Replying to @cronokirby
There is a big difference between a cryptographer, a cryptographic engineer, and a cryptographic protocol designer. And then there is are are huge different knowledge domains in each: lattice cryptography, defensive engineering, mechanism design.
Mon May 02 14:10:44 +0000 2022
RT @SarahJamieLewis: Governments around the world continue to put forward draft laws that would make secure systems illegal (sometimes written so badly they would technically outlaw arithmetic)
It is important that we come to see these actions as active attacks on democracy and free society.
Mon May 02 14:25:26 +0000 2022
Replying to @cronokirby
A key test in all three of these categories is “humility first”. https://twitter.com/ChristopherA/status/997233796058509313
Mon May 02 14:55:46 +0000 2022
@add_hawk want a copy of my book Meeples Together on cooperative game design? Adam me: https://www.MeeplesTogether.com/about
Tue May 03 02:48:52 +0000 2022
Replying to @raw_avocado, @ShareblockHolmz and @arcbtc
There is also bytewords. Defined at https://github.com/BlockchainCommons/Research/blob/master/papers/bcr-2020-012-bytewords.me reference library & cli available, and used by other specs like UR.
Wed May 04 20:56:31 +0000 2022
Replying to @raw_avocado, @ShareblockHolmz and @arcbtc
In particularly look at the word list selection criteria: https://github.com/BlockchainCommons/Research/blob/master/papers/bcr-2020-012-bytewords.md#word-selection-criteria
Wed May 04 20:57:02 +0000 2022
RT @nathan_chong: Kani says hi! Kani is a new open source verification tool for Rust: https://model-checking.github.io/kani-verifier-blog/2022/05/04/announcing-the-kani-rust-verifier-project.html
Thu May 05 02:37:46 +0000 2022
RT @FOUNDATIONdvcs: Passport Batch 2 includes a power-only USB-C connector for charging the lithium ion battery. The connector only has pin…
Fri May 06 15:43:25 +0000 2022
🤬“The pervasive and barely regulated data collection industry could have a big role to play in investigating and proving cases against people accused of performing or getting what may soon be illegal abortions.” https://www.vox.com/platform/amp/recode/23059057/privacy-abortion-phone-data-roe
Sat May 07 02:20:35 +0000 2022
Replying to @matthew_d_green, @ncweaver, @durumcrustulum, @gakonst and @cronokirby
Where do VRFs fall into your thinking about signatures?
Mon May 09 21:24:53 +0000 2022
I appreciate these tweaks to enable robustness in Schnorr threshold multisig. This one offers robustness even against a majority of malicious co-signers. This is quite useful when the policy requires a quorum of 2 of 5 but 3 are offline or compromised. It also scales well. https://twitter.com/real_or_random/status/1523964246945636352
Tue May 10 15:40:45 +0000 2022
RT @philiprosedale: I suspect some of the positive impact of @SecondLife as compared to social media is due to presence of many “public goo…
Tue May 10 16:02:31 +0000 2022
I’m not surprised that @Discord’s “private” channels are not secure, but these very revealing details about business teams, people and security relevant details about multisig signer members & policies are quite trivial to get. 🤷🏻♂️ https://twitter.com/joshfraser/status/1524093113953886210
Wed May 11 01:51:26 +0000 2022
Example: https://twitter.com/joshfraser/status/1524093118555082752
Wed May 11 01:51:27 +0000 2022
“…to protect ourselves from our own domestic governments…the end of Roe has laid that bare. The threat is coming from inside the house. “China” was really a euphemism for “Alabama” this whole time. Encryption advocates in the U.S. just usually aren’t willing to say so.”
Thu May 12 01:47:43 +0000 2022
👏🏼“If you’re an encryption advocate in the United States, it’s time to stop pretending that encryption’s protection against oppressive governments is only about Uighurs in Xinjiang or gay people in Uganda. Americans also need strong encryption… https://cyberlaw.stanford.edu/blog/2022/05/end-roe-will-bring-about-sea-change-encryption-debate
Thu May 12 01:47:43 +0000 2022
RT @matthew_d_green: For those who missed it yesterday, the EU Commission just proposed a surveillance regime that will read your private t…
Thu May 12 14:09:29 +0000 2022
RT @matthew_d_green: Reminder to Silicon Valley: there’s an even chance that many governments in the world will be run by authoritarian mov…
Thu May 12 14:09:53 +0000 2022
What if semiconductor manufacturers made chips especially intended for cryptocurrency & digital identity & asset wallets? That’s the topic of Blockchain Commons’ first Silicon Salon. [1/6] https://www.blockchaincommons.com/salons/silicon-salon/
Fri May 13 02:09:39 +0000 2022
There will then be two hours of facilitated discussion, seeking consensus on questions of secure enclave/MCU integration, secure and persistent storage, and how semiconductor designs can improve cryptographic security, resilience and efficiency [4/6].
Fri May 13 02:09:40 +0000 2022
Our virtual Salon will contain an hour of presentations from experts in the field including CrossBar, Tropic Square, Proxy, Bryan Bishop, and Christopher Allen. [3/6]
Fri May 13 02:09:40 +0000 2022
Join semiconductor manufacturers, crypto-wallet makers, and experts in the field to talk about requirements for secure semiconductors chips made to support modern cryptography. [2/6]
Fri May 13 02:09:40 +0000 2022
Joining us by purchasing a ticket at Eventbrite. We are limited to 40 additional participants, so sign up now! (Our sponsors via Github will automatically be receiving free tickets) [6/6] https://github.com/sponsors/BlockchainCommons
Fri May 13 02:09:41 +0000 2022
The Silicon Salon is scheduled for June 1st from 9am to noon PT. (That’s starting at noon in ET or 6pm in CET) [5/6]
Fri May 13 02:09:41 +0000 2022
@matthew_d_green If there is a particular wishlist item that you wish was secured by hardened chips (bbs+ sigs, ristretto255 curve, BLS, VRFs, etc) I’d love a quote RT of this tweet with your suggestions. https://twitter.com/ChristopherA/status/1524934871637819392
Fri May 13 06:01:22 +0000 2022
RT @tropicsquare: @Jovian_358459 Thanks, we’ll be presenting. https://t.co/NAq3jJcKmS
Fri May 13 14:27:22 +0000 2022
RT @kanzure: What’s on your wishlist for secure enclaves for crypto? I will be co-hosting a chip design workshop focused on hardware wallet…
Sat May 14 01:33:20 +0000 2022
RT @csuwildcat: This is false - FIDO isn’t an identity system at all, let alone portable, it’s a centralized account authentication system…
Sat May 14 19:18:01 +0000 2022
Though I’m not the biggest fan of both the term “soulbound” and some of the approaches being suggested for it, sybil resistance is often required for “fairness”. That being said, Proof of Personhood #PoP is quite hard to do safely. Much more work to do! https://twitter.com/WhinfreyChris/status/1525178626563420160
Sat May 14 19:26:44 +0000 2022
In particular, this link offers the changes since the last guide (May 2021): https://support.apple.com/en-ca/guide/security/secb82d6b274/web
Sun May 15 00:07:12 +0000 2022
An update to Apple’s “Platform Security Guide” for iOS & macOS is now out (dated May 2022): https://help.apple.com/pdf/security/en_US/apple-platform-security-guide.pdf
Sun May 15 00:07:12 +0000 2022
RT @cronokirby: For something like this, you’d probably want broad utility over prioritizing specific algorithms, to avoid baking in too mu…
Sun May 15 23:38:50 +0000 2022
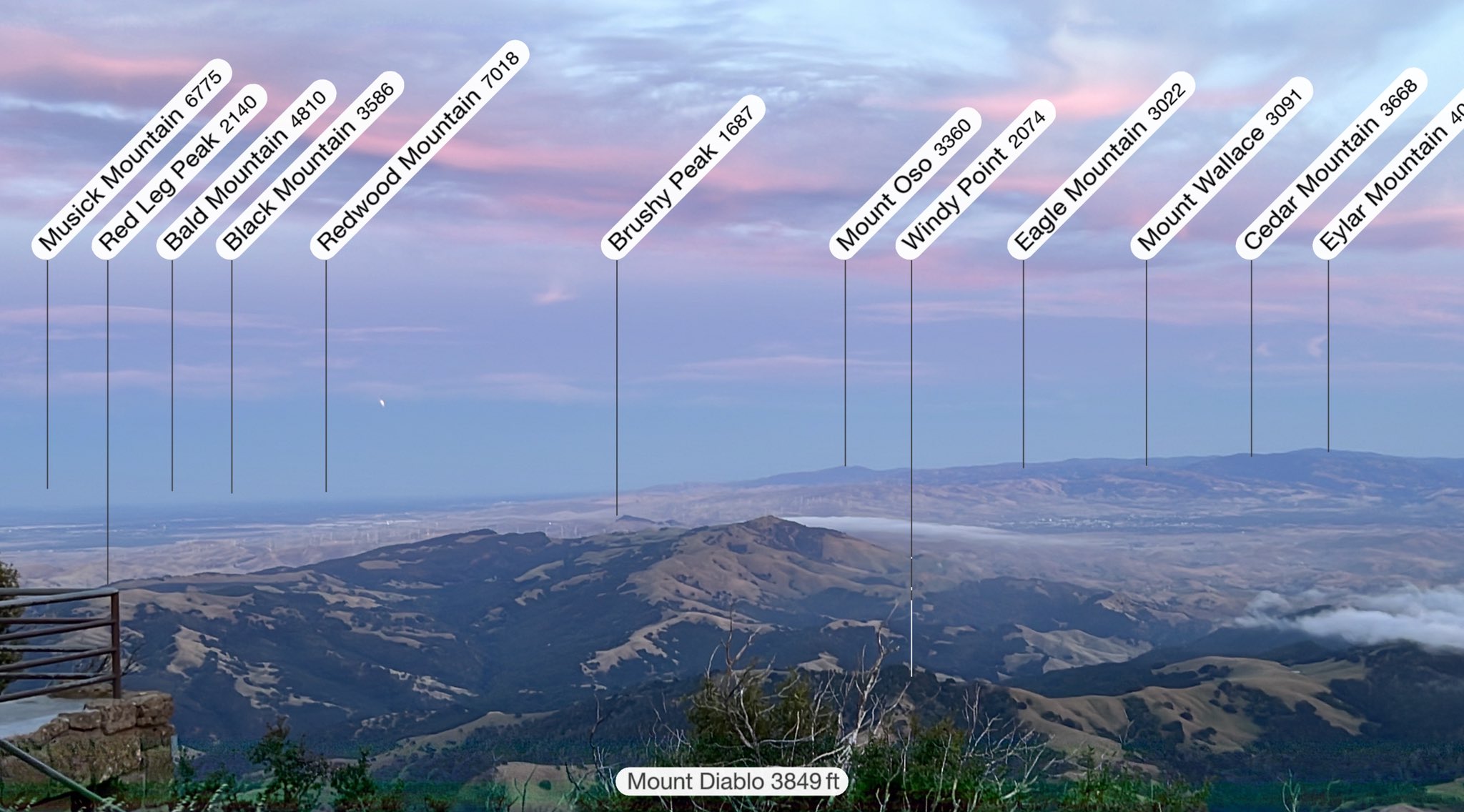
The #LunarEclipse from Mt. Diablo, rising from the shadow of Mt. Diablo over the Altamonte pass during sunset.
Mon May 16 03:10:46 +0000 2022
It looks like the haze will prevent us from seeing the rest of the full #LunarEclipse2022 from Mt. Diablo, but seeing the partial moon crescent 🌙 rise from the shadow of the mountain 🗻 we were standing on was quite dramatic.
Mon May 16 03:29:40 +0000 2022
RT @ChristopherA: It looks like the haze will prevent us from seeing the rest of the full #LunarEclipse2022 from Mt. Diablo, but seeing the…
Mon May 16 03:29:46 +0000 2022
My iPhone 13 can see it a bit better than we can. Wind is roaring right now as fog is coming in.
Mon May 16 03:46:16 +0000 2022
Patience rewarded with brief view between clouds: (10s exposure)
Mon May 16 04:34:30 +0000 2022
Replying to @euvieivanova
There is a lot of this outside of the DAO/Web3 movement. I’ve am old “opinionated” document on the topic at https://github.com/ParticipatoryOrgs/Participatory-Organizations-Overview-and-Taxonomy
Mon May 16 23:21:50 +0000 2022
Replying to @samanthajmarin
When and how does it terminate? When it’s mission is complete? After investors get a reasonable return on investment & time? After a generation? When bad actors dominate? When attacked? Biology teaches immortality is a risky design.
Mon May 16 23:27:18 +0000 2022
👏🏼 We need more companies involved in cryptocurrency & digital identity as voting members of the #W3C. For instance, there is a charter vote this month for a Working Group to do Verifiable Credentials 2.0, which can address some of the weaknesses of the 1.0 draft. https://twitter.com/brockm/status/1526723285102120960
Wed May 18 18:15:22 +0000 2022
RT @BlockchainComns: @MarkFriedenbach @murchandamus @djvalerieblove @rocket_fuel_ @miketwenty1 @ercwl @pwuille @parman_the @BitcoinQ_A We a…
Wed May 18 18:24:20 +0000 2022
RT @BlockchainComns: @MarkFriedenbach @murchandamus @djvalerieblove @rocket_fuel_ @miketwenty1 @ercwl @pwuille @parman_the @BitcoinQ_A @FOU…
Wed May 18 18:24:28 +0000 2022
So how do we make it safer? 1.5 allows for the printing of individual SSKR shares (or even their individual storage as PDFs). Network printing can be a big security hole, so we wanted to demonstrate how to limit that by sharding the printing as well! [3/10]
Wed May 18 18:59:50 +0000 2022
The usability work centers on SSKR, our secret sharding system. We feel that it’s crucial for ensuring the resilience of your seeds. [2/10] https://github.com/BlockchainCommons/Research/blob/master/papers/bcr-2020-011-sskr.md
Wed May 18 18:59:50 +0000 2022
The new version 1.5 of Gordian Seed Tool for iOS & macOS from @Blockchaincomns focuses on usability & a new experimental feature to support NFC Tags. It’s our updated look at the best practices for the future of self-sovereign #SmartCustody of cryptographic key material. [1/10] https://twitter.com/BlockchainComns/status/1526990262592974849
Wed May 18 18:59:50 +0000 2022
With that said, there are definite security questions when using NFC Tags for non-sharded content like seeds & derived keys, which is why we’ve labeled it as experimental. Use this new NFC feature with caution. More on that in a future tweetstorm! [7/10]
Wed May 18 18:59:51 +0000 2022
We are also beginning to experiment with NFC Tag support in the 1.5 release. You can now read URs from an NFC Tag just by tapping it with your phone. Gordian Seed Tool will be opened automatically and your shards recovered, seed material imported, or PSBT signed! [6/10]
Wed May 18 18:59:51 +0000 2022
These features allow for more scenarios to support long-term offline storage methods that can be safely restored many years in the future. [5/10]
Wed May 18 18:59:51 +0000 2022
We also wanted to demonstrate how to make it easy & secure cryptographic data to the iOS file system or to external SD Cards. With these features you can write out SSKR key shards to a variety of media, offering more options to safely export key material from your iPhone. [4/10]
Wed May 18 18:59:51 +0000 2022
We also have available an early draft of a sophisticated 2 of 3 multisig scenario that leverages Gordian Seed Tool’s offline SSKR features (with @FOUNDATIONdvcs Passport & @Sparrow Wallet) at https://github.com/BlockchainCommons/SmartCustody/blob/master/Docs/Scenario-Multisig.md [9/10]
Wed May 18 18:59:52 +0000 2022
If you haven’t already, you can pick up our Gordian Seed Tool reference application for cryptographic seed storage & signing from the Apple App Store. [8/10] https://apps.apple.com/us/app/gordian-seed-tool/id1545088229
Wed May 18 18:59:52 +0000 2022
You can support @BlockchainComns continued work toward wallet interoperability reference apps & specifications, all with independence, privacy, resilience, privacy & openness, by becoming a monthly sponsor via Github! [10/10] https://github.com/sponsors/BlockchainCommons
Wed May 18 18:59:53 +0000 2022
RT @hoffmang: The @chia_project is already a #W3C member specifically to support this.
Wed May 18 19:31:30 +0000 2022
Replying to @etekis and @petejkim
The patrons of Blockchain Commons @BlockchainComns are also working on Secure MPC based wallet infrastructure. Will @coinbase be supporting open development (no lock-in) & open source (complete source code for both client & server)?
Wed May 18 22:01:58 +0000 2022
The patrons of Blockchain Commons @BlockchainComns are also working on Secure MPC based wallet infrastructure. Will @coinbase be supporting open development (no lock-in) & open source (complete source code for both client & server)? https://twitter.com/petejkim/status/1527027583254241280
Wed May 18 22:02:19 +0000 2022
It looks like our summer interns at @BlockchainComns are interested in implementing BIP-322, which leverages the Bitcoin scripting language to enable the signing of arbitrary messages using the same keys & scripts used for transactions. Want to help? https://github.com/BlockchainCommons/Community/issues/112
Fri May 20 19:51:14 +0000 2022
@SeedSigner We have a number of summer interns in India that we’d like to get SeedSinger devices to (we’d like to add PRs for UR support), but given supply chain, shipping, etc. is hard for them. Do you have someone assembling them in India who can help?
Fri May 20 20:19:21 +0000 2022
Replying to @EnteroPositivo, @esiattorney and @SeedSigner
This will be useful for our summer interns in India as we’d like to add UR based crypto-request and animated PSBTs, but parts availability is more complex there.
Sat May 21 01:23:51 +0000 2022
Replying to @kate_sills
The Long Way to a Small, Angry Planet (Wayfarers Book 1) https://www.amazon.com/dp/B00ZP64F28/ref=cm_sw_r_cp_api_KC05T1TD9J26W2SMYADJ
Mon May 23 16:18:08 +0000 2022
Replying to @kate_sills
Quarter Share (Trader’s Tales from the Golden Age of the Solar Clipper Book 1) https://www.amazon.com/dp/B00AMO7VM4/ref=cm_sw_r_cp_api_ZCP5P3460HW00WTN0HDH
Mon May 23 16:19:35 +0000 2022
Replying to @kate_sills
I’m very confused about why On Basilisk Station is not on Kindle, but has long been available free from author online as a teaser for series. https://www.amazon.com/dp/B007360DBU/ref=cm_sw_r_awdo_5SF5NWKMK3K5V0AS7EAA?psc=1
Mon May 23 16:26:45 +0000 2022
Replying to @kate_sills
If you love Becky Chambers you’ll love the “A Trader’s Tale from the Golden Age of the Solar Clipper” series. Has heart.
Mon May 23 16:28:47 +0000 2022
Replying to @mnot
You say: “when a participant loses their keys — recovering their identity is not possible”. That is only true for the more basic DID methods — there has been a lot of exploration of various methods to pre-commit to future keys (did-keri), support social key recovery, or…
Tue May 24 07:13:03 +0000 2022
Replying to @mnot
…offer social revocation and collaborative key generation (did:btcr w/ FROST). Join us at #RebootingWebOfTrust in the The Hague in September to talk more? https://twitter.com/RWOTEvents/status/1512876315900141569?s=20&t=OveeUriuyBDFz2qXSXKc1g
Tue May 24 07:14:59 +0000 2022
Replying to @mnot
I also highly suggest you dive deep into the W3C DID Method Rubric. It is a scoring guide to evaluate performance, a product, or a project for decentralization. https://www.w3.org/TR/did-rubric/
Tue May 24 07:17:45 +0000 2022
Replying to @mnot
Personally, I’m focused more right now on the opportunities offered by new collaborative key management approaches like FROST. Though intended for threshold signatures, it can also be used as a social key creation tool, which can be socially re-regenerated if lost.
Tue May 24 07:21:41 +0000 2022
Replying to @nvk and @COLDCARDwallet
Can we get you to share this in next week’s Silicon Salon? DM me?
Tue May 24 15:02:29 +0000 2022
RT @kanzure: Here’s a sneak preview for the upcoming Blockchain Commons’ Silicon Salon #1 – take a look at my transcript of @lkcl’s presen…
Tue May 24 16:39:16 +0000 2022
It’s just one week until our first Silicon Salon, coming next Wednesday, June 1, starting at 9am PDT. [1/11] https://www.eventbrite.com/e/silicon-salon-hosted-by-blockchain-commons-tickets-338323152657
Wed May 25 15:19:42 +0000 2022
Topics of discussion will include architecture, firmware, supply chain, cryptographic primitives, cryptographic protocols, crypto acceleration, countermeasures, and more! [6/11]
Wed May 25 15:19:43 +0000 2022
After the presentations, it’s the cryptographic wallet development community’s turn to discuss their requirements and concerns. We will be capturing this conversation under Chatham House rules and sharing it with the larger community. [5/11]
Wed May 25 15:19:43 +0000 2022
We’ll have presentations by @CrossBar, @TropicSquare, @Supranational, @Proxy , and @lkcl on Libre-SOC. We are evaluating the inclusion of a few more (any @risc_v chip designers doing cryptography?). [4/11]
Wed May 25 15:19:43 +0000 2022
We’ve got more than 30 people signed up so far, but still have a little room left for security people, hardware designers, cryptographers, and others interested in the future of securing secrets in silicon. [3/11]
Wed May 25 15:19:43 +0000 2022
This virtual salon gives you the opportunity to have your input into the first generation of semiconductor designs created especially for cryptocurrency wallet use. [2/11]
Wed May 25 15:19:43 +0000 2022
If you have any of your own priorities and cryptographic wishlist items that you want to be secured by semiconductor chips, sign up now to join us for this interactive salon and have your say. [9/11]
Wed May 25 15:19:44 +0000 2022
We are also trying to capture the requirements of hardware designers for supply chain security, HSM & vendors for custody & server performance, and online services for securing large numbers of servers. [9/11]
Wed May 25 15:19:44 +0000 2022
On the wishlists of others is the support of the ristretto255 curve, ECC add & multiply, personal roots-of-trust with self-sovereign open firmware, and acceleration of various MPC & ZKP protocols with direct access to exponentiation, finite field math, etc. [8/11]
Wed May 25 15:19:44 +0000 2022
On my personal wishlist for native silicon support is secp256k1, not only for ECDSA but also for Schnorr signing, with support for adapter signatures in both. I want this in a Secure Enclave with side-channel resistance, not as an interpreted script in an MCU. [7/11]
Wed May 25 15:19:44 +0000 2022
The Silicon Salon is hosted by Blockchain Commons. @BlockchainComns. Join the community by becoming a monthly sponsor and supporting the future of open & interoperable, secure & compassionate digital infrastructure! [10/11] https://github.com/sponsors/BlockchainCommons
Wed May 25 15:19:45 +0000 2022
RT @ChristopherA: On my personal wishlist for native silicon support is secp256k1, not only for ECDSA but also for Schnorr signing, with su…
Wed May 25 18:33:17 +0000 2022
RT @ChristopherA: On the wishlists of others is the support of the ristretto255 curve, ECC add & multiply, personal roots-of-trust with sel…
Wed May 25 18:33:25 +0000 2022
Replying to @dunxen and @coinjoiner
Cool. How does it differ from the work @jesseposner & others are doing for secp256k1-zkp? I’m also very interested in refactoring out the VSS portion as it can be very useful for other purposes.
Sat May 28 04:32:37 +0000 2022
Replying to @kate_sills
Here is a real sleeper. Published posthumously by a colleague of mine written by her father, it really was quite good! I wish there could be more. $0.99 on kindle. https://www.amazon.com/dp/B00LU4NFN4