediction of how an entity will behave. Reputation systems, therefor, are designed to foster trust where there is no prior data…”
Sat Aug 31 20:59:25 +0000 2019
(https://twitter.com/ChristopherA/status/1167904750265753605)
…”…When participants in a system have some supplemental certainty of predictable interactions, they will tolerate larger risks and form larger structures in less time.”
Sat Aug 31 20:59:38 +0000 2019
(https://twitter.com/ChristopherA/status/1167904805282435072)
…”Identity is quantum. Identities are neither fixed nor independent…an entity changes both with time and within time, which is why the authors of Identity Crisis characterize identities as ‘emergent phenomenon’”
Sat Aug 31 20:59:50 +0000 2019
(https://twitter.com/ChristopherA/status/1167904854376734727)
…”Risks: Gaming…Falsification…Sybil Attack…Miscorrelation…Self-Fulfilling Prophecy”
Sat Aug 31 21:00:02 +0000 2019
(https://twitter.com/ChristopherA/status/1167904902732902402)
…”Goal…Legibility…generate highly-legible reputation, like a credit score or product rating, while mitigating the risks of decontextualization such as gaming and falsification.”
Sat Aug 31 21:00:22 +0000 2019
(https://twitter.com/ChristopherA/status/1167904989290745856)
…”Goal…Transitivity…promote reputation transitivity while mitigating risks such as context collapse, miscorrelation, self-fulfilling prophesy, and high-velocity spirals.”
Sat Aug 31 21:00:35 +0000 2019
(https://twitter.com/ChristopherA/status/1167905044617809920)
…”Heresay operates as a distributed, fuzzy prediction market for reputation claims. Below, we outline the system in broad strokes.”
Sat Aug 31 21:00:51 +0000 2019
(https://twitter.com/ChristopherA/status/1167905109335928835)
…This is 3rd or 4th topic paper related to reputation submitted to this #RWOT9, and there have been many at previous events, though none have gone to final since #RWOT4’s https://github.com/WebOfTrustInfo/rwot4-paris/blob/master/final-documents/reputation-design.pdf. This is another topic I hope to see some collaboration and consensus building on.
Sat Aug 31 21:03:25 +0000 2019
(https://twitter.com/ChristopherA/status/1167905754172424192)
If you’ve not read the Primer documents that are also in our repo, they’ve been written to help give you the basics of how #RWOT design workshops function, how we approach identity, what is SSI, what are DIDs & VCs, our glossary, etc. https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings
Sat Aug 31 21:07:02 +0000 2019
(https://twitter.com/ChristopherA/status/1167906666999738369)
That is all for tonight, just a few more papers to summarize tomorrow. Then onward to #RWOT9 for the real work of collaboration to advance our advocacy for human-rights centric digital identity.
Sat Aug 31 21:08:48 +0000 2019
RT @jeffemmett: Ergodicity economics makes the simple assertion that time (i.e. temporal path dependence) matters in our economic decision…