#SmartCustody is an ongoing project of @BlockchainComns, a blockchain infrastructure support organization. In it we share the best practices for the use of advanced cryptographic tools in improving the care, maintenance, control, and protection of your digital assets. (1/14)
Mon Jun 01 20:55:43 +0000 2020
In the year since the release of our #SmartCustody digital-asset checklists, resources, and risk modeling there have been many changes to our ecosystem. For example, last year’s edition could only safely recommend single-signature cold storage approaches for self-custody. (4/14)
Mon Jun 01 20:55:44 +0000 2020
These resources, paid for by your fellow patrons in the Bitcoin and cryptocurrency digital-asset community, are available for free in the PDF http://bit.ly/SmartCustodyBookV101 and at cost in a print-on-demand book http://bit.ly/SmartCustodyBookViaLulu (3/14)
Mon Jun 01 20:55:44 +0000 2020
In the 1st edition of #SmartCustody we detail best practices & default storage scenarios, offer an exercise for you to learn how to model digital asset flows, create a risk model, do an adversarial analysis, and use these tools to modify your personal storage scenario. (2/14)
Mon Jun 01 20:55:44 +0000 2020
As @BlockchainComns begins work on a major new release of a 2nd edition #SmartCustody, I thought I’d share with you personally some of my own thoughts on how I think about digital asset security, risk modeling, and adversarial analysis. (6/14)
Mon Jun 01 20:55:45 +0000 2020
However, a number of wallets’ architectures have since become more mature. So we now feel that multi-sig solutions are feasible for use by regular people. (5/14)
Mon Jun 01 20:55:45 +0000 2020
Classic risk-modeling indentifies vulnerabilities and turns those vulnerabilities into risks based on likelihoods and consequences. You’ll still find all of that in #SmartCustody. It’s only after we’ve identified these initial risks that we bring in our adversaries. (9/14)
Mon Jun 01 20:55:46 +0000 2020
Classic risk-modeling techniques can be overwhelming, so the #SmartCustody book offers a different approach that helps users to protect their digital assets by figuring out what endangers them. I do this using a unique method: exposing ADVERSARIES. (8/14)
Mon Jun 01 20:55:46 +0000 2020
The first thing I’d like to share is particularly unique to how I approach the risk-modelling of digital assets: Adversarial Analaysis. I believe you may find it useful, so I’ll be sharing my thoughts about these Adversaries throughout the month of June. (7/14)
Mon Jun 01 20:55:46 +0000 2020
We can look at the motives of Death or Institutional Theft or Blackmail. We can consider what they want, even in situations when they’re not thinking beings. By better considering motives, we can better understand if an adversary is actually a threat to US. (12/14)
Mon Jun 01 20:55:47 +0000 2020
Why adversaries? Because they flip the script. We go from discussing somewhat vague and abstract vulnerabilities to considering something more concrete. In the abstract, we might fall prey to our own biases; when things are made concrete, we hew closer to reality. (11/14)
Mon Jun 01 20:55:47 +0000 2020
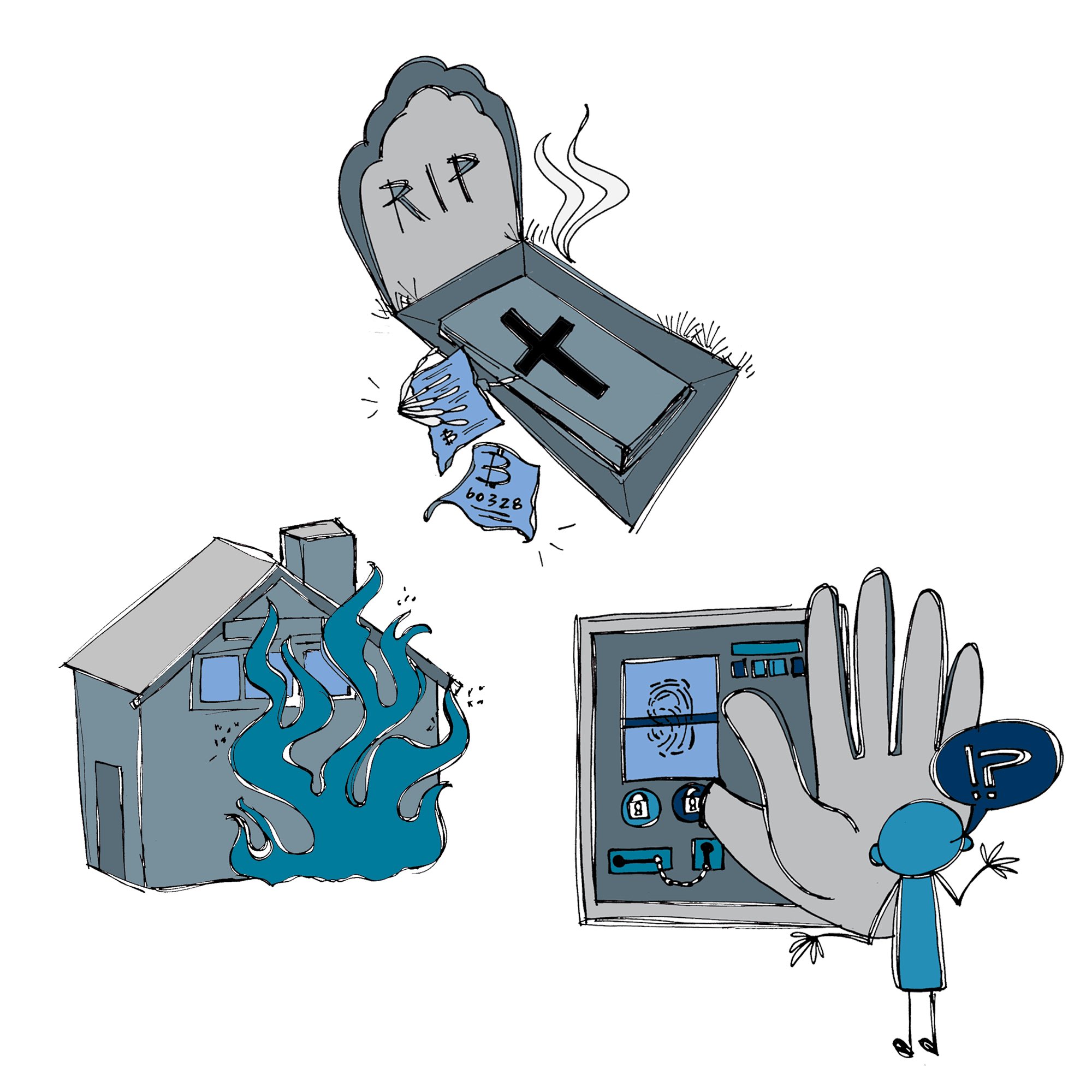
So what’s an adversary? It’s an anthropomorphized problem. Each one can encompass many different risks and have many different solutions. Losing your funds due to incapacitation is a potential risk, but DEATH, that’s an adversary. (10/14)
Mon Jun 01 20:55:47 +0000 2020
What do you think of adversaries? Are they useful for modeling risks? Let us know! And please consider supporting the #SmartCustodywork that this topic is drawn from. We’re need support for our 2nd edition, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (14/14)
Mon Jun 01 20:55:48 +0000 2020
Risk modeling is all about making informed decisions rather than emotional ones. I believe that adversaries help us to do so. I’ll be talking more about them in coming days, as I highlight the 27 adversaries in #SmartCustody. (13/14)
Mon Jun 01 20:55:48 +0000 2020
RT @ChristopherA: #SmartCustody is an ongoing project of @BlockchainComns, a blockchain infrastructure support organization. In it we share…
Tue Jun 02 16:38:55 +0000 2020
The adversaries in my #SmartCustody book are broadly divided into seven categories, the first of which is LOSS BY ACTS OF GOD. These are threats to your cryptocurrency and other digital assets that originate in bad luck. (1/6)
Tue Jun 02 16:43:40 +0000 2020
I imagine Loss of Acts of God as like a lightning strike. There’s often no warning, but the destruction can be total. (2/6)
Tue Jun 02 16:43:45 +0000 2020
When talking about adversaries, I look at both ulterior and explicit motivation. But, there’s nothing ulterior about Acts of God. They just happen! (3/6)
Tue Jun 02 16:43:49 +0000 2020
Nonetheless, we can still anthropomorphize motivations, and that’s where I think the adversarial modeling becomes very powerful. It helps us to understand these natural forces and whether they’re actually a danger to each of us. (4/6)
Tue Jun 02 16:44:00 +0000 2020
Specific adversaries in this category include: Death / Incapacitation; Denial of Access; and Disaster. I’ll be talking about each of these specifically in the next few days. (5/6)
Tue Jun 02 16:44:03 +0000 2020
Any thoughts on Acts of God category? Any specific adversaries that I missed? Let us know! And please support the #SmartCustodywork that this topic is drawn from. We’re working on our 2nd edition, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/
Tue Jun 02 16:44:10 +0000 2020
Adversary category “Loss by Actions of God” https://twitter.com/christophera/status/1267859439408697344?s=21 https://twitter.com/ChristopherA/status/1267859439408697344
Tue Jun 02 16:46:05 +0000 2020
RT @Appelcline: I like writing technical books too. I’ve done a few over the years. The most recent is the #SmartCustody book that I coauth…
Wed Jun 03 01:00:57 +0000 2020
#SmartCustody Adversary — Death/Incapacitation.
What is DEATH’s motivation? I imagine it as: “I am your last firing neurons, and I seek to drag everything you ever knew down with you, into the darkness.” (1/7)
Thu Jun 04 04:38:13 +0000 2020
Our best solution here? To relay your secrets. You have to make sure the private information that protects your digital assets lies somewhere outside of your own neurons, as we learned when considering the motivations of Death. (5/7)
Thu Jun 04 04:38:14 +0000 2020
QuadrigaCX is the biggest case we know of where funds were lost due to the holder’s death. Allegedly; that death is still in question. But currently it appears that $200M CAD became inaccessible. (4/7) https://www.engadget.com/2019-03-08-quadrigacx-bitcoin-missing-millions.html
Thu Jun 04 04:38:14 +0000 2020
Death/Incapacitation is one of the big ones: an adversary that anyone could face and that can endanger their digital assets for themselves, for their estates, and for their heirs. (3/7)
Thu Jun 04 04:38:14 +0000 2020
That’s my first adversary in the #SmartCustody course, where I anthropomorphize problems that you might face when securing your digital assets, to allow you to better, and less emotionally, model the actual risks. (2/7)
Thu Jun 04 04:38:14 +0000 2020
Have your own stories of Death impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2 of the book, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (7/7)
Thu Jun 04 04:38:15 +0000 2020
We only cover the digital asset basics about the Death adversary in the, but not much about inheritance law, but we highly recommend @pamelawjd’s book (and a sponsor of last year’s #SmartCustody v1 book) “Cyptoasset Inheritance Planning” (6/7) https://www.amazon.com/gp/product/1947910116/
Thu Jun 04 04:38:15 +0000 2020
Our first adversary in the category “Loss by Actions of God” — Death/Incapacitation:
https://twitter.com/christophera/status/1268401649728368640?s=21 https://twitter.com/ChristopherA/status/1268401649728368640
Thu Jun 04 04:39:39 +0000 2020
RT @FullyNoded: If you update to 0.20.0 you can now create BIP67 hd multi sig wallets with fully noded and your node 🖤
Thu Jun 04 05:14:33 +0000 2020
RT @trbouma: “If we are going to mandate digitization, human rights activists must demand that these tools are built with the interests of…
Thu Jun 04 08:15:13 +0000 2020
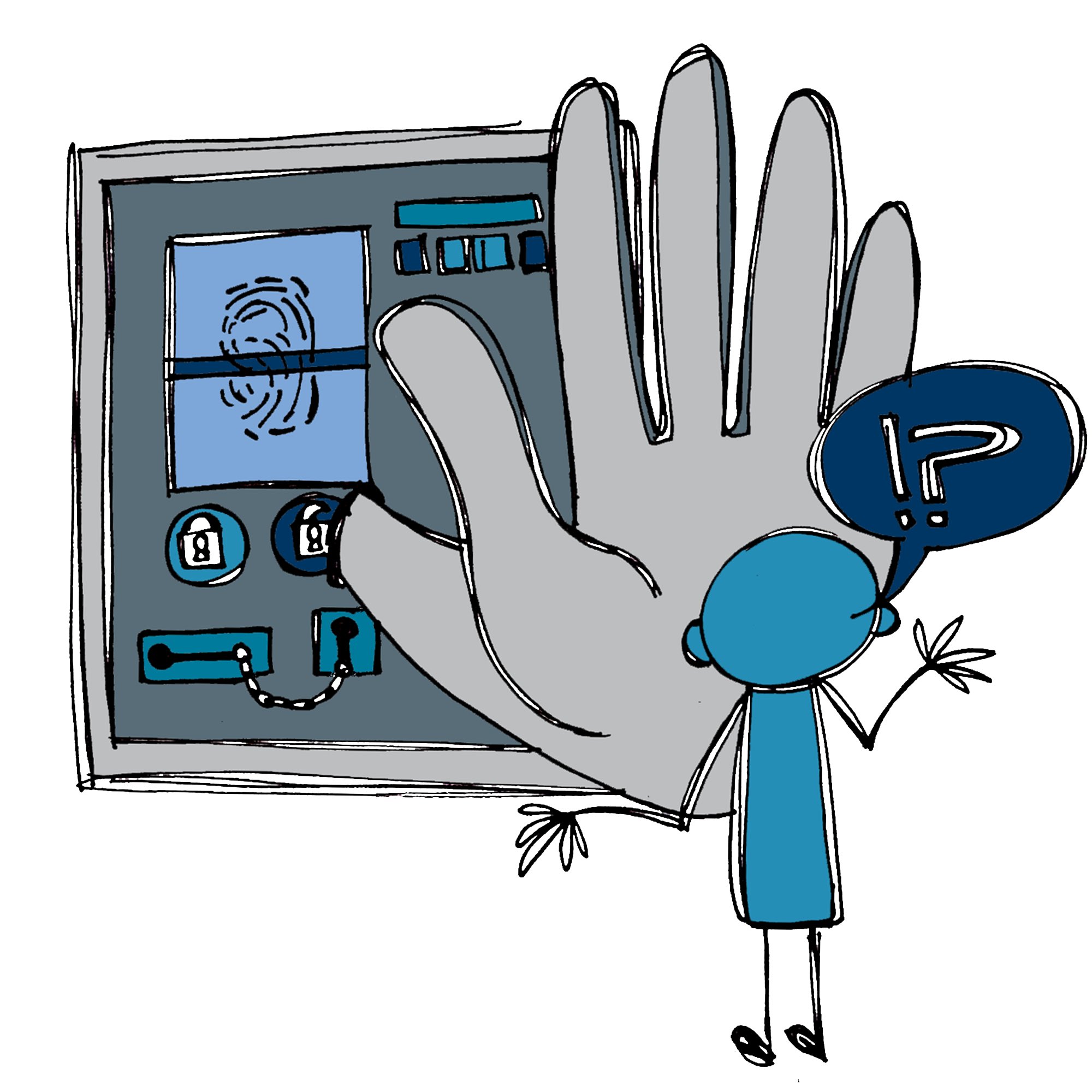
#SmartCustody Adversary — Denial of Access
DENIAL OF ACCESS is a very pragmatic adversary that can affect your cryptocurrency. What if you physically couldn’t get to the location where you stored the private keys that protect those assets? (1/9)
Thu Jun 04 13:12:55 +0000 2020
I had to imagine some less likely scenarios when I first wrote about this adversary, like storing keys in a corporate safe before the company went out of business, or with a friend who died. (2/9)
Thu Jun 04 13:12:56 +0000 2020
We take our freedom of movement for granted in the first world, and that may well be the case when all of this is done. But our #SmartCustody book anthropomorphizes adversaries so that you can better understand them and better consider the concretely. (5/9)
Thu Jun 04 13:12:57 +0000 2020
The recent riots offer another very real example of a physical DENIAL OF ACCESS. There might have been curfews blocking your access, or it might be unsafe to go and retrieve your cold storage keys. (4/9)
Thu Jun 04 13:12:57 +0000 2020
But we’ve seen a more likely situation in recent months: COVID-19 lockdowns. Banks have been accessible, but what if you left private keys with friends or family? It would have been illegal to retrieve them. What if they were at a work place and you couldn’t go there? (3/9)
Thu Jun 04 13:12:57 +0000 2020
There are of course other forms of DENIAL OF ACCESS. What if your hardware or processor manufacturer bricks or freezes all of your secure devices? Estonia did this is 2017 due to an security flaw, preventing access to all e-ID services. https://amp.insider.com/estonia-freeze-e-residency-id-cards-id-theft-2017-11 (7/9)
Thu Jun 04 13:12:58 +0000 2020
Think about where you store the secrets that protect your cryptocurrency and other digital assets. Is there any way you could lose access to that? (6/9)
Thu Jun 04 13:12:58 +0000 2020
Have your own stories of the DENIAL OF ACCESS adversary? Has COVID-19 already affected your own access? Any of your own solutions? Let us know! And please support #SmartCustody — we’re working on v2 of the book, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (9/9)
Thu Jun 04 13:12:59 +0000 2020
One of our top solutions is redundant storage. If you have keys in more than one place, particularly disparate sorts of places, then it’s less likely that you’ll lose access to all of them. Obviously, any solution may introduce its own adversaries as well. (8/9)
Thu Jun 04 13:12:59 +0000 2020
The second #SmartCustody adversary in the category of “Loss by Actions of God” — Denial of Access: https://twitter.com/christophera/status/1268531178916569088?s=21 https://twitter.com/ChristopherA/status/1268531178916569088
Thu Jun 04 13:17:46 +0000 2020
An example of this. I currently have a backup key not in the same county as my primary key, in case of big fires like we saw in recent years in California. But I’m still at risk in case of earthquake, so was considering moving it to Wyoming or EU. But given #COVID19? Not sure.
Thu Jun 04 20:39:29 +0000 2020
RT @ChristopherA: An example of this. I currently have a backup key not in the same county as my primary key, in case of big fires like we…
Thu Jun 04 20:39:36 +0000 2020
For more information on the rest of this series on digital asset adversaries covered in the first edition of the #SmartCustody book, see the first #tweetstorm where I am linking it all together: https://twitter.com/ChristopherA/status/1267560481855639553?s=20 https://twitter.com/ChristopherA/status/1267560481855639553
Thu Jun 04 20:44:42 +0000 2020
RT @kimdhamilton: @RadHertz @IdentityWoman @darrello @taykendesign @drummondreed @RuffTimo @realjoet @streetcred_id @psykoreactor @Christop…
Fri Jun 05 02:28:41 +0000 2020
RT @kimdhamilton: @RadHertz @IdentityWoman @darrello @taykendesign @drummondreed @RuffTimo @realjoet @streetcred_id @psykoreactor @Christop…
Fri Jun 05 02:28:51 +0000 2020
RT @kimdhamilton: @RadHertz @IdentityWoman @darrello @taykendesign @drummondreed @RuffTimo @realjoet @streetcred_id @psykoreactor @Christop…
Fri Jun 05 02:29:00 +0000 2020
RT @FullyNoded: If you use FN1 or 2 you can pass unsigned PSBTs to HWW for signing and back. FN2 forces you to verify the tx before its bro…
Fri Jun 05 03:01:14 +0000 2020
RT @FullyNoded: Here is the FN2 “confirm” view. Not only does it display all info to you, you may also tap each input and output to get the…
Fri Jun 05 03:01:22 +0000 2020
#SmartCustody Adversary — Disaster
DISASTER! Its motivation? “I want to destroy. I want to crumble and burn. I want to ruin with water, to blow things into the air. I am bombs, bullets, and explosions. I am sudden and unexpected but disastrous destruction.” (1/9)
Fri Jun 05 09:34:34 +0000 2020
When researching for my book, I heard the story of someone who religiously printed his keys to paper wallets. Every quarter he’d reprint so the ink didn’t fade (and would then shred the previous one). Unfortunately, he kept those keys in the basement. Which flooded. (3/9)
Fri Jun 05 09:34:35 +0000 2020
This is the third adversary in my #SmartCustody book about protecting your cryptocurrency and other digital assets. And the motivations certainly explain the ways that you could lose your private keys. A house fire, a flood, a tornado, a war. (2/9)
Fri Jun 05 09:34:35 +0000 2020
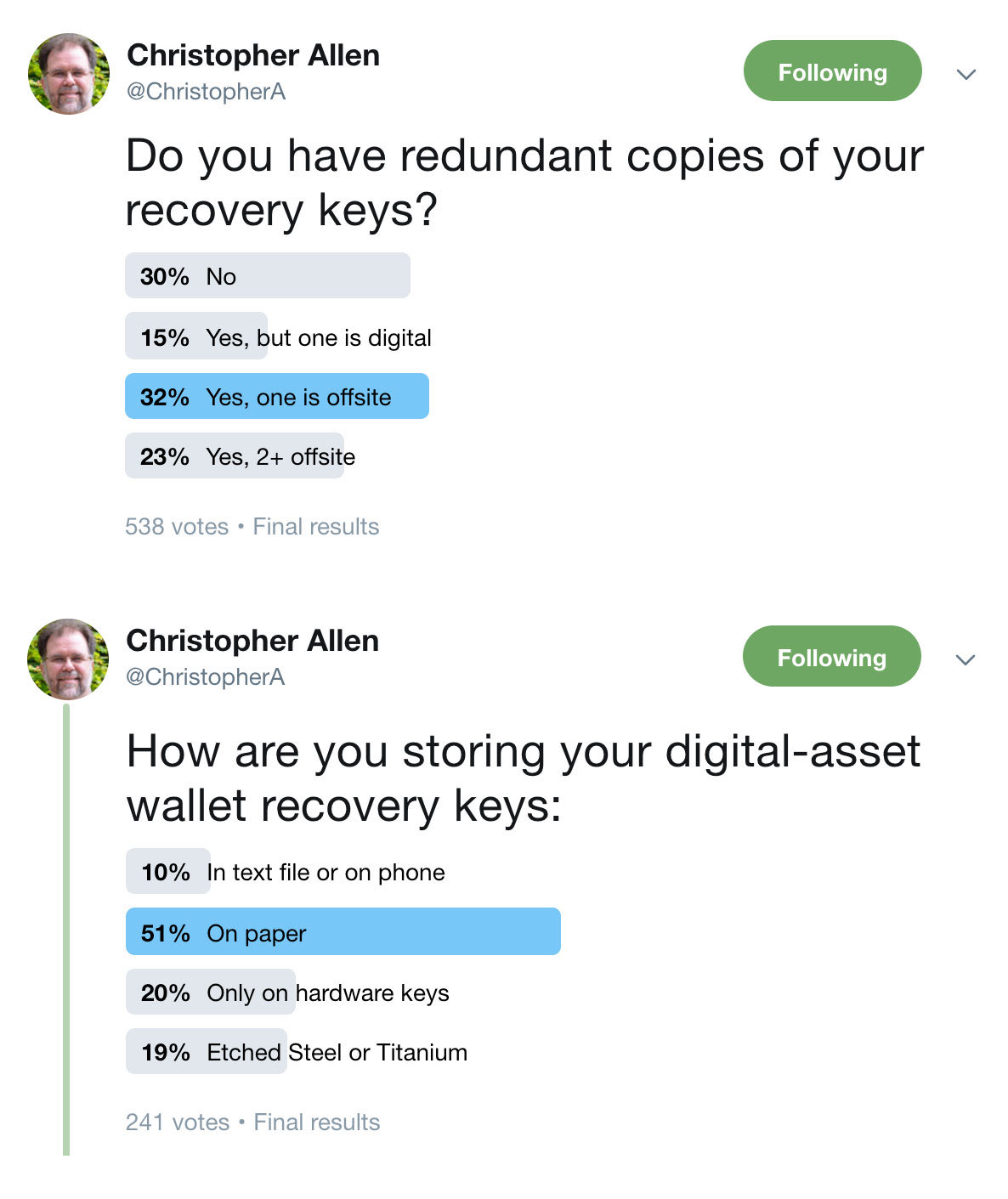
Last year I polled my Twitter followers about their own recovery key practices. 30% of them did not have redundant copies of their recovery keys & 51% still had their recovery keys only on paper! I live in California, but everywhere you may be vulnerable to some DISASTER. (4/9)
Fri Jun 05 09:34:37 +0000 2020
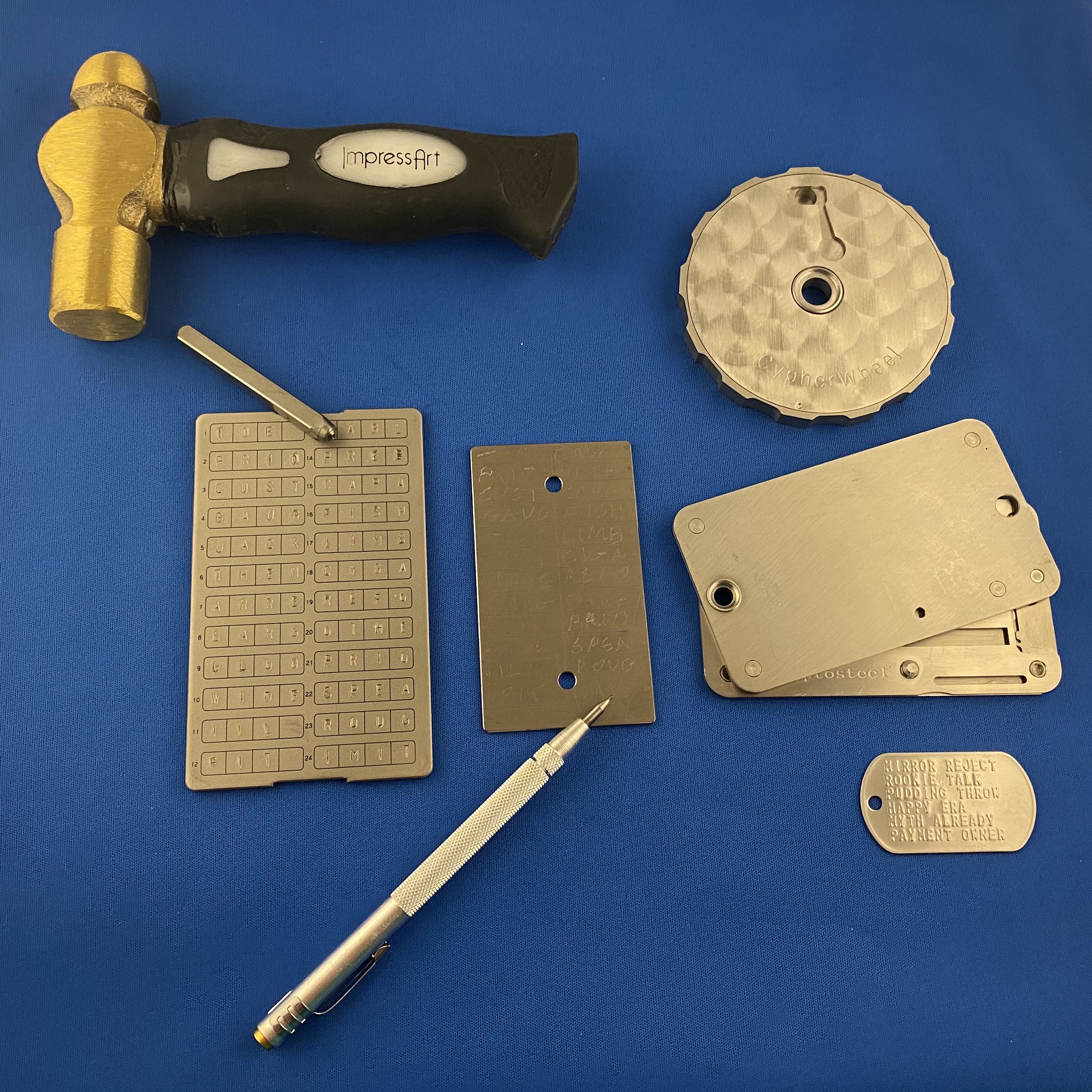
I suggest physically reinforcing your key storage as the best way to defend against disaster. If you use paper, it should be waterproof with permanent ink, but it’s even better to stamp or etch your keys into steel or titanium plates. And it’s quite easy to do! (5/9)
Fri Jun 05 09:34:39 +0000 2020
The important thing here is to consider which disasters are most likely to strike the location where you store your keys. (And, as always, how likely they are) Because fire, earthquake, tornado, and warfare all expose different vulnernabilities. (7/9)
Fri Jun 05 09:34:40 +0000 2020
My cold storage scenario even talks about some of the tradeoffs of different types of metals and other storage devices when applied to truly out-of-bounds temperature changes. (6/9) https://github.com/BlockchainCommons/SmartCustodyBook/blob/master/manuscript/02-scenario.md
Fri Jun 05 09:34:40 +0000 2020
Have your own stories of DISASTER impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2 of the book, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (9/9)
Fri Jun 05 09:34:41 +0000 2020
And that’s the last of my category”Acts of God” adversaries. In the last few days I also covered Death / Incapacitation & Denial of Access. Which are most likely to affect You? (8/9)
Fri Jun 05 09:34:41 +0000 2020
Our third #SmartCustody adversary, our last in the category of “Loss by Actions of God” — Disaster: https://twitter.com/christophera/status/1268838617012568065?s=21 https://twitter.com/ChristopherA/status/1268838617012568065
Fri Jun 05 09:35:40 +0000 2020
Replying to @DestrySaul and @BlockchainComns
In general PSBT (partially signed bitcoin transaction) is still fairly new, as is multisig in general. Older hardware (Ledger, Trezor, etc) also have some assumptions about there being only single seed on the device and a single account used a a time. …
Fri Jun 05 19:03:34 +0000 2020
Replying to @DestrySaul and @BlockchainComns
I know that as we are developing the @FullyNoded 2 multisig bitcoin app that we are encountering that these assumptions have caused a number of interesting new attack surfaces now that we have multiple devices and multiple account paths involved. …
Fri Jun 05 19:06:22 +0000 2020
Replying to @DestrySaul, @BlockchainComns and @FullyNoded
Some of these potential attack surfaces were addressed last year, but I’m not surprised that another attack surface emerged just now. I would not be surprised if there are a few more PSBT issues that the ecosystem will have to address this year as more multisig wallets evolve.…
Fri Jun 05 19:10:33 +0000 2020
Replying to @DestrySaul, @BlockchainComns and @FullyNoded
Right now @BlockchainComns is facilitating & hosting conversations about a number of multisig issues with a number of wallet vendors in Github and in a private Signal group. Most are newer wallet companies, and though we’ve heard from @Ledger & @Trezor they have not been active…
Fri Jun 05 19:12:48 +0000 2020
Replying to @DestrySaul, @BlockchainComns, @FullyNoded, @Ledger and @Trezor
Many of these new problems will only become visible when we test multisig with multiple wallet vendors. Currently @FullyNoded tests against @ElectrumWallet, @COLDCARDwallet, @unchainedcap’s Caravan, and soon a few more. …
Fri Jun 05 19:18:37 +0000 2020
If you like what @BlockchainComns is doing to address these kinds of problems by increasing our ability to interoperate & not be locked into a single wallet vendor, I encourage your financial support at https://btcpay.blockchaincommons.com or contribute engineering talent to our cause.
Fri Jun 05 19:21:21 +0000 2020
RT @ChristopherA: @DestrySaul @BlockchainComns @FullyNoded @Ledger @Trezor @ElectrumWallet @COLDCARDwallet @unchainedcap If you like what @…
Fri Jun 05 19:22:12 +0000 2020
Replying to @DestrySaul, @BlockchainComns, @FullyNoded and @BobMcElrath
There are a number of not-collaboratively designed details about how hardware wallets do HD keys that have never been properly documented, only repeatedly reverse engineered. For instance, the derivation m/48’ used by existing hardware wallet vendors is unique & has issues. …
Fri Jun 05 19:25:38 +0000 2020
Replying to @DestrySaul, @BlockchainComns, @FullyNoded and @BobMcElrath
I suspect that if anything we are going to have have more conventions & rules about use of HD key paths, wallet descriptors, PSBT, etc. in the future, many of which may force users to sweep their keys to keep up. This is not desirable & should be avoided, but probably necessary.
Fri Jun 05 19:28:21 +0000 2020
RT @ChristopherA: @DestrySaul @BlockchainComns @FullyNoded @BobMcElrath There are a number of not-collaboratively designed details about ho…
Fri Jun 05 19:28:27 +0000 2020
RT @ChristopherA: @DestrySaul @BlockchainComns @FullyNoded @BobMcElrath I suspect that if anything we are going to have have more conventio…
Fri Jun 05 19:28:29 +0000 2020
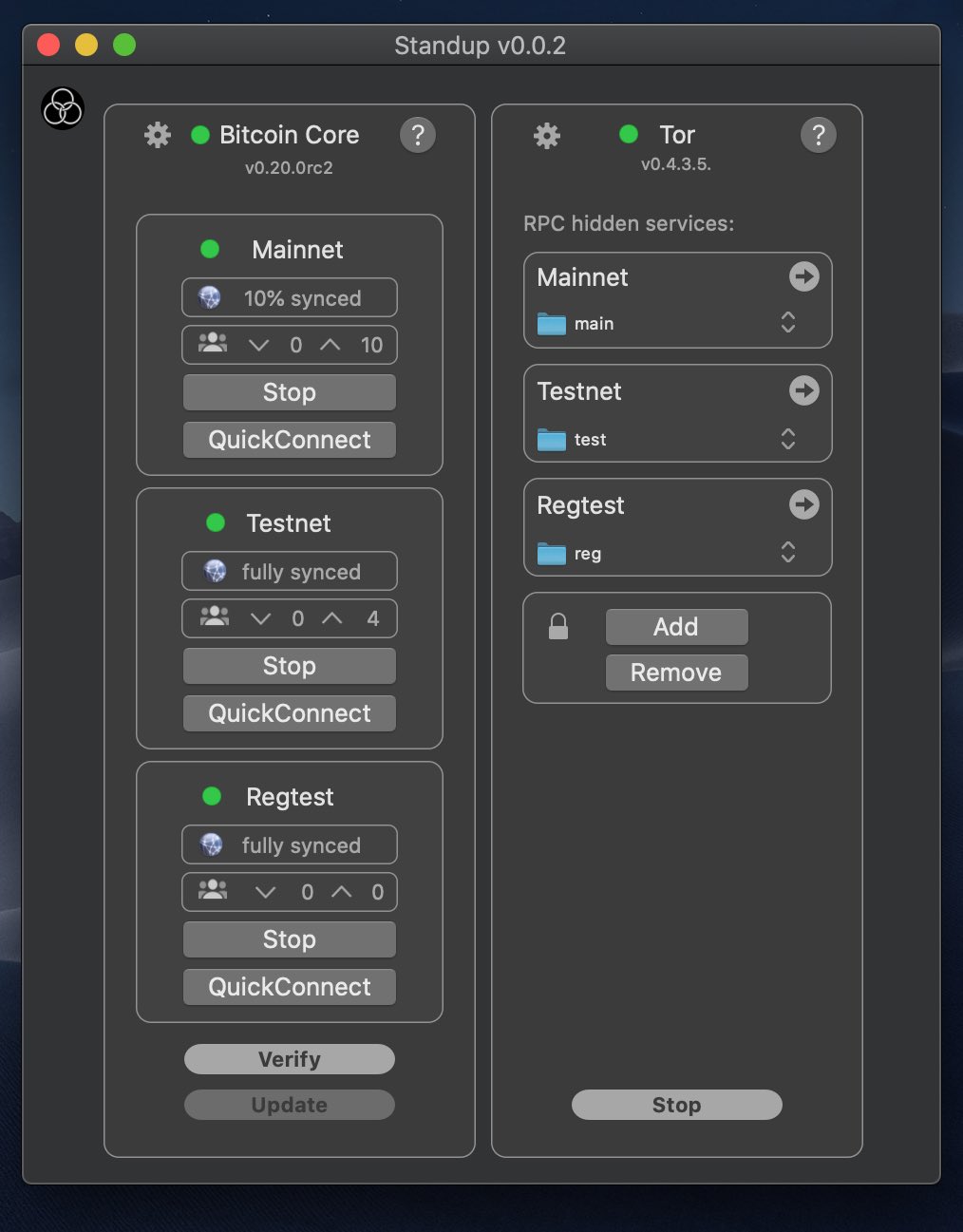
RT @FullyNoded: 1. ⚠️ Major announcement! Standup is finally ready for you all to try out!!! 🤩 Easily install Bitcoin Core and Tor and setu…
Sat Jun 06 05:07:26 +0000 2020
RT @FullyNoded: Major shoutout to @ChristopherA and @BlockchainComns for making this app and a ton of other amazing bitcoin projects a poss…
Sat Jun 06 05:13:15 +0000 2020
In addition to being the full node half of our @FullyNoded 2 iOS app, it is also available from your command line if you want to use it with my “Learning Bitcoin from the Command Line” course. Best way to really learn Bitcoin! https://github.com/BlockchainCommons/Learning-Bitcoin-from-the-Command-Line https://twitter.com/FullyNoded/status/1269132911279632384
Sat Jun 06 05:17:22 +0000 2020
Replying to @DestrySaul, @BlockchainComns, @FullyNoded and @BobMcElrath
I agree that there should be more open deliberation among the developer community. That is part of what Blockchain Commons is all about. …
Sat Jun 06 07:08:53 +0000 2020
Replying to @DestrySaul, @BlockchainComns, @FullyNoded and @BobMcElrath
I’m the co-author of the TLS protocol, the world’s most successful cryptographic protocol. It won because we out collaborated Microsoft & Visa/Mastercard who wanted to own the early commercial internet. I’m co-chair of the W3C Credentials CG. I believe in open standards.
Sat Jun 06 07:09:51 +0000 2020
RT @FullyNoded: Just in case it’s lost in the thread, just clicking this link will download the mac app via our github. Could not be easier…
Sat Jun 06 08:00:37 +0000 2020
RT @unchainedcap: The @FullyNoded wallet by @ChristopherA and team is the first mobile wallet to be able to interact with Caravan. Here’s a…
Sat Jun 06 17:22:34 +0000 2020
Replying to @La__Cuen
I know I’m frustrated that my personal KYC data is with a number of exchanges, and there is no way to delete it now that I now longer use some of them. I’m also frustrated that exchanges want me to email them personal KYC data (@krakenfx most recently) which disturbs me.
Sat Jun 06 19:16:51 +0000 2020
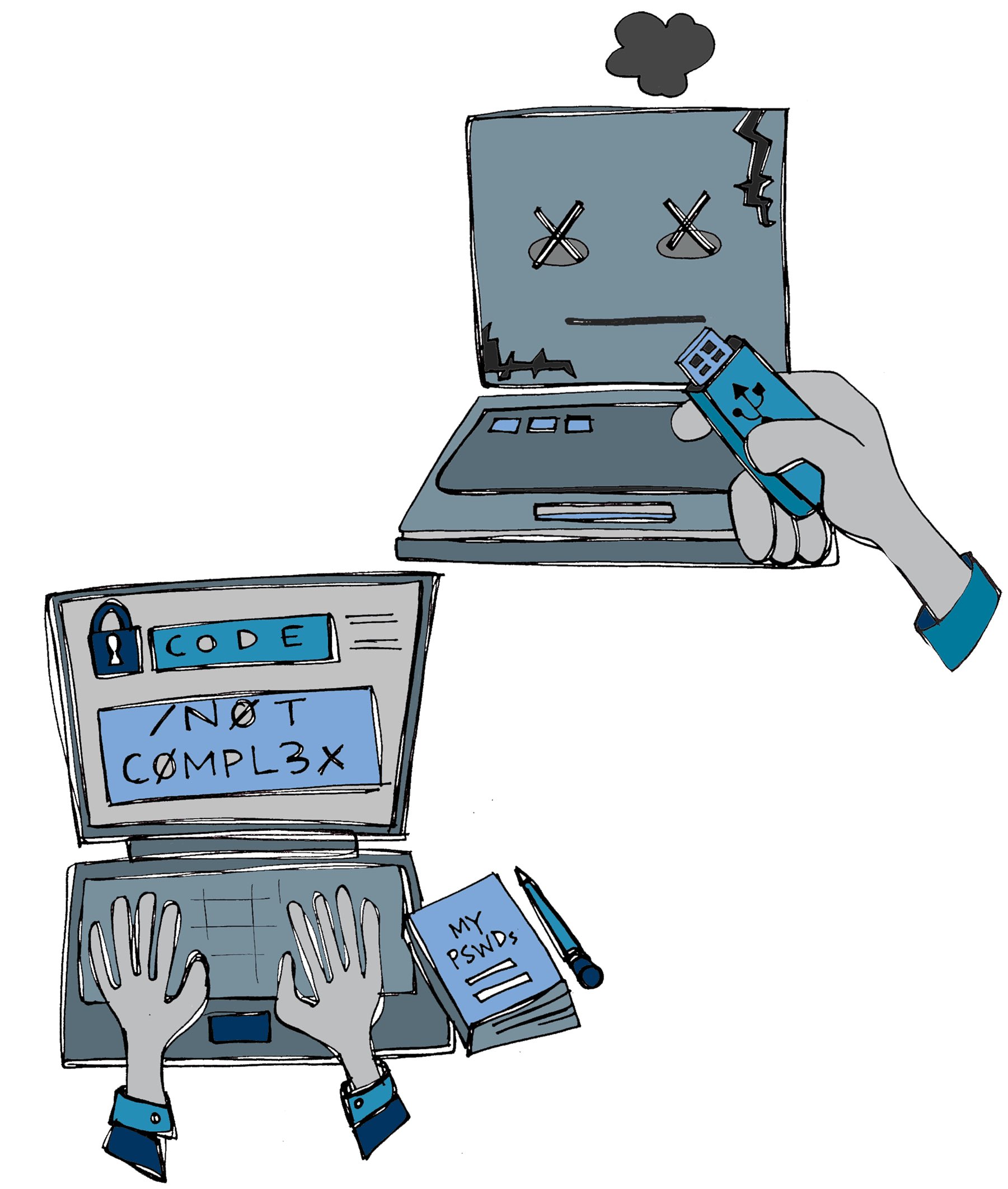
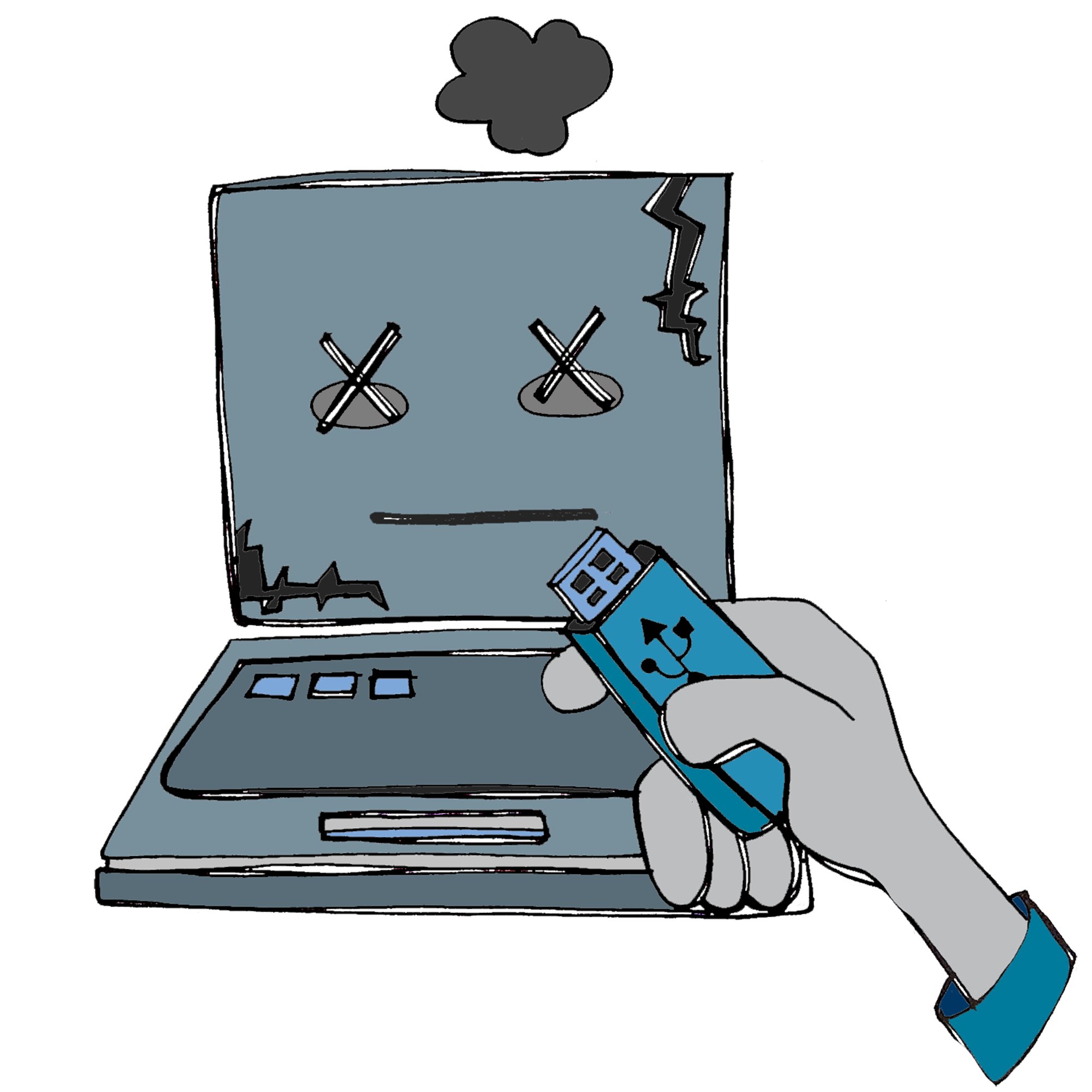
#SmartCustody Category — Loss by Computer Error
Cryptocurrency is innately digital: it’s stored on computers. That’s why LOSS BY COMPUTER ERROR may terrify us the most among adversaries that could steal away those assets. It’s the second category of adversaries in my book .(1/7)
Sun Jun 07 00:25:46 +0000 2020
Like the category Acts of God, this is another pretty faceless category. Computer Error is just an Act of God affecting the electronic world instead of the physical world. But unlike it we often can point to people causing errors rather than from an uncontrollable force. (2/7)
Sun Jun 07 00:25:49 +0000 2020
Like many of us, I imagine Computer Error as smoke billowing up from a computer whose lights have just blinked out forever. It’s a terrifying image. (3/7)
Sun Jun 07 00:25:50 +0000 2020
But, there are actually lots of ways that computers can eat up your cryptocurrency and other digital assets. Time and neglect may actually be the enemies most likely to turn your computers against you. (4/7)
Sun Jun 07 00:25:52 +0000 2020
I include two specific adversaries in this category: BITROT and SYSTEMIC KEY COMPROMISE. That’s your computer becoming unusable; and your keys proving insecure. I’ll explain them more in the next few days. (5/7)
Sun Jun 07 00:25:53 +0000 2020
And though I talk about how terrifing LOSS BY COMPUTER ERROR is, remember that the goal of anthropomorphizing threats is always to look at them more bloodlessly. Consider these adversaries and ask, “Is this likely to happen to me?” (6/7)
Sun Jun 07 00:25:55 +0000 2020
Any thoughts on Computer Error? Any specific adversaries that I missed? Let us know! And please consider supporting the #SmartCustodybook that this is drawn from. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (7/7)
Sun Jun 07 00:25:56 +0000 2020
Our second major #SmartCustody adversary category is “Loss by Computer Error”: https://twitter.com/ChristopherA/status/1269425280008876032?s=20 https://twitter.com/ChristopherA/status/1269425280008876032
Sun Jun 07 00:28:18 +0000 2020
RT @BTCSocialist: #DIY #bitcoin hardware wallet, with Morse code passphrase, on @M5Stack, hiding behind #Tetris!
Built using @StepanSnigi…
Sun Jun 07 16:48:37 +0000 2020
Replying to @BTCSocialist and @WorldCryptoNet
We are working on QR code standards for export & importing xpubs and PSBTs. For instance you could send the xpub as a QR code to @FullyNoded 2 or Spectre or @CoboVault & more to watch & prespare PSBT to be signed. Similarly can return signed PSBT via animated QR to be posted.
Sun Jun 07 16:55:55 +0000 2020
Replying to @PyVitor, @RuffTimo, @PelleB and @IdentityWoman
I’ve been architecting the @FullyNoded 2 iOS Wallet to be able to support the DID BTCR method, and in general trying to understand the architectural challenges of wallets that do both cryptocurrency & decentralized identify safely. A challenge!
Sun Jun 07 18:33:04 +0000 2020
Replying to @van_flymen and @JustinMoon
Don’t forget to share a link to my “Learning Bitcoin from the Command Line” course. It has a big section on leveraging RPC. We also welcome PRs to improve it. https://github.com/BlockchainCommons/Learning-Bitcoin-from-the-Command-Line
Mon Jun 08 01:53:02 +0000 2020
Replying to @van_flymen and @JustinMoon
Someone pointed your live stream to me in amusement while you were installing Bitcoin on a Mac. You might find the the install script in my course useful. We also have a one-click MacOS installer now at https://github.com/BlockchainCommons/Bitcoin-Standup-MacOS which automates the whole thing.
Mon Jun 08 01:55:31 +0000 2020
Replying to @JustinMoon, @Hodl8333 and @KG81
https://twitter.com/ChristopherA/status/1269809629023764480?s=20
Mon Jun 08 01:56:07 +0000 2020
Replying to @JustinMoon, @Hodl8333 and @KG81
https://twitter.com/ChristopherA/status/1269810255300456448?s=20
Mon Jun 08 01:56:55 +0000 2020
RT @chiselinc: I’m pleased to say I’m participating in @ChristopherA’s upcoming mini-team internship for @BlockchainComns, contributing to…
Mon Jun 08 05:12:24 +0000 2020
Replying to @mikeinspace and @FullyNoded
The design of FullyNoded2 is to take advantage of the fact that you can create Swift-based iOS apps & use the code to develop Mac apps in for Mojave. However, there have been some “gotchas”. Maybe this month’s WWDC will address the ones from Apple, but library fixes needed too.
Mon Jun 08 15:55:41 +0000 2020
#SmartCustody Adversary — Bitrot
Our first category “Loss by Computer Error” adversary is BITROT. It encompasses the many ways that you could lose digital assets & cryptocurrency through failure of your electronic storage. (1/10)
Mon Jun 08 16:46:43 +0000 2020
The most obvious is your computer flat-out dying, smoke billowing up from it. You could have a hard drive crash. Your cheaply made USB key could stop working. Any hardware failure could endanger access to your private keys. (2/10)
Mon Jun 08 16:46:44 +0000 2020
It’s all about entropy as I write in its motivation: “I am entropy writ large. I want to break down your storage, crash your hard drives and degrade your optical media. I want to prevent your computers from booting, your programs from running, and your data from reading”. (4/10)
Mon Jun 08 16:46:45 +0000 2020
But, there are less obvious & more subtle ways that your storage could fail. A software wallet could stop working with the newest upgrade of your operating system. Standards for digital-key storage could change, so that your recovery method is no longer recognized. (3/10)
Mon Jun 08 16:46:45 +0000 2020
It was BITROT when one user talked about have a 15-word recovery seed, but said that he didn’t know what software had generated it. (5/10) https://bitcoin.stackexchange.com/questions/65171/how-to-restore-wallet-from-15-word-seed-mnemonic
Mon Jun 08 16:46:46 +0000 2020
It was sort of BITROT when James Howells disposed of a laptop computer before remembering that it had Bitcoins on it. (6/10) https://www.cnbc.com/2017/12/20/man-lost-127-million-worth-of-bitcoins-and-city-wont-let-him-look.html
Mon Jun 08 16:46:47 +0000 2020
You also want to fully test your procedures before actually relying on them, especially your recovery procedures. Delete your hardware wallet’s seed, restore from scratch, and see if your test transaction comes back before using that key for substantial funds. (8/10)
Mon Jun 08 16:46:48 +0000 2020
The best way to avoid Bitrot is to maintain backups of not just your machine’s data, but also its operating system, and information on how you set it up. You want to be able to recreate the exact machine that once contained your digital assets. (7/10)
Mon Jun 08 16:46:48 +0000 2020
Our free #SmartCustody book offers a number of checklisted procedures for you to test against BITROT. We’re working on V2, with multi-sigs and other expansions. Support this new edition at https://smartcustody.btcpay.blockchaincommons.com/ (10/10)
Mon Jun 08 16:46:49 +0000 2020
We also suggest that you test your recovery processes at least anually. I actually use a two-phase recovery process, one focused on local keys and hardware in spring, and the other focused on my remote backup sets of keys in the autumn. (9/10)
Mon Jun 08 16:46:49 +0000 2020
Our first #SmartCustody adversary in the category “Loss by Computer Error” is Bitrot: https://twitter.com/ChristopherA/status/1270034533270745095?s=20
Mon Jun 08 16:52:27 +0000 2020
We had over 20 applications this year for a summer internship at Blockchain Commons. I usually pick just one, but given social distancing, travel restrictions, etc. I decided to try something different—virtual team intership. We have 7 excited students working together to learn! https://twitter.com/ChristopherA/status/1262826694726975489
Mon Jun 08 20:10:39 +0000 2020
This is our first week. We focused now on defining at least one project deliverable for each intern to be a lead on. It is needs to be something achievable in our short summer timeframe, but also something they can be proud of.
Mon Jun 08 20:16:32 +0000 2020
The projects are quite varied, as are the interns. One project emerging is an .onion bitcoin price feed that you can host yourself but also share, electrum-server style. Others are improvements to Bitcoin Standup, such as adding Lightning support, etc.
Mon Jun 08 20:19:04 +0000 2020
Another set of projects are hardware related, like adding xpub/zpub derived keys, and export via QR codes by #LetheKit.
Mon Jun 08 20:20:13 +0000 2020
Last year, Blockchain Commons helped @TheBlueMatt set up a Tor exit node at @nycmesh (a commons good that we all are using and should be supporting). Another intern project is to set up a 2nd @torproject , likely in Asia.
Mon Jun 08 20:22:09 +0000 2020
RT @chiselinc: So excited to be a part of this: we will be documenting the process for @BlockchainComns & hopefully paving a clearer path f…
Mon Jun 08 20:28:50 +0000 2020
RT @jodobear: A little less than 3 years ago I started learning computers because #Bitcoin happened to me and now finally, I got an opportu…
Mon Jun 08 20:28:52 +0000 2020
RT @fakhrulKhir: 2 years ago, I joined a blockchain startup here in Malaysia and started to learn a lot about blockchain. Now getting my ha…
Tue Jun 09 15:59:18 +0000 2020
#SmartCustody Adversary — Systemic Key Compromise
Here’s an adversary for your cryptocurrency (or other digital assets) that you might not have thought about: SYSTEMIC KEY COMPROMISE. What if the software that generated your keys did so in an insecure way? (1/11)
Tue Jun 09 19:32:39 +0000 2020
This is one of the “Loss by Computer Error” adversaries in my #SmartCustody book, and it’s broadly a software programming error: someone messed up the key-generation code and it creates keys that either have less entropy than intended or that can be systemically guessed! (2/11)
Tue Jun 09 19:32:40 +0000 2020
This is NOT just a theoretical idea. After one software update, http://Blockchain.info generated insecure keys for 0.0002% of their users. 250 Bitcoins subsequently went missing. (3/11) https://cointelegraph.com/news/white-hat-hacker-returns-missing-bitcoins-to-blockchaininfo
Tue Jun 09 19:32:41 +0000 2020
Two years ago, we learned that JavaScript’s secureRandom() was neither entirely secure nor random. Insufficient entropy meant that hackers could brute-force coins. (4/11) https://btcmanager.com/vulnerability-in-javascript-function-may-mean-long-term-bitcoin-hodlers-are-at-risk/
Tue Jun 09 19:32:42 +0000 2020
Last week, the @Trezor hardware wallet did a software update to fix a security issue, that locked users out of access to funds in a number of Bitcoin multisig accounts when using some third-party software tools. (5/11) https://decrypt.co/31463/bitcoin-segwit-bug-fix-could-lock-wallet-users-out-funds
Tue Jun 09 19:32:43 +0000 2020
How do you solve a problem so far out of your control? You monitor news related to your hardware and software, and you have an emergency procedure in place so that you can immediately move funds if your keys might be vulnerable to compromise. (7/11)
Tue Jun 09 19:32:44 +0000 2020
SYSTEM KEY COMPROMISE may pretty abstract, but we have three examples of it actually happening. All of these failures have had widespread repercussions. This is why I advocate adversarial analysis: it helps you to look at the real likelihooods of vulernabilities. (6/11)
Tue Jun 09 19:32:44 +0000 2020
Another approach is to not to update hardware key firmware or software immediately, or have two devices and only upgrade one, and have a working backup of the old software. This allows you to move your funds to an updated, more secure wallet. (8/11)
Tue Jun 09 19:32:45 +0000 2020
Eternal vigilance is the price for the autonomy of decentralization. You’re taking centralized authorities out of the loop, but that means you need to bear the responsibility yourself! (9/11)
Tue Jun 09 19:32:46 +0000 2020
That’s my second and final form of “Loss by Computer Error” category of adversary, following up on yesterday’s look at BITROT. Together, they comprise the may ways that computers could case you to lose your assets. (10/11)
Tue Jun 09 19:32:47 +0000 2020
Have your own stories of SYSTEMIC KEY COMPROMISE impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (11/11)
Tue Jun 09 19:32:48 +0000 2020
Our second and last #SmartCustody adversary in the category “Loss by Computer Error” is Systemic Key Compromise: https://twitter.com/ChristopherA/status/1270438677940846592?s=20 https://twitter.com/ChristopherA/status/1270438677940846592
Tue Jun 09 19:35:16 +0000 2020
RT @ChristopherA: Last week, the @Trezor hardware wallet did a software update to fix a security issue, that locked users out of access to…
Tue Jun 09 19:35:41 +0000 2020
RT @ChristopherA: Another approach is to not to update hardware key firmware or software immediately, or have two devices and only upgrade…
Tue Jun 09 19:35:47 +0000 2020
The ulterior motive here is obvious: greed. There’s an active antagonist attacking you, and they want what you have. (2/8)
Wed Jun 10 17:45:15 +0000 2020
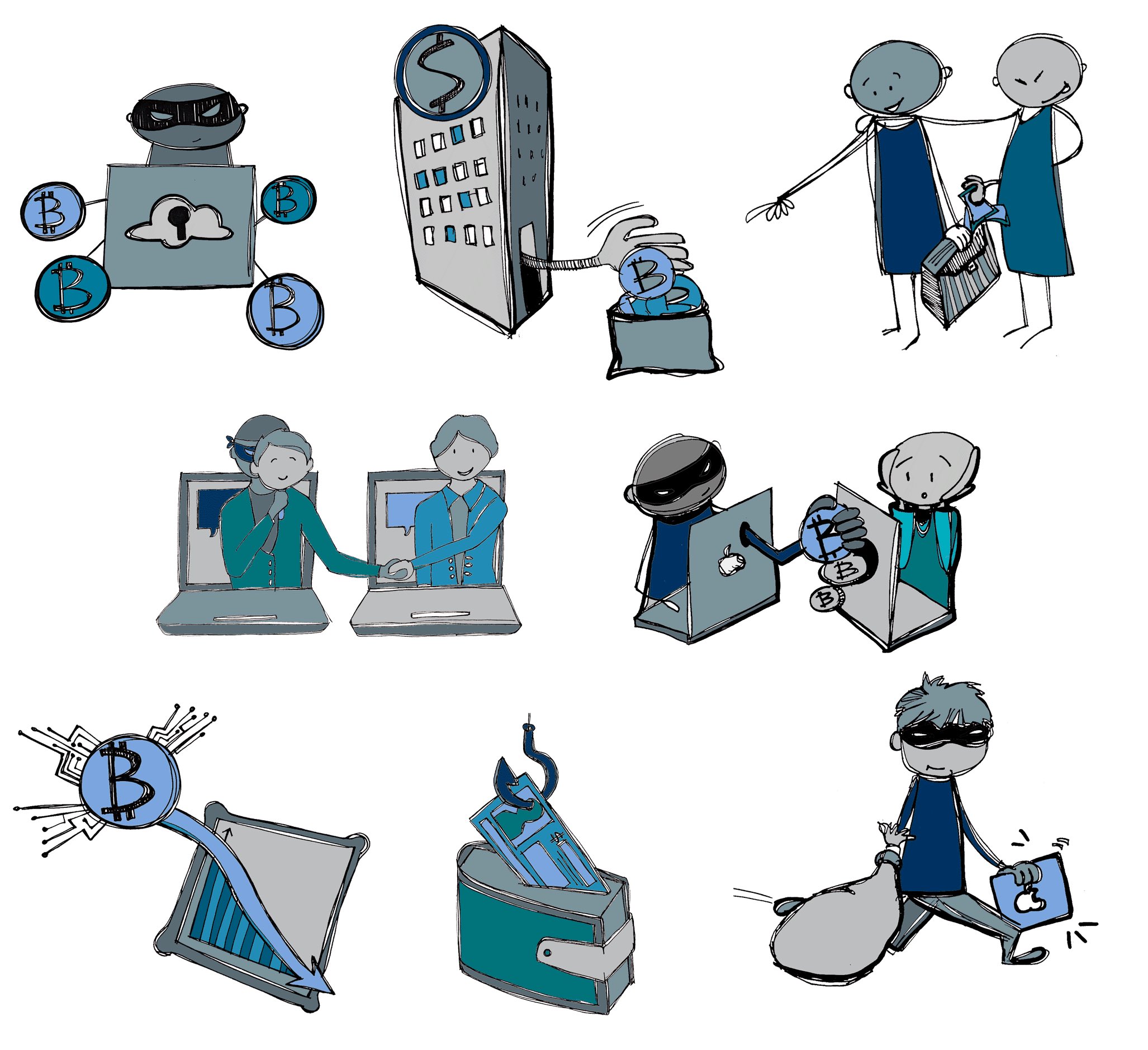
#SmartCustody Category — Loss by Crime, Theft
Cryptocurrency holders seem to be the most afraid of their digital assets being stolen. That’s my third category of #SmartCustody adversaries: LOSS BY CRIME, THEFT. And, it’s quite varied: I’ve got a whole week’s worth of them! (1/8)
Wed Jun 10 17:45:15 +0000 2020
I envision LOSS BY CRIME, THEFT as a masked burglar taking keys out of a safe while heist music plays in the background. But, honestly, theft is usually more subtle, not involving physical presence at all. (3/8)
Wed Jun 10 17:45:16 +0000 2020
Is LOSS BY CRIME, THEFT really the most worrisome danger to your digital assets? I personally think that the average holder is more likely to lose their funds due to accidentally misplacing the keys in some way: either a physical or computer loss. (4/8)
Wed Jun 10 17:45:17 +0000 2020
Are your keys stored at a public exchange? Are you a well-known hodler of Bitcoin? Do other people have access to your funds? These are all things that could increase the danger of this category of adversaries to you. (6/8)
Wed Jun 10 17:45:19 +0000 2020
But as always, #SmartCustody anthropomorphizes these adversaries and considers their motivations so that you can more bloodlessly think about whether you’re actually at risk. One at a time, rather than being overwhelmed by all possible threats at once. (5/8)
Wed Jun 10 17:45:19 +0000 2020
#SmartCustody details 8 different Theft adversaries: Institutional Theft, Internal Theft, Personal Network Attack, Systemic Network Attack, Casual Physical Theft, Sophisticated Physical Theft, Social Engineering, and Supply-Chain Attack. I’ll cover them over the next week. (7/8)
Wed Jun 10 17:45:20 +0000 2020
Any thoughts on the LOSS BY CRIME, THEFT category? Any other specific THEFT adversaries that I missed? Let us know! And please consider supporting the book this is drawn from, #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Wed Jun 10 17:45:21 +0000 2020
Our next category of adversaries are “Loss by Crime, Theft”: https://twitter.com/ChristopherA/status/1270774037782777856?s=20 https://twitter.com/ChristopherA/status/1270774037782777856
Wed Jun 10 17:46:39 +0000 2020
Our examples of this are mostly theoretical, as companies don’t like to publicize actual thefts of this sort. But an engineer could backdoor a system, a bank employee could physically steal something from a safety deposit box. (3/8)
Thu Jun 11 20:08:37 +0000 2020
#SmartCustody is all about figuring out what protects your personal assets best. Many might see an institution as being a strong protector, whether it be an exchange, a bank, or a lawyer. But you have to assess the gains against the dangers for your personal situation. (2/8)
Thu Jun 11 20:08:37 +0000 2020
#SmartCustody Adversary — Institutional Theft
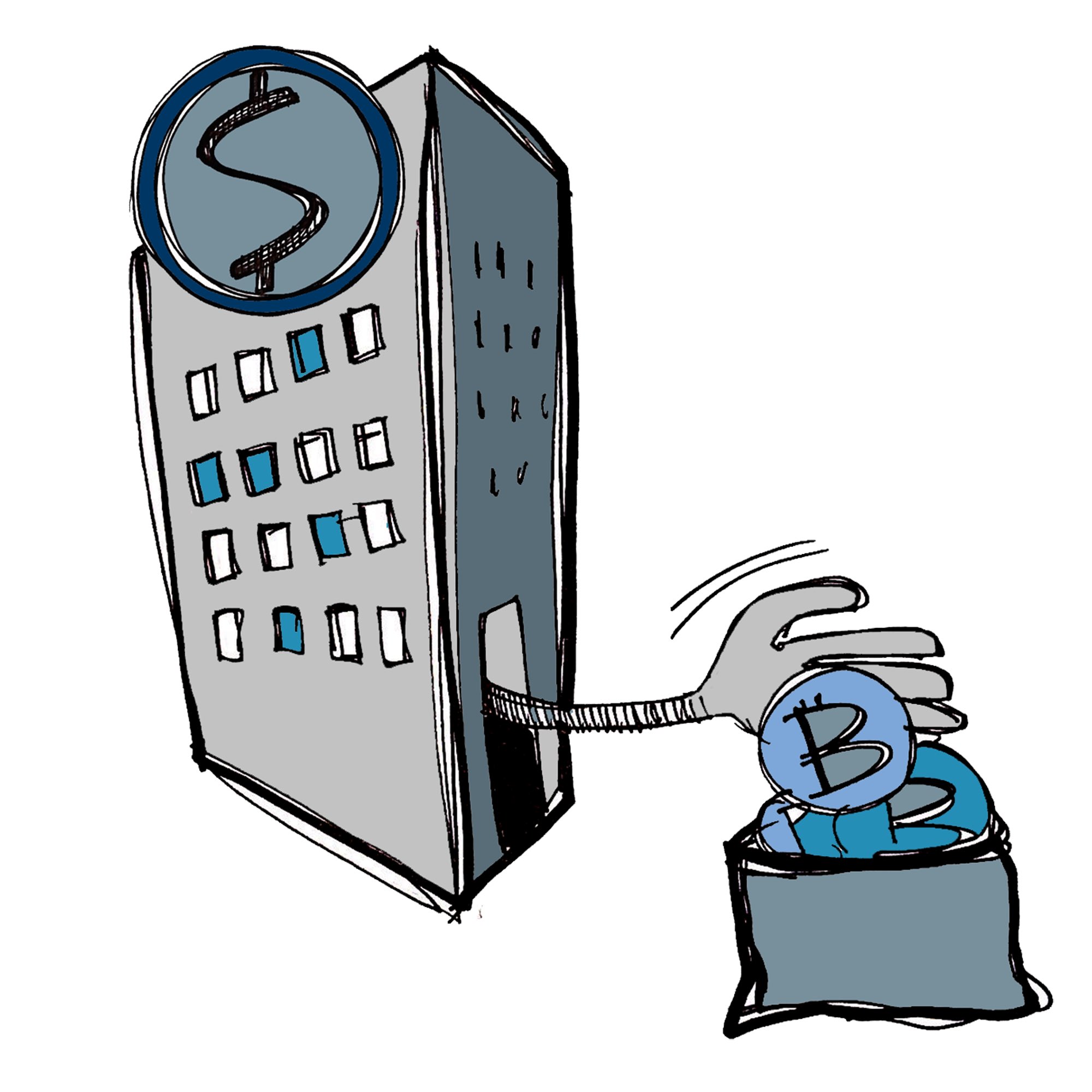
What’s INSTITUTIONAL THEFT? Here’s the motive: “I pretend to be a good employee, but I’m always waiting for my chance for a great score. I want to sift through the goods entrusted to my company and to take the best for myself.” (1/8)
Thu Jun 11 20:08:37 +0000 2020
How do you address this adversary? KYI! Know Your Institution. Be aware of its history and (politely) ask questions about how it addresses questions of personal responsibility. Ask your peers — recommendations can be pretty important too. (6/8)
Thu Jun 11 20:08:38 +0000 2020
Are the protections of your institution robust enough? That’s the question you have to ask, and it’s particularly important for cryptocurrency, where actual regulations may not have caught up with the rest of the financial world. (5/8)
Thu Jun 11 20:08:38 +0000 2020
Certainly there are protections against this sort of thing, often quite robust protections. For example, fiduciary responsiblity requires dual control to theoretically keep any single employee from engaging in theft. (4/8)
Thu Jun 11 20:08:38 +0000 2020
Have your own stories of INTERNAL THEFT impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Thu Jun 11 20:08:39 +0000 2020
As always when using these adversaries in a process to improve management of your own risks, the trick is to think of only adversary’s motive at a time. Don’t become overwhelmed by addressing all forms of theft at once. (7/8)
Thu Jun 11 20:08:39 +0000 2020
Our first #SmartCustody adversary in the category of “Loss by Crime, Theft” is INSTITUTIONAL THEFT: https://twitter.com/ChristopherA/status/1271172504787116032?s=20 https://twitter.com/ChristopherA/status/1271172504787116032
Thu Jun 11 20:09:53 +0000 2020
Replying to @TuurDemeester, @ericsavics1 and @kanzure
Given that you say that this appears to be a phishing attack, I doubt there is anything I can personally could do. However, to benefit others, I would appreciate learning details so that I can be sure to consider adding that to the next edition of our #SmartCustody book.
Fri Jun 12 16:02:58 +0000 2020
#SmartCustody Adversary — INTERNAL THEFT
We might not like to think about INTERNAL THEFT in our #SmartCustody scenarios, but what if someone you entrust with the keys to your digital kingdom decides to steal those assets? (1/7)
Fri Jun 12 16:10:09 +0000 2020
Unfortunately, money can change people. You might have a friend who’d put their life on the line for you, but when they realize they have the key to tens or hundreds of thousands of dollars in Bitcoins … they can do the unexpected. (2/7)
Fri Jun 12 16:10:11 +0000 2020
One of our real-life examples comes from the corporate world. ShapeShift’s internal IT Lead was entrusted with keys that gave him access to their hot wallet. He used it to steal 315 Bitcoins and fled. (3/7) https://news.bitcoin.com/looting-fox-sabotage-shapeshift/
Fri Jun 12 16:10:12 +0000 2020
During the Silk Road investigation, Secret Service agent Shaun Bridges stole funds from Silk Road, then he took monies seized from Bitstamp. (4/7) https://arstechnica.com/tech-policy/2015/12/rogue-secret-service-agent-who-stole-from-silk-road-sentenced-to-nearly-6-years/
Fri Jun 12 16:10:13 +0000 2020
And how do you resolve the problem? Dual control is a great answer, which for digital assets means multisignatures. Of course that introduces new issues of trying to protect multiple keys from loss. You always have to decide where the balance lies in #SmartCustody. (6/7)
Fri Jun 12 16:10:14 +0000 2020
So you ask: can you trust your employees? Can you trust your lawyer? Can you trust your spouse? Can you trust your friends? You need to understand all of their desires and motivations, and only then can you make unemotional decisions about these potential adversaries. (5/7)
Fri Jun 12 16:10:14 +0000 2020
Have your own stories of INTERNAL THEFT impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (7/7)
Fri Jun 12 16:10:15 +0000 2020
Our next #SmartCustody adversary in the category of “Loss by Crime, Theft” is INTERNAL THEMFT: https://twitter.com/christophera/status/1271474884497965056?s=21 https://twitter.com/ChristopherA/status/1271474884497965056
Fri Jun 12 16:12:42 +0000 2020
I have been asked to offer testimony today at the Wyoming Select Committee on Blockchain, Financial Technology and Digital Innovation Technology. Today’s focus is digital identity. The live stream is now available at https://www.youtube.com/watch?v=91ZA8rppgSA
Fri Jun 12 18:45:42 +0000 2020
RT @CaitlinLong_: LIVE STREAM of #Wyoming’s Select Committee on #Blockchain, Fintech & Innovation available here! Digital identity is the m…
Fri Jun 12 20:40:11 +0000 2020
My testimony to the Wyoming Legislature on #Decentralized #DigitalIdentity begins at roughly the 1 hour mark. https://www.youtube.com/watch?v=91ZA8rppgSA
Fri Jun 12 22:55:40 +0000 2020
Replying to @excelleliu and @adam3us
There are several “full node in the box” solutions out there: @nodl_it Rasbiblitz, etc. If you have a MacOS device you leave at home (mine is an old MacMini that I also use for videos) we offer a free “one-click” installer Bitcoin Standup: https://github.com/BlockchainCommons/Bitcoin-Standup-MacOS More soon.
Sun Jun 14 17:23:14 +0000 2020
Replying to @excelleliu, @adam3us and @nodl_it
All of the above I mention use QuickConnect that allows your mobile device to control your home full node via Tor. FullyNoded2 is one such—it is a single & multisig wallet for iOS that also leverages Tor for privacy. In alpha today, but beta mainnet soon: https://testflight.apple.com/join/OQHyL0a8
Sun Jun 14 17:28:43 +0000 2020
#TIL: The Korean word 손맛
son-mat, which describes the specific, irreplaceable flavor of someone else’s cooking. I’ve also seen it translated more literally “hand taste”or “the taste of one’s hands” but apparently it has a connotation of a “mothers hand taste”. ♥️👐 …
Sun Jun 14 22:34:07 +0000 2020
I’m also fascinated at the meta level how interconnected this rabbit-hole was. From language, to emotion, to culture, to family, to food, to microbiota, to changes in health, to changes in culture. And all easily available to an inquiring mind over the internet. A good feeling.
Sun Jun 14 22:34:08 +0000 2020
I find that this is also interesting in the context of rise of allergies, where there is a hypothesis that too much cleanliness may be one of the sources. It terns out research shows that allergic diseases is on the rise in Korea. Too much hand cleaning? https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5796968/
Sun Jun 14 22:34:08 +0000 2020
It turns out the in addition to the spirit of the concept, there might also be some truth, at least for Korean cooking, as it often uses fermentation. This is due to the microbiota of Mom’s hands. 3 out of 4 multigenerational family show continuation of hand yeasts in cooking. …
Sun Jun 14 22:34:08 +0000 2020
This was was such a lovely concept, I wanted to see if it was true. I jumped into a research rabbit-hole, ultimately finding this lovely video https://calls.ars.electronica.art/prix2019/prixwinner/31613/ …
Sun Jun 14 22:34:08 +0000 2020
A year ago my Kickstarter for a social storytelling cooperative card game “Gate Watch” was a success. I’d thought that I’d do a number of other small projects over the next few years. Unfortunately, these type of intimate in-person games are now difficult in days of COVID-19. … https://twitter.com/ChristopherA/status/1139638040358297600
Sun Jun 14 23:02:59 +0000 2020
I had planned a close sequel called “Twilight Road” this spring. Stories of journeys rather that stories of borders. The other side of the story from “Gate Watch”. Unfortunately, play testing has been difficult. I’m now puzzling out to adapt game for Zoom. …
Sun Jun 14 23:04:41 +0000 2020
For a cooperative storytelling game, Zoom + Screen Sharing isn’t that bad as in general these games all information is public. The problem is that TOO much information is public — it overwhelm’s the players. …
Sun Jun 14 23:06:35 +0000 2020
I’ve been working on some collaborative information overload solutions using presentation software and/or custom scripting, and it isn’t bad. But I’m realizing this isn’t just relevant to games — being overwhelmed is also a consequence of business meetings as well. …
Sun Jun 14 23:08:07 +0000 2020
So far, the key thing appears to be having up front a clear shared signal of what conversational modality are we in. Are we in information sharing? Brainstorming? Are we trying to make a decision? Are we trying to document to share with others? …
Sun Jun 14 23:10:35 +0000 2020
Not being aligned on these modalities is one of the problems in chat online. Another problem is where is other people’s attention? Google Docs has a trick where you can click on someone’s avatar and go to what they are looking at. …
Sun Jun 14 23:11:40 +0000 2020
What other types of problems might be solved with some type of screen-shared worksheet? Have you created anything like this in Google Docs, Google sheets, or other shared document environment? Do you have tricks doing screen sharing of a facilitative document? Let me know!
Sun Jun 14 23:13:28 +0000 2020
RT @ChristopherA: I’ve been working on some collaborative information overload solutions using presentation software and/or custom scriptin…
Sun Jun 14 23:13:48 +0000 2020
Replying to @liber_liver
We call this adversary “Process Fatigue”. The greater number of of wallets, the more steps required, subtle but important differences, etc. will increase your errors, or keep you from doing the work at all. I’m not saying don’t have heterogeneous wallets, but be careful of risks.
Mon Jun 15 20:08:36 +0000 2020
Replying to @phil_geiger and @skwp
https://twitter.com/christophera/status/1272622054110449664?s=21 https://twitter.com/ChristopherA/status/1272622054110449664
Mon Jun 15 20:11:48 +0000 2020
PERSONAL NETWORK ATTACK is a #SmartCustody adversary that comes in two parts. First, it’s an internet-based attack on digital assets, and second it’s directed at your personally. (1/7)
Mon Jun 15 20:16:50 +0000 2020
WiFi offers one of the prime vectors for this attack. If you connect to a free WiFi, someone might be spoofing the sites you’re connecting to and collecting your credentials. (2/7)
Mon Jun 15 20:16:52 +0000 2020
A user of Coinbase encountered a different sort of attack. After he invested in cryptocurrency, hackers broke into his T-Mobile account, used that to access Google’s 2FA, and used that to get into the Coinbase account. (3/7) https://fortune.com/2017/08/22/bitcoin-coinbase-hack/
Mon Jun 15 20:16:54 +0000 2020
This is one of the adversaries where you have the greatest personal agency in defeating it. It’s all about having great internet security: protecting your passwords, protecting your phone, and otherwise making sure that hackers can’t get to your credentials. (4/7)
Mon Jun 15 20:16:56 +0000 2020
Of course the alternative is just to hide the fact that you have cryptocurrency at all. Don’t tell people about it, don’t access it except from the safety of your home network. Security by Obscurity usually fails, but here you’re just not giving hackers a target. (5/7)
Mon Jun 15 20:16:57 +0000 2020
But you need to remain vigilant because this is a situation where the result is likely to be total loss: if hackers know you have cryptocurrency, and they attack you to get it, they’re going to take it all! (6/7)
Mon Jun 15 20:16:58 +0000 2020
Have your own stories of Personal Network Attack impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (7/7)
Mon Jun 15 20:16:59 +0000 2020
The PERSONAL NETWORK ATTACK is our next adversary in the “Loss by Crime, Theft” category:
https://twitter.com/christophera/status/1272624127719829504?s=21 https://twitter.com/ChristopherA/status/1272624127719829504
Mon Jun 15 20:29:03 +0000 2020
RT @bsfarrington: I haven’t wanted to share this news, but my father died late Thursday. But his last message needs to be heard. “In Bill’s…
Tue Jun 16 03:09:08 +0000 2020
RT @FullyNoded: The latest FullyNoded2 Testflight includes coin control features! Including “do not spend change” and “do not spend dust” a…
Tue Jun 16 15:13:53 +0000 2020
RT @artemkrt: @CandleHater @baidakova If you don’t, let me guess - you don’t want that nerdy mess?
I switched to YES answer right after tr…
Tue Jun 16 15:14:22 +0000 2020
The systemic attack on Betcoin Dice was quite involved. Hackers took over http://Ghash.io and stole its money, but simultaneously made bets at Betcoin Dice, and were able to double-spend because of their control of the network. (4/8) https://bitcointalk.org/index.php?topic=327767.0
Tue Jun 16 18:11:41 +0000 2020
The Blockchain Graveyard lists millions of dollars of systemic losses of this sort, with some of the companies closing down as a result, passing those losses on to their customers. (3/8) https://magoo.github.io/Blockchain-Graveyard/
Tue Jun 16 18:11:41 +0000 2020
Our adversary’s motivation: “I’m a big kahuna among hackers. I don’t go after your little bitcoin wallets, I go after the exchanges or other bitcoin sites instead. Nonetheless, you might just find yourself at a literal loss when I bankrupt the company holding your wallet.” (2/8)
Tue Jun 16 18:11:41 +0000 2020
#SmartCustody Adversary — Systemic Network Attack
Yesterday I talked about Personal Network Attack as a adversary that could threaten your digital assets. But what if attackers instead make a SYSTEMIC NETWORK ATTACK, going after your service providers? (1/8)
Tue Jun 16 18:11:41 +0000 2020
Have your own stories of SYSTEMIC NETWORK ATTACK impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Tue Jun 16 18:11:42 +0000 2020
How else can you avoid attacks on your providers, who are presumably very secure? That’s the heart of our self-custody scenario, which uses cold-storage rather than wallets on exchanges. (7/8) https://github.com/BlockchainCommons/SmartCustodyBook/blob/master/manuscript/02-scenario.md
Tue Jun 16 18:11:42 +0000 2020
The good news with this adversary is that you are not alone — everyone involved in the ecosystem wants to avoid these type of attacks. However, you should be sure that your wallet vendors, custodians, exchanges, etc. are competent to spot these before they are successful. (6/8)
Tue Jun 16 18:11:42 +0000 2020
A recent failed attack, but too close for comfort, a hacker tricked a provider of a non-bitcoin related source code repository into accepting an update, which if incorporated downstream that code snippet would secretly backdoor all CoPay wallets. https://arstechnica.com/information-technology/2018/11/hacker-backdoors-widely-used-open-source-software-to-steal-bitcoin/ (5/8)
Tue Jun 16 18:11:42 +0000 2020
The SYSTEMIC NETWORK ATTACK is our next adversary in the “Loss by Crime, Theft” category: https://twitter.com/christophera/status/1272955016710549504?s=21
Tue Jun 16 18:12:40 +0000 2020
RT @veriphibtc: A little reminder for you all! 🤓
Our director of Marketing @CepnikMaciej will be giving a presentation on Cold-Storage lat…
Tue Jun 16 19:49:41 +0000 2020
RT @westfall104: The #T3Network just published a paper on “Applying SSI Principles to ILRs” to empower learners and workers with their data…
Wed Jun 17 01:27:12 +0000 2020
I need to give credit to @hackylawyER, who I also commended to this Wyoming Legislative Select Committee to invite to further discussions. Wyoming is in a great place to kick off a great start & has a real desire for fundamental enabling legislation for decentralized identity. https://twitter.com/vinayvasanji/status/1273016508982018048
Wed Jun 17 01:41:41 +0000 2020
🤔Some good stuff here, but feels like a bigger problem: “Protects people’s privacy during contact tracing…requires certain privacy measures be implemented in contact tracing applications.” https://www.nysenate.gov/legislation/bills/2019/S8327
Wed Jun 17 02:06:19 +0000 2020
RT @michael_nielsen: Whoo! Excited to see @nayafia’s book “Working in Public: The Making & Maintenance of Open Source Software” now for pre…
Wed Jun 17 17:52:13 +0000 2020
#SmartCustody Adversary — Casual Physical Theft:
Imagine: a robber enters your home and steals the safe containing your Ledger. It wasn’t their goal, and they might have no idea what to do with it. But you don’t have access to your Ledger any more either. (1/8)
Wed Jun 17 21:15:08 +0000 2020
Obviously, you minimize the threat of this adversary by having redundant copies of your keys, with the ability to restore your funds so that one CASUAL PHYSICAL THEFT doesn’t cost you everything. (5/8)
Wed Jun 17 21:15:09 +0000 2020
Even with theft, one of the most likely consequences is loss of your funds, not their acquisition by someone else! (4/8)
Wed Jun 17 21:15:09 +0000 2020
The motivation here? “I just want an easy score, and your house looks like it. … if you got a safe, I’ll try to take that too. I have no idea what I’ll do with it, or with the contents if I can get it open. If I see some weird numbers, I’ll probably just trash them.” (3/8)
Wed Jun 17 21:15:09 +0000 2020
This is what I call CASUAL PHYSICAL THEFT, one of the adversaries in #SmartCustody. Like the rest of the adversaries, it’s a specific threat that you can assess for your personal situation based on its anthropomorphized motivations. (2/8)
Wed Jun 17 21:15:09 +0000 2020
This also means that you need to be aware that a theft has happened. Consider checking periodically all the locations you store your keys in any form. I even check my safe deposit boxes twice a year. (7/8)
Wed Jun 17 21:15:10 +0000 2020
But you also need to be proactive. If your coins aren’t gone immediately, don’t just assume your thief is a knucklhead who doesn’t know what to do with your Ledger or your metal plates or whatever. Move your funds! (6/8)
Wed Jun 17 21:15:10 +0000 2020
Have your own stories of CASUAL PHYSICAL THEFT impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Wed Jun 17 21:17:24 +0000 2020
CASUAL PHYSICAL THEFT is the next #SmartCustody adversary in the category of “Loss by Crime, Theft”: https://twitter.com/christophera/status/1273363574295937024?s=21
Wed Jun 17 21:18:27 +0000 2020
Replying to @hackylawyER
Why would you think so? I don’t see how based from their questions during the testimony Friday that they have not shown that they are very serious about digital identity. What are you seeing differently? /cc co-chairs of #Wyoming Select Committee: @rothfuss @JaredSOlsen
Wed Jun 17 21:45:34 +0000 2020
Replying to @hackylawyER, @rothfuss, @JaredSOlsen and @hackylawyER
you are a leader in this area, in particular about moving beyond property law, thinking deeply & critically. I (and we) will miss your voice if you find you can’t participate in these discussions. If not you, who else? I believe Wyoming is ready to make a diference.
Wed Jun 17 21:49:27 +0000 2020
Replying to @hackylawyER, @rothfuss and @JaredSOlsen
For instance, in the testimony before mine from Google, you can tell the legislators are concerned about portability. You & @Emily_Fry_ wrote about that being a key good place to start. I think @GiuliettaMarani in the EU might agree. Wyoming can become US leader on this topic.
Wed Jun 17 22:16:58 +0000 2020
Replying to @hackylawyER, @rothfuss, @JaredSOlsen, @Emily_Fry_ and @GiuliettaMarani
How might we help Wyoming express the requirement for portability? What are the key points? We began a discussion on revising the #SSI Principle 6 on #Portability at https://github.com/WebOfTrustInfo/self-sovereign-identity/issues/13 — how can we turn this into legislation as a principle and not be too prescriptive?
Wed Jun 17 22:22:47 +0000 2020
Replying to @hackylawyER, @rothfuss, @JaredSOlsen, @Emily_Fry_, @GiuliettaMarani and @hackylawyER
— I shared with the #Wyoming Select Committee your article with @dazzagreenwood https://www.linkedin.com/pulse/do-we-really-want-sell-ourselves-risks-property-law-data-greenwood/ — however, you may feel this is now dated. What other links to help them understand the issue do you feel are essential?
Wed Jun 17 22:28:10 +0000 2020
RT @hackylawyER: @ChristopherA @rothfuss @JaredSOlsen @Emily_Fry_ @GiuliettaMarani @dazzagreenwood Thanks, I’d recommend this recent piece…
Thu Jun 18 02:19:03 +0000 2020
So as far as I can tell, #Wyoming has no specific law around digital identity. They have a number of adjacent laws around real-world identity and are very protective about personal privacy—much more so than other states. But otherwise they are tabula rasa. Where would you start?
Thu Jun 18 02:23:50 +0000 2020
IANAL, but is a good issue to start with that the existence of a digital identity, or the lack of (or problems with), should in no way be allowed reduce the rights of the individual person? I shared the India & Kenya examples of denial of services due to lack of digital identity.
Thu Jun 18 02:29:12 +0000 2020
What other fundamental principles, acknowledgement of human rights, solid modern definitions, and privacy issues are a good base line for #Wyoming, given a general absence of them or inheriting them from US Federal Law or other laws like UCC? Seeking powerful low-hanging fruit.
Thu Jun 18 02:32:49 +0000 2020
Replying to @alistairmilne
I would really like to add the full story of this to the next edition of the #SmartCustody book.
Thu Jun 18 03:12:14 +0000 2020
Now that W3C DID (Decentralized Identifier) Working Group is working on their next draft toward a final spec, the official register of different DIDs methods that have been added to date has been moved its new home: https://www.w3.org/TR/did-spec-registries/#did-methods
Thu Jun 18 05:04:08 +0000 2020
This is a situation where someone knows that you have digital assets, knows where those assets are held, and it prepared to physically break in to retrieve them. It’s a bit terrifying. (2/8)
Thu Jun 18 17:37:33 +0000 2020
Yesterday I wrote about the #SmartCustody adversary Casual Physical Theft, where a robber accidentally (or at least non-purposefully) takes your cryptocurrency. SOPHISTICATED PHYSICAL THEFT, where they know what they’re after, is much more dangerous. (1/8)
Thu Jun 18 17:37:33 +0000 2020
This is another situation where the best protection might be anonymity. If no one knows about your cryptocurrency or other digital assets, then no one will make a special effort to steal it. (5/8)
Thu Jun 18 17:37:34 +0000 2020
Is someone likely to break into your house, disguise themself as a service person, or place nearby listening devices? Probably not. But compare it to your profile and vulnerability. How well known is your wealth, how secure is it, and how large is it? (4/8)
Thu Jun 18 17:37:34 +0000 2020
It’s also somewhat unlikely. And #SmartCustody is all about bloodlessly considering threats and seeing which ones are actually adversaries that you have to face. (3/8)
Thu Jun 18 17:37:34 +0000 2020
Have your own stories of SOPHISTICATED PHYSICAL THEFT impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Thu Jun 18 17:37:35 +0000 2020
It is a balancing act—if you try to protect against all possible adversaries at once, you will become paralyzed. Instead, take a look at each seperately. SOPHISTICATED PHYSICAL THEFT is scary, but unless you are a public figure other adversaries are likely a greater threat.(7/8)
Thu Jun 18 17:37:35 +0000 2020
You can take steps to increase your privacy. For instance, see @lopp’s article reflecting on privacy after a SWAT incident https://blog.lopp.net/reflections-upon-a-swatting/ that resulted in his extensive advice at https://blog.lopp.net/modest-privacy-protection-proposal/ (6/8)
Thu Jun 18 17:37:35 +0000 2020
Our next #SmartCustody adversary in the category “Loss by Crime, Theft” is SOPHISTICATED PHYSICAL THEFT: https://twitter.com/christophera/status/1273671203832492033?s=21
Thu Jun 18 17:39:08 +0000 2020
Replying to @veriphibtc
I’ve also been doing a tweetstorm daily this month on each of the #SmartCustody adversaries, starting at: https://twitter.com/ChristopherA/status/1267560484611387392?s=20 https://twitter.com/ChristopherA/status/1267560484611387392
Thu Jun 18 19:03:21 +0000 2020
Replying to @BitcoinQ_A
You should also look at Bitcoin Standup MacOS https://github.com/BlockchainCommons/Bitcoin-Standup-MacOS, a one-click installer that also installs Tor v3 services & QuickConnect QR to connect to a remote wallet (some of your other nodes do as well, should add a column!). We have linux scripts also available.
Thu Jun 18 19:08:54 +0000 2020
The co-chairs @rothfuss @JaredSOlsen of #Wyoming Select Committee on Blockchain, Financial Technology and Digital Innovation Technology said during the last meeting they were interested getting help. I recommended you. What do you need next?
Thu Jun 18 23:34:46 +0000 2020
Done. Your invite from the Select Committee’s co-chairs should be in your inbox.
Now to find a select few more people that can help create a legal model for decentralized digital identity in #Wyoming that other states can learn from. Any suggestions on who else?
Fri Jun 19 05:03:06 +0000 2020
The underlying algorithms and protocols for Charter will be open source & will use open standards processes, and thus not owned by any single company. Instead they will be under the control of individuals and the groups that people create and join.
Fri Jun 19 06:53:35 +0000 2020
“Charter reimagines social media to recover its initial promise, with new safeguards so that no single vendor one can steal it away.” I’m co-author of the IETF TLS 1.0 standard, and co-author of the emerging W3C Decentralized Identifier standard. I care deeply about this.
Fri Jun 19 06:53:35 +0000 2020
Blockchain Commons @BlockchainComns is collaborating with Bitmark @BitmarkInc in their efforts to create Charter, a new open social-media architecture for the internet. https://www.prnewswire.com/news-releases/blockchain-commons-and-bitmark-introduce-charter-a-new-social-media-architecture-301078535.html
Fri Jun 19 06:53:35 +0000 2020
We look forward to continuing to work with Bitmark as the Charter open architecture evolves, as well as with other companies who might be interested in this architecture. Join our mailing list http://eepurl.com/gDvBkj
Fri Jun 19 06:53:36 +0000 2020
This is the sort of open infrastructure that is at the heart of our work at Blockchain Commons: Charter will be available for use by many people & many companies all across the internet, each with their own ability to improve or utilize it, and all with no centralized authority.
Fri Jun 19 06:53:36 +0000 2020
We will begin by collaborating with @BitmarkInc on an information lifecycle engagement model (like the previous Joram or Amira models from #RWOT led by @JoeAndrieu) for this decentralized social-media architecture that gives its users both agency & autonomy.
Fri Jun 19 06:53:36 +0000 2020
#SmartCustody Adversary — Social Engineering
The Con Man may be the most dangerous thief in the online world. He’s an adversary who depends on SOCIAL ENGINEERING to trick you into giving up your credentials, and then use them to steal the assets that they were protecting. (1/12)
Fri Jun 19 19:52:26 +0000 2020
This is one of the many adversaries that I talk about in #SmartCustody: threats to your digital assets that I anthropomorphize to help you assess how dangerous they are to you (or not). Then help you balance those actual threats vs. the cost to mitigate them. (2/12)
Fri Jun 19 19:52:28 +0000 2020
There are certainly examples of con men being dangerous to other holders of cryptocurrency, as has been reported in the news over the years. (3/12)
Fri Jun 19 19:52:29 +0000 2020
An attacker spearphished Bitpay and got the CFO to reveal his credentials, which were then used to contact the CEO and convince him to transfer 5,000 Bitcoins. (4/12) https://cointelegraph.com/news/bitpay-hacked-for-over-18-million-in-bitcoins
Fri Jun 19 19:52:30 +0000 2020
The COINHOARDER group used ads with misspelled URLs for exchange sites to trick people into giving up their credentials. (5/12) https://blog.talosintelligence.com/2018/02/coinhoarder.html
Fri Jun 19 19:52:31 +0000 2020
Social engineering can be devastatingly clever. The bottom line is that you should never type in your credentials unless you went to a site in a way that confirmed it’s the real thing or you saw its certificate. (7/12)
Fri Jun 19 19:52:32 +0000 2020
These tricks need not be very technical. My colleague got an email from a partner in China with a new email. That partner also received a new email. The attacker just sat in the middle, carefully forwarding each email until the right moment and changed the crucial address. (6/12)
Fri Jun 19 19:52:32 +0000 2020
Learning to use two-factor authentication (2FA) is also a requirement: it ensures that if someone else gets your credentials, they still can’t get into a site (unless they port your cell phone number, but at least that’s an additional obstacle). (8/12)
Fri Jun 19 19:52:33 +0000 2020
In other words, we sort of need to be protected from ourselves, because it’s possible for any of us to fall to a SOCIAL ENGINEERING scam at some point! (10/12)
Fri Jun 19 19:52:34 +0000 2020
I personally always request that cryptocurrency address to me to pay for for significant amounts be sent via two mechanisms, with at least one secure such as Signal. Even larger amounts I might confirm address by voice. (9/12)
Fri Jun 19 19:52:34 +0000 2020
LIke all the #SmartCustody adversaries in this series, you review your risks seperately. SOCIAL ENGINEERING is one that stood out in my own review of threats as being under-represented in my own tactics, and it was relatively cheap for me to strengthen. (11/12)
Fri Jun 19 19:52:35 +0000 2020
Have your own stories of SOCIAL ENGINEERING impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (12/12)
Fri Jun 19 19:52:36 +0000 2020
Today’s #SmartCustody adversary in the category “Loss by Crime, Theft” is SOCIAL ENGINEERING https://twitter.com/ChristopherA/status/1274067538637291520?s=20
Fri Jun 19 19:56:35 +0000 2020
RT @johnabbe: Thx to @shareable (and every author/publisher who has helped me learn from #elinorostrom), this is new to me & yet unsurprisi…
Sat Jun 20 00:05:57 +0000 2020
An anonymous burner phone is useful for other legal purposes besides protests, for instance to publish an advocacy blog, document & report civil and human rights abuses, or inform press about illegal activities of parties with financial or political power. Asymmetric power. https://twitter.com/theintercept/status/1274103545458036737
Sat Jun 20 00:18:01 +0000 2020
RT @mgsiegler: We’re getting too far into the weeds with all this. It seems pretty simple at a higher level: App Store rules and policies w…
Sat Jun 20 02:53:31 +0000 2020
Replying to @KLoaec and @rootzoll
There are other things beside funding needed for Tor to exist. Our own organization @BlockchainComns funds an exit node, and we hope to fund more. I urge the entire community to support these commons, both @torproject directly, and common pool resources like bandwidth, etc.
Sat Jun 20 04:49:32 +0000 2020
There are other things beside funding needed for Tor to exist. Our own organization @BlockchainComns funds an exit node, and we hope to fund more. I urge the entire community to support these commons, both @torproject directly, and common pool resources like bandwidth, etc. https://twitter.com/torproject/status/1274040299363299328
Sat Jun 20 04:50:13 +0000 2020
See also “We wanted to do something to help people that have been affected [by COVID-19] and people that are out of work,” Fournier described. “So we fired up the same exact press from the late 1800s, and we have printed off wooden money once again.” https://mynorthwest.com/1951334/tenino-washington-printing-wooden-money/
Sun Jun 21 02:25:20 +0000 2020
I’ve written before about local currencies. They can be a powerful local tool: “he’d watched the pandemic rake local businesses…‘How do we directly help families and individuals?’ And then it hit him: ‘Why not start our own currency?’” https://thehustle.co/covid19-local-currency-tenino-washington/#:~:text=Whynotjustgiveresidents,moneystaysinthecity
Sun Jun 21 02:25:20 +0000 2020
Support in our @FullyNoded 2 iOS bitcoin wallet for bitcoin multisig transactions that leverage interoperability with multiple wallets from multiple companies is really evolving right now. 4 now! You should ask (no demand!) that your wallet vendors demonstrate interoperability. https://twitter.com/FullyNoded/status/1274573750298533890
Sun Jun 21 06:54:43 +0000 2020
#SmartCustody Adversary — Supply-Chain Attack
SUPPLY-CHAIN ATTACK may be one of the least obvious adversaries that we cover in #SmartCustody. But that makes it particularly important, because you may not be aware of its possibilities. (1/11)
Mon Jun 22 19:09:50 +0000 2020
The problem with a supply-chain attack is that it can make you very paranoid. Anyone could be an attacker, from a worker in a factory to a reseller to your postal carrier, to the eponymous “evil maid”. (6/11) https://en.wikipedia.org/wiki/Evil_maid_attackevil
Mon Jun 22 19:09:51 +0000 2020
And we’ve always wondered about the “factory-sealed” computer used to supposedly prove the identity of Satoshi Nakamoto, especially since it was delivered by that person’s assistant. That’s a prime example of an opportunity for an attack of this sort. (5/11)
Mon Jun 22 19:09:51 +0000 2020
Is this hypothetical? Maybe. Nonetheless it’s been highlighted by security analysts as a potential threat. (4/11) https://threatpost.com/cryptocurrency-wallet-hacks-spark-dustup/140445/
Mon Jun 22 19:09:51 +0000 2020
Here’s how we explain the motivation: “I’m the slyest of thieves because I worm my way into your life without your even knowing. … My goal is to mess with your devices so that I can mess with your digital assets, and you may never figure out how I did it!” (3/11)
Mon Jun 22 19:09:51 +0000 2020
In a Supply-Chain Attack, someone corrupts your computer, your hardware wallet, or your other cryptocurrency hardware before you ever see it. (2/11)
Mon Jun 22 19:09:51 +0000 2020
On my most critical personal devices, I enclose them in tamper-evident bags, or add a tamper-evident seal, or just some add glitter polish and take a photo. I check these twice a year. I personally feel it is unlikely to happen to me, but it is so cheap to protect against. (9/11)
Mon Jun 22 19:09:52 +0000 2020
Of course, this is really practical when in fact the known incidents of SUPPLY-CHAIN ATTACK are very few. However, whether you purchase directly from a manufacturer or not, seek hardware that is sealed and offers some measures of tamper-resistance. And re-check regularly! (8/11)
Mon Jun 22 19:09:52 +0000 2020
The ideal solution? Buy from manufacturers directly. If you can, do so in person by going to their warehouse! I bough my first @Ledger hardwared from their store in Paris. Every person you can cut out of the supply-chain is one less vector of attack. (7/11)
Mon Jun 22 19:09:52 +0000 2020
Have your own stories of SUPPLY-CHAIN ATTACK impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (10/11)
Mon Jun 22 19:09:53 +0000 2020
And this at last of the #SmartCustody category “Loss by Crime, Theft” by networked, personal or systemic, institutional or internal, through the supply chain or through social engineering. You need to consider them all in your risk analysis! (9/11)
Mon Jun 22 19:09:53 +0000 2020
Our last #SmartCustody adversary in the category “Loss by Crime, Theft” is SUPPLY-CHAIN THEFT: https://twitter.com/christophera/status/1275143980389265408?s=21
Mon Jun 22 19:11:09 +0000 2020
RT @RhysLindmark: Confused by paradigms? Me too! Hopefully my most recent article can help.
Paradigms are the combination of epistemology,…
Tue Jun 23 17:00:49 +0000 2020
#SmartCustody adversary category “Loss by Crime, Other”
I’ve spent a lot of time on the category of THEFT, but it’s not the only sort of crime that can impact your cryptocurrency holdings. There’s a whole other category, which I wittily called LOSS BY CRIME, OTHER. (1/10)
Tue Jun 23 21:05:44 +0000 2020
I place four different adversaries in this #SmartCustody category: Blackmail, Coercion, Terrorism, and Non-Financially-Motivated Attackers. The unifying theme is that they’re trying to take your digital assets by illegal means. (2/10)
Tue Jun 23 21:05:45 +0000 2020
Yes, some of these OTHER adversaries are still technically THEFT, but they tend to be risks with bigger consequences than just losing property. You could lose your reputation or your life! (3/10)
Tue Jun 23 21:05:46 +0000 2020
These can be darker crimes, but they’re also somewhat less likely. Are you really likely to be kidnapped? (A form of coercion) Could you even be blackmailed? I suspect mostly not. (5/10)
Tue Jun 23 21:05:47 +0000 2020
I iconify these criminals as a man with a overcoat and a shotgun. That’s pretty scary too. (4/10)
Tue Jun 23 21:05:47 +0000 2020
But of course the point of #SmartCustody is to anthropomorphize adversaries so that you understand them better, and to use that as the foundation for determining whether they’re threats to you (personally) or not. (6/10)
Tue Jun 23 21:05:48 +0000 2020
We might viscerally fear being kidnapped for our Bitcoins (or that man in the covercoat), but by modeling the risk we can determine if it’s actually likely. If it isn’t, it may be better concentrate our efforts on another risk. (7/10)
Tue Jun 23 21:05:49 +0000 2020
The motive of these adversaries is mixed. Like other crimes, greed is a big factor, but the non-fincially-motivated attackers could be hackers, hactivists, or just bored kids. (8/10)
Tue Jun 23 21:05:50 +0000 2020
Any thoughts on these OTHER crimes? Any specific adversaries that I missed? Let us know! And please consider supporting the book this is drawn from, #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (10/10)
Tue Jun 23 21:05:51 +0000 2020
Because of that variation in motive, each of these OTHER crimes have to be approached somewhat differently than we did for the motives of the more pure THEFT crimes. (9/10)
Tue Jun 23 21:05:51 +0000 2020
Our next category of #SmartCustody adversaries is “Loss by Crime, Other”: https://twitter.com/christophera/status/1275535534866104322?s=21
Tue Jun 23 21:07:33 +0000 2020
RT @AntoineVedeilhe: THREAD. This morning I took a flight to Chengdu (2000km away from Shanghai) to interview Fan Xiao, a respected Chinese…
Wed Jun 24 06:34:44 +0000 2020
I wrote this two years ago today. Can we do this yet with Lightning Networks’ LSATs? I’d like to start leveraging content addressable objects, but I don’t want rest of FileCoin stack. @WayneVaughan @BuckPerley @roasbeef @alexbosworth @gugol https://twitter.com/ChristopherA/status/1010994379434016775
Wed Jun 24 19:00:32 +0000 2020
RT @start9labs: Announcing Capacitor-Tor!
An open source plugin for hybrid mobile apps built with @Ionicframework that enables developers…
Wed Jun 24 19:02:40 +0000 2020
#SmartCustody Adversary — Blackmail
BLACKMAIL sounds like a somewhat unlikely crime for the average person, but in actuality it’s a very real adversary, which is why we talk about in #SmartCustody. (1/10)
Wed Jun 24 21:21:00 +0000 2020
How real is it? You or your employer has probably received one or more BLACKMAIL threats demanding payment in bitcoins. Granted, bitcoins are just a preferred method of pseudonymous payment, but if you have cryptocurrency, you’re that much more vulnerable. (2/10)
Wed Jun 24 21:21:26 +0000 2020
It’s even appeared in TV shows, such as an episode of The Good Wife where the firm’s computers are encrypted and a ransom is demanded. (3/10) https://computertroubleshooters.co.uk/tonbridge/commentary/the-good-wife-attacked-by-ransomware/
Wed Jun 24 21:21:29 +0000 2020
One of the prime sorts of BLACKMAIL is cryptocurrency ransomware, where files will only be decrypted if a bitcoin fee is paid. (4/10) https://nakedsecurity.sophos.com/2019/02/14/inside-a-gandcrab-targeted-ransomware-attack-on-a-hospital/
Wed Jun 24 21:21:40 +0000 2020
Sextortion is another form of BLACKMAIL. It tends to be based on pure bluff, that an attacker took control of the victim’s computer camera. (5/10) https://www.eff.org/deeplinks/2018/07/sextortion-scam-what-do-if-you-get-latest-phishing-spam-demanding-bitcoin
Wed Jun 24 21:21:44 +0000 2020
Obviously, a specific attack could be more precisely targeted, and it could be based on control of information or a possession that you care about more personally. (6/10)
Wed Jun 24 21:21:47 +0000 2020
A challenge that the BLACKMAIL doesn’t even have to be true. Going back to the day’s of Cardinal Richelieu’s “six lines” and today’s #FalseNews and #MeToo facts are unfortunately optional. (7/10)
Wed Jun 24 21:21:50 +0000 2020
How to avoid BLACKMAIL? Well, the problem is that they already have something of value, so sometimes you have to decide between losing it and losing your digital assets. (8/10)
Wed Jun 24 21:21:52 +0000 2020
Not necessarily a solution, but having someone you trust in a multisig who can more objectively advise you and keep you from being too rushed or doing something stupid may help. (9/10)
Wed Jun 24 21:21:56 +0000 2020
Have your own stories of BLACKMAIL impacting digital assets? Any other ways to mitigate against this adversary? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/
Wed Jun 24 21:21:58 +0000 2020
Our first #SmartCustody adversary in the category of “Loss by Crime, Other” is BLACKMAIL: https://twitter.com/christophera/status/1275901766081507329?s=21
Wed Jun 24 21:26:35 +0000 2020
Replying to @BuckPerley, @cycryptr, @WayneVaughan, @roasbeef, @alexbosworth and @gugol
A particular challenge is that I don’t want to incentivize availability back to me, but instead I want the data available broadly on the network. I don’t want the data back, I want my associates to be able to get it when I’m not available to offer it, for instance offline.
Wed Jun 24 23:13:37 +0000 2020
Open source & Ostrom “they take the first of her design principles, clear boundaries and memberships, and turn it inside out…a Hobbesian state…where the rules about who can appropriate are no rules at all. The ‘membership’ that can exploit is everyone” https://writing.kemitchell.com/2020/04/20/Common-Pool-Pushovers.html
Thu Jun 25 01:47:57 +0000 2020
The author continues with this list of alternative views on open source software as “antidotes” to the hype. Basic summary is that open source has complications that are “omitted from the popular narrative”. https://writing.kemitchell.com/lists/Antidote.html
Thu Jun 25 01:52:42 +0000 2020
Replying to @infinite_mao
I’m just not quite sure what this is? A zine? A collection of poetry? Game play? A game?
Thu Jun 25 07:31:09 +0000 2020
Here’s our take on the motivation: “I know you have cryptocurrency. Well, I’ve got power in the real world. … I want to get what you have, and I’m going to force you to give it to me by any means necessary.” (2/8)
Thu Jun 25 18:18:26 +0000 2020
#SmartCustody Adversary — Coercion
COERCION? Ugh. It’s a terrible adversary that can threaten the #SmartCustody of your digital assets. Someone is demanding those assets based on a threat to you, your family, or your friends. (1/8)
Thu Jun 25 18:18:26 +0000 2020
How real is this threat in the first world? It’s limited. Though of course that’s the exact sort of assement you need to make in #SmartCustody, when you look at the motivations of anthropomorphized adversaries, and see how they impact you. (3/8)
Thu Jun 25 18:18:27 +0000 2020
And there is at least one strong possibility for COERCION in first-world countries: SWATting, where the police are sent in to possibly kill you based on fake 911 calls. This isn’t isn’t only a #BLM problem.(4/8)
Thu Jun 25 18:18:28 +0000 2020
Elsewhere, kidnapping can be a real problem, in which case you’re being coerced to give up your digital assets due to threats to yourself or your family. (5/8)
Thu Jun 25 18:18:29 +0000 2020
One gamble is to have two sets of funds, those which you are able to give away easily based on a threat, the second you genuinely can’t give up due to a multisig or timelock. But sometimes it’s a question or your money or your life: try not to get into a position like that .(7/8)
Thu Jun 25 18:18:30 +0000 2020
There’s a list of real-world COERCION of this sort that includes SWATting, kidnapping, and torture. (6/8) https://github.com/jlopp/physical-bitcoin-attacks
Thu Jun 25 18:18:30 +0000 2020
Have your own stories of COERCION impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Thu Jun 25 18:18:31 +0000 2020
The next #SmartCustody adversary in the category of “Loss by Crime, Other” is COERCION: https://twitter.com/christophera/status/1276218207909511169?s=21
Thu Jun 25 18:19:43 +0000 2020
#SmartCustody Adversary — Non-Financially Motivated Attackers
The most far-flung crime in my list of adversaries is likely the NON-FINANCIALLY MOTIVATED ATTACKERS: people who are denying you access to your cryptocurrency even though they don’t care about the money. (1/9)
Fri Jun 26 17:32:53 +0000 2020
What might these non-financial motivations be? The attacker might want to expose something, they might want to deny your money to you, or they might want to use your funds as a tool to get something else. We can’t always know their motivations. (2/9)
Fri Jun 26 17:32:55 +0000 2020
The creators of Malware are prime examples of non-financially motivated attackers. They just want to demonstrate their power. They want to break stuff! (4/9)
Fri Jun 26 17:32:56 +0000 2020
But here’s how we try and summarize it: “I don’t care about your money, but I’ll still going to mess with you. … The key is: I know who you are, I know what you have, and I want to use that knowledge as a lever for my own purposes.” (3/9)
Fri Jun 26 17:32:56 +0000 2020
The goal of leveraging #SmartCustody adversaries is to understand their motives so that we can both assess and avoid them. Yet that’s really hard to do with NON-FINANCIALLY MOTIVATED ATTACKERS. (6/9)
Fri Jun 26 17:32:57 +0000 2020
An attacker of the Parity wallet said that his attack was accidental, caused by curiosity. Was it? We don’t know. (5/9) https://medium.com/chain-cloud-company-blog/parity-multisig-hack-again-b46771eaa838
Fri Jun 26 17:32:57 +0000 2020
Most NON-FINANCIALLY MOTIVATED ATTACKERS are directly targeting you. This requires you to have good digital hygeine. Protect your not only your keys, but also protect your identity and your other credentials. Make it hard for anyone to identify you and deny you access. (8/9)
Fri Jun 26 17:32:58 +0000 2020
So how do you protect your digital assets against NON-FINANCIALLY MOTIVATED ATTACKERS? The key is their focus is denial of access, not theft. So where are the places, short of theft, that they can lock you out or delay you? Establish redundancies and alternative paths. (7/9)
Fri Jun 26 17:32:58 +0000 2020
Have your own stories of non-financial motivations impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (9/9)
Fri Jun 26 17:32:59 +0000 2020
Another #SmartCustody adversary in the category of “Loss by Crime, Other” is the NON-FINANCIALLY MOTIVATED ATTACKER: https://twitter.com/christophera/status/1276569133165903872?s=21
Fri Jun 26 17:35:35 +0000 2020
Replying to @bobhilt
There are definitely a number of approaches to avoiding a complete loss. But care must be taken to avoid too much PROCESS FATIGUE (a future adversary) else you increase your vulnerability. You can balance the risk.
Sat Jun 27 01:09:51 +0000 2020
RT @BtcpayServer: What’s your favorite feature of the v 1.0.5.0?
https://twitter.com/BtcpayServer/status/1276526312279113730?s=20
Sat Jun 27 01:36:06 +0000 2020
We are in that point in our beta testing of the @FullyNoded 2 multisign wallet where we are moving from bitcoin testnet to testing on mainnet, where real bitcoin is at risk. We are seeking a few private beta testers to help us move FN2 to the next level! https://twitter.com/FullyNoded/status/1276780728101924864
Sun Jun 28 01:59:43 +0000 2020
RT @torproject: Wikipedia has tried to block Tor users since 2007, alleging vandalism, spam, and abuse. New research tells a different stor…
Sun Jun 28 05:22:22 +0000 2020
I’m feeling this to be particularly true today. I didn’t predict the impact of COVID-19 on my plans going forward, but my plans from the future to today are still valid — how do we together make better decisions to collaborate & thrive to save the world? It helps my priorities. https://twitter.com/moskovich/status/846243656239661056
Mon Jun 29 20:49:46 +0000 2020
#SmartCustody Adversary — Terrorist / Mob
Here’s one final criminal adversary from #SmartCustody that might affect your digital holdings: TERRORISM or the MOB. (1/9)
Mon Jun 29 21:07:51 +0000 2020
So I’ll start with repeat what I said then: consider if your money is really worth more than your life. (4/8)
Mon Jun 29 21:07:52 +0000 2020
They’re a special case because they’re much more likely to carry through on their threats, because that’s how they operate. They know that fear breeds compliance, and fear derives from threats actually carried out. (3/9)
Mon Jun 29 21:07:52 +0000 2020
It’s a special case of the Coercion adversary that I discussed a few days ago https://twitter.com/ChristopherA/status/1276218207909511169, but now it’s an organization that’s targeting you, whether it be organized crime or a terrorist group. (2/9) https://twitter.com/ChristopherA/status/1276218207909511169
Mon Jun 29 21:07:52 +0000 2020
Have your own stories of TERRORISM or the MOB impacting digital assets? Your own solutions? Let us know! And please consider supporting #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (9/9)
Mon Jun 29 21:07:53 +0000 2020
And that’s the last of my “other” criminal adversaries, which covered Blackmail, Coercion, Non-Financially Motivated Attackers, and Terrorism/Mob. These may be less likely to affect you, but #SmartCustody is all about figuring out your odds before placing bets or investing. (8/9)
Mon Jun 29 21:07:53 +0000 2020
There are no easy answers to addressing this adversary, but a key may be in their strategy, which is to instill fear, not only in you, but in your community. Find support in your community to mitigate that fear and its impact. Also support your community! (7/9)
Mon Jun 29 21:07:53 +0000 2020
The opposite strategy is to be recognized as a public-figure such that civil society & governments will help defend you. But that option is limited and not available to everyone. I’m sure @Snowden worries as almost as much about TERRORIST / MOB as he does about governments. (6/9)
Mon Jun 29 21:07:53 +0000 2020
Practice anonymity of your funds, because an organized criminal organization is only going to attack you if they know they have something to gain. (5/9)
Mon Jun 29 21:07:53 +0000 2020
Our last #SmartCustody adversary in the category of “Loss by Crime, Other” is TERRORISM / MOB: https://twitter.com/christophera/status/1277710396778885120?s=21
Mon Jun 29 21:08:48 +0000 2020
Replying to @clay_space, @sthenc, @jonst0kes, @SwanBitcoin and @kanzure
If your interested, the above is an excerpt from the full #SmartCustody Book http://bit.ly/SmartCustodyBookV101, free due to the generosity of our Sponsors. We are seeking support for v2 of the book which will include multisig scenarios.
Tue Jun 30 03:12:58 +0000 2020
Replying to @clay_space, @sthenc, @jonst0kes, @SwanBitcoin and @kanzure
I’m also recapping this month on Twitter the digital asset adversaries that we cover in the book. One a day starting at https://twitter.com/christophera/status/1267560481855639553?s=21
Tue Jun 30 03:14:26 +0000 2020
Replying to @lumpysnake
In a reply to the original tweet (128 character day) I credit the orgininator. But your URL is more current. Thanks!
Tue Jun 30 07:15:02 +0000 2020
I’m not surprised—Pandemic is a true social cooperative game, and health care today is socially cooperative work. As a game it depersonalizes the topic just a bit, allowing you to focus on solving the problems and not needing to empathize with your patients, only your co-workers. https://twitter.com/mattleacock/status/1277714286702256133
Tue Jun 30 20:08:00 +0000 2020
LOSS BY GOVERNMENT is one of the most interesting categories of adversaries in #SmartCustody because I think it’s something that a lot of cryptocurrency holders are afraid of, but I also think it contains adversaries that aren’t necessarily going to impact most people. (1/8)
Tue Jun 30 20:12:01 +0000 2020
But that’s not necessarily the state of things today, and that’s what #SmartCustody is all about: approaching potential adversaries without emotion, seeing what they want, and assessing whether that’s a danger to your own holdings. (5/8)
Tue Jun 30 20:12:02 +0000 2020
That’s probably what causes me to envision this category as a man in black wearing sunglasses, ready to take you away in an unmarked van. (4/8)
Tue Jun 30 20:12:02 +0000 2020
This hasn’t been helped by some governments’ prejudicial attitudes toward cryptocurrency in the early years of Bitcoin, and waffling support back & forth today. (3/8)
Tue Jun 30 20:12:02 +0000 2020
The concern is understandable. The beliefs of centralized government and those of advocates of decentralized services can run straight against each other. (2/8)
Tue Jun 30 20:12:02 +0000 2020
Any thoughts on Loss by Government? Any specific adversaries that I missed? Let us know! And please consider supporting the book this series is drawn from, #SmartCustody. We’re working on V2, with multi-sigs and other expansions: https://smartcustody.btcpay.blockchaincommons.com/ (8/8)
Tue Jun 30 20:12:03 +0000 2020
There are just two adversaries in this category: Legal Forfeiture and the danger of the uncontrolled Nation-State Actor. (7/8)
Tue Jun 30 20:12:03 +0000 2020
So you have to ask: am I in a state likely to take my holdings by illegal means? Am I in danger of losing my holdings to legal means? Would it be just if that happened? The answers to those questions helps to define the danger of these adversaries. (6/8)
Tue Jun 30 20:12:03 +0000 2020
Our next category of #SmartCustody adversaries is “Loss by Government”: https://twitter.com/christophera/status/1278058733868773376?s=21
Tue Jun 30 20:12:58 +0000 2020
RT @FullyNoded: Manually importing things into your node is not fun. I worked with bitcoin-cli non stop the last two years and i can not ge…